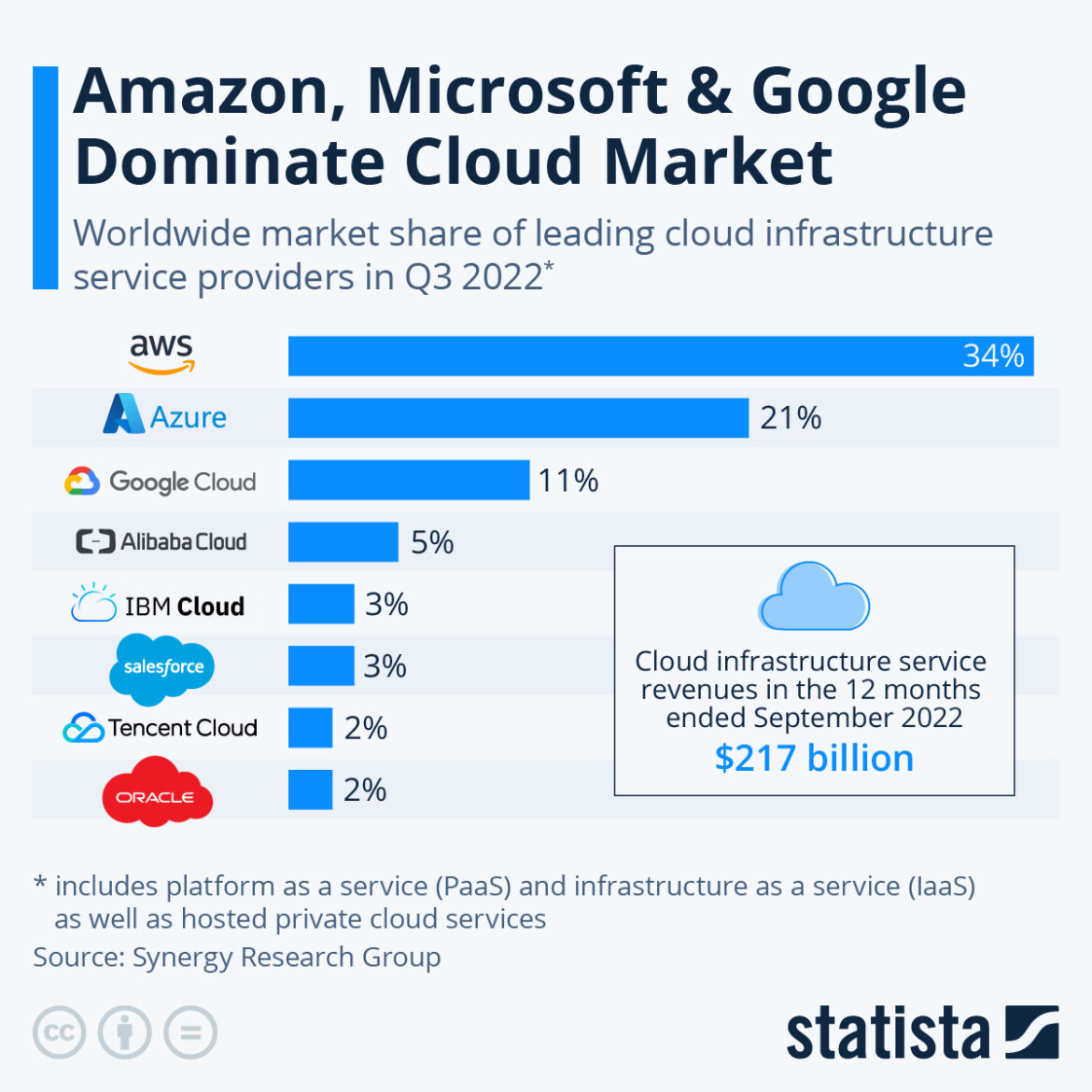
Cloud adoption by businesses continues to grow. During the COVID-19 pandemic the use of public and private cloud services increased due to the need to shift to remote work environments. In 2023 many companies seeking to reduce IT costs are also turning to the cloud. Cloud adoption provides numerous benefits but also introduces security risks. It is important for businesses to recognize these risks and the security responsibilities they have when using cloud environments. Cloud service providers (CSP) typically engage in a shared responsibility model with their customers. The shared responsibility model states that cloud customers are responsible for the security of their data IN the cloud, and the CSP is responsible for security OF the cloud. Many cloud vendors are now providing more services to assist their customers secure data in the cloud. According to statista, AWS represents 34% of the global cloud market, larger than the next two largest providers, Azure and Google Cloud, combined. Below are 6 common cloud security risks and their mitigation solutions that include AWS tools.
1) Misconfiguration
Misconfiguration of cloud environments continues to be a major security issue. Cloud environments are designed to enable data sharing, but if the proper controls are not in place this can lead to accidental data disclosure. Many businesses also use multiple cloud vendors, which can add to the complexity of implementing vendor-specific controls and settings. Example misconfigurations include: unrestricted inbound or outbound ports, improper credential management and unrestricted data storage access. A common example is AWS S3 buckets with default public access settings.
Misconfiguration Solutions: Double check settings for cloud environments to ensure that each vendor’s default settings and/or best practices are in place. Review cloud services to ensure there are not forgotten services and implement vendor tools. AWS tools: AWS Config and AWS Control Tower
2) Unauthorized Access
Cloud environments are designed to be publicly accessible but this also opens up services to unauthorized access.
Unauthorized Access Solutions: Ensure proper security settings and include network segmentation, security zones and firewalls. Separate business environments with different cloud accounts and implement the principle of least-privilege permissions. Enforce strong employee passwords and use MFA. This minimizes the likelihood and possible damage from unauthorized access. AWS tool: AWS IAM Access Analyzer
3) Insecure APIs
APIs help customers customize their use of cloud services but also opens up the potential for Denial of Service, Man in the Middle and brute force attacks.
Insecure API Solutions: Conduct targeted vulnerability audits and testing of APIs. Follow vendor documentation on how to properly use APIs. AWS tool: AWS CloudTrail and AWS API Gateway
4) Lack of Visibility
“Shadow IT” or the improper use of cloud resources either intentionally or unintentionally by employees is a common issue. A lack of visibility of cloud usage prevents businesses from properly checking for these issues. The lack of visibility of cloud environment can also lead to data loss or disclosure.
Visibility Solutions: CSPs typically provide security audits that can provide a review of cloud usage and access. CSPs provide security tools that can alert customers for anomalous and irregular actions in cloud environments. AWS tool: AWS CloudTrail
5) Data Breach or Disclosure
Data breaches are a common concern in cloud environments. Data breaches often occur through phishing attacks. Data disclosure can also be accidental due to publicly accessible databases and link-based data sharing.
Data Protection Solutions: MFA can help protect against phishing attacks. Single passwords for multiple accounts should be prohibited. Implement IAM and password policies. Review publicly accessible databases and encryption strength and storage of keys. AWS tools: AWS IAM and AWS Key Management Service
6) Denial of Service Attacks
Denial of Service attacks can directly impact business operations and reputation typically by preventing users from accessing programs or websites.
Denial of Service Solutions: Implement firewalls and IDS along with vendor specific protection tools. AWS tool: AWS Shield

