Services
- Home
- Services
BE CONFIDENT. BE SECURED.
Be confident in your systems with tailored security solutions
Secured offers nimble, dedicated, and engaged services that are designed to meet the needs of our clients. Our small but flexible team provides the focus that our clients need and can grow to meet the demands of any project.
Support for your mission
Professional IT & Cyber Ops Solutions
Web Development
Our services include responsive website design, CMS integration, online donation capabilities, membership zones, payment solutions, and comprehensive cybersecurity consulting. Partner with Secured™ to enhance your online presence, engage with your members, and protect your organization from digital threats. Contact us today to take your digital presence to the next level.
Cybersecurity
Secured™ empowers your organization’s infrastructure by working with your existing technology and IT team to manage, supplement, enhance and tighten cybersecurity protocols. This allows you to be able to focus on success and growth and have peace of mind about the security of your network.
Product Engineering
Secured's™ product engineering services can help your organization design, develop, and improve your offerings and related systems. It's a complex process that involves many different disciplines, from market research and product design to software development and manufacturing.
IT Management & Consulting
From inception to on-going support, our team is dedicated to providing a high level of customer service. We work closely with our clients to ensure that your needs are being met and that they are satisfied with our services. In addition, we are always available to answer any questions or concerns that may arise.
CLEAR AND REASONABLE
Our Management Approach
Secured™ believes that approaching each project with sound, proven and repeatable processes leads to better outcomes and increased client and customer satisfaction.
Our technical approach is based on our proven Stabilize-Optimize-Transform (SOT) methodology. It provides incremental, measurable improvements and efficiencies that eliminate duplications of effort, streamline processes, and improve security without disrupting ongoing operations. We team our Standard Operating Procedure (SOP) with our three tenets to our methodology, which are: People, Process, and Technology.
This methodology works for all critical operations within an organization and we will focus these processes on your growing security needs.
Secured's™ SOT Methodology
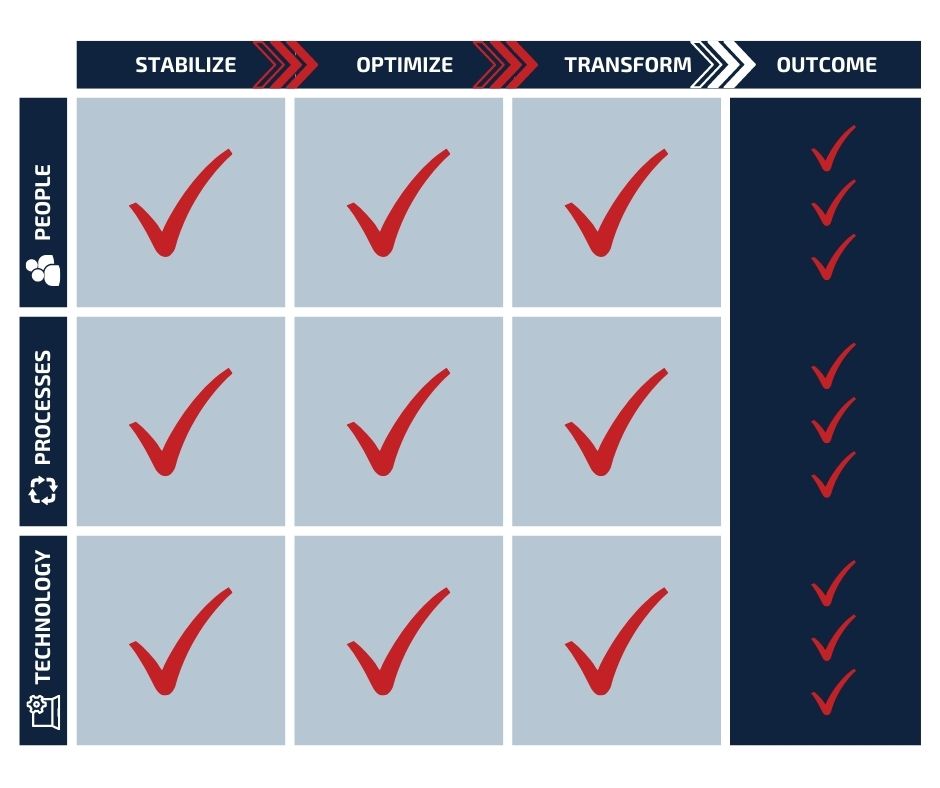
Stabilize
During the Stabilize phase, we identify highly qualified people to evaluate the task areas while maintaining continuity of service operations. We mitigate transition risk by applying our proven processes and procedures to determine baseline operations and ensure we achieve the performance metrics requested.
Optimize
To Optimize, we apply our IT and security service delivery approach which encourages personnel to innovate within your framework. Our team focuses on areas for time saving, waste elimination and strengthening security within your network. We focus on developing training to ensure all who access your environment (employees, contractors, and other users) know how to identify, avoid, and mitigate risks. In addition, we always seek opportunities for improvement.
transform
The Transform phase consists of analyzing and recommending new process and technology innovations to drive greater safety and efficiency. We also install needed security measures (with accompanying training and assessment) and provide consistent IT infrastructure services in support of your current and future missions.




