DDoS Attacks Emerge as Main Cyber Threat in Ukraine Conflict
Table of Contents
Background
On February 24th 2022 Vladmir Putin became his “special military operation” and sent Russian armed forces into Ukraine. The CyberPeace Institute has recorded cyber-attacks against a variety of host nations, including Ukraine and Russia. Reviewing their data from the past year highlights new cybersecurity attack trends, priorities, and hacker groups.
Prior to the start of the conflict there were years of Russian cyber-attacks on Ukraine. In 2014 the Russian government was suspected of targeting the Ukrainian government with the cyber weapon “Ouroboros” (the Greek symbol for a snake eating its own tail), also known as the “Snake” attacks. In 2015 Ukraine’s power grid was attacked by the Russian group Sandworm. Fancy Bear, another Russian hacker group, was reportedly targeting Ukrainian artillery systems from 2014 to 2016, according to Crowdstrike. Many security experts believe these attacks were Russia testing out cyber weapons in Ukraine.
Ukraine Cyber Attack Trends from 2022
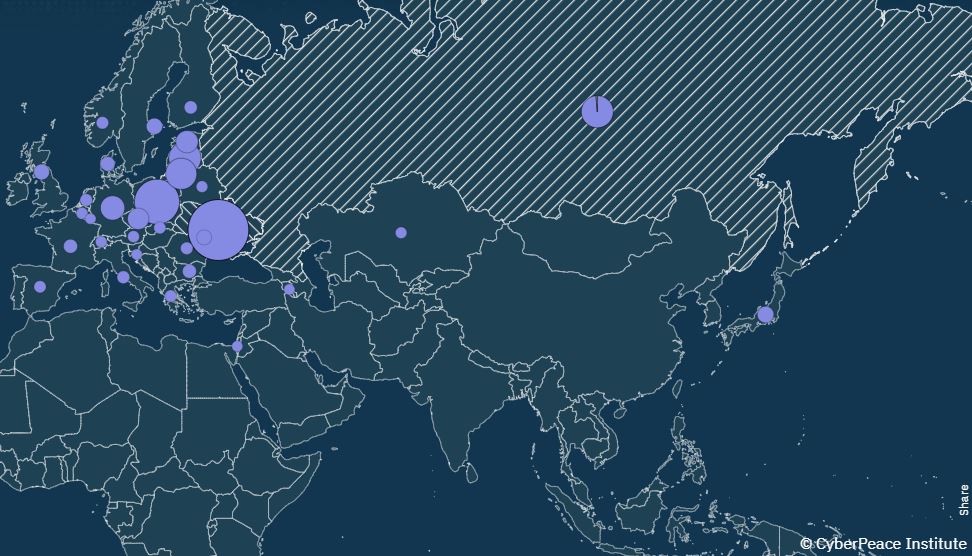
So, what cybersecurity attacks occurred over the past year in Ukraine? DDoS attacks. The CyberPeace Institute, an NGO based out of Switzerland, reported on cyber-attack trends over the past year. They noted that of “the 1,100 cyberattacks and operations analyzed, Distributed Denial of Service (DDoS) attacks make up the largest number of recorded incidents, amounting to 79% of all incidents.” The CyberPeace Institute noticed an increasing trend in a specific type of DDoS attacks: crowdsourced DDoS. Their report highlights that threat actors have “created software to crowdsource their DDoS activities amongst a broader public, potentially and functionally involving the general population in attacks and campaigns.” The CyberPeace Institute’s end of year report also noted “a 368% increase in attacks against countries that are not belligerents compared to the previous quarter (July to September 2022).” The major cyber threat groups behind these attacks typically claim ownership. These ‘self-attributed’ attacks consist of 80% of the attacks the CyberPeace Institute analyzed and provide a clear picture of the major cyber threat groups in the Ukraine-Russia conflict.
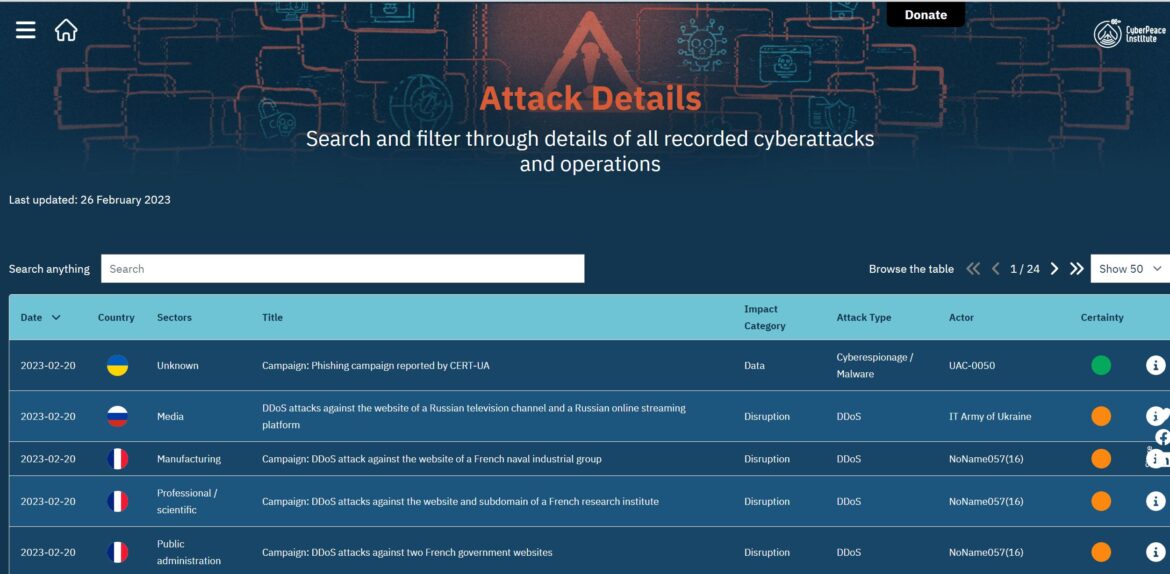
The CyberPeace Institute lists all major cyber attacks on their website, here:
According to the data, a handful of pro-Russian and pro-Ukrainian threat actors emerge as major threat groups.
The major pro-Russian groups are People’s CyberArmy, KillNet, Anonymous Russia, and NoName057(16).
The major pro-Ukrainian groups are Anonymous and the IT Army of Ukraine.
The IT Army of Ukraine gained worldwide attention upon its creation, just two days after the start of the conflict. The IT Army of Ukraine was formed by the Minister of Digital Transformation Mykhailo Fedorov via his Twitter account. They are known to use Telegram to list Russian domain names and IPs and encourage volunteers to perform DDoS attacks.
Ukraine Cyber Attack Trends in 2023
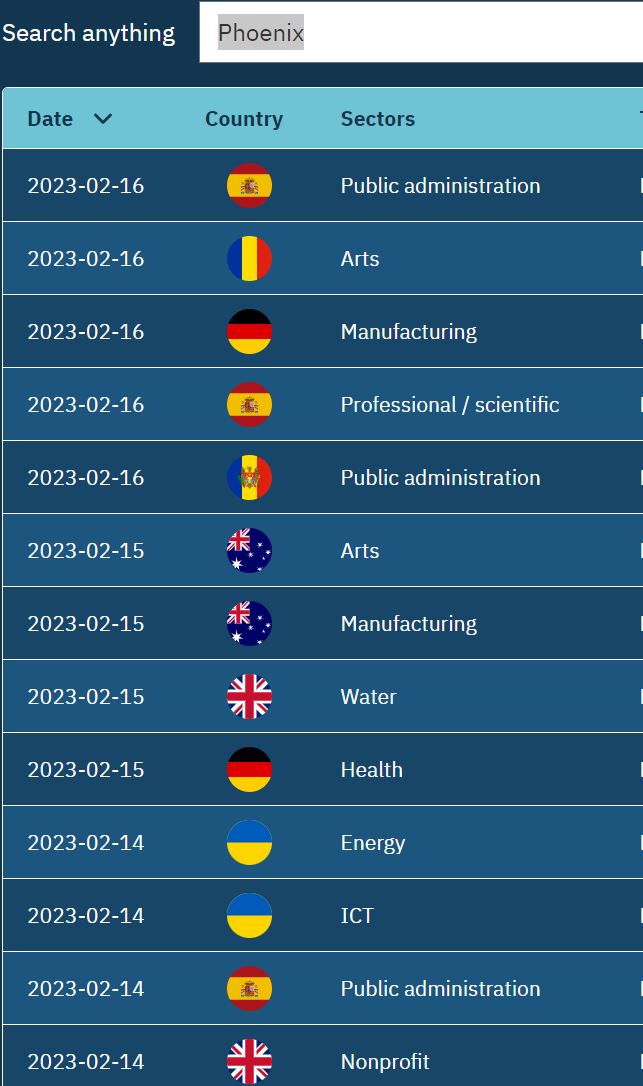
The CyberPeace Institute’s cyberattack database shows new trends for 2023. This past month 170 cyberattacks have been reported by the institute. They include a growing number of non-belligerent countries targeted by DDoS attacks. France, Germany, Poland, Estonia, Sweden, Japan, Moldova, Spain, Lithuania, Canada, the United States, United Kingdom, Latvia, Bulgaria, and Denmark have all been targeted by DDoS attacks. The public administration sector is the most targeted sector in January and February 2023. The past month’s data also highlights the prolific volume of attacks by the pro-Russia group NoName057(16). NoName057(16) attacks accounted for over 35% of the 170 cybersecurity attacks listed in February. The data also highlights the scope of targets by the pro-Russia group Phoenix, which has already attacked Germany, the United States, Pakistan, the United Kingdom, Spain, Australia, Moldova, and Romania in 2023. As shown below, Phoenix has targeted a range of sectors including manufacturing, arts, health and education.
Cybersecurity Best Practices
As more non-belligerent countries are targeted by DDoS attacks it is important to implement cybersecurity best practices to prevent and detect cyber threats.
Cybersecurity threat prevention prevent involves minimizing the attack surface.
Three examples include:
- Disabling all ports and protocols that are not essential for business purposes
- Update all software and prioritize updates that address known exploited vulnerabilities identified by CISA
- Reviewing the security of remote access methods to your network, and implement multi-factor authentication
Cybersecurity detection and response involves implementing the various tools and best practices. Three key cyber threat detection and response best practices include:
- Implementing antivirus and antimalware software
- Implementing network logging
- Review and inspect network traffic when working with Ukrainian organizations
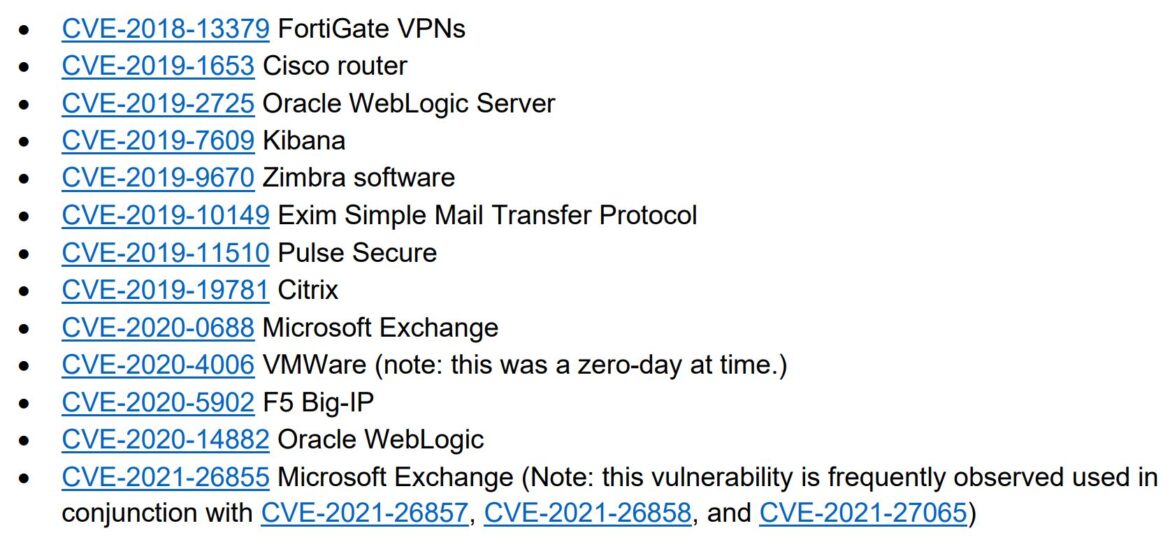
The 2023 trends for cyber attacks showed increasing DDoS attacks across various publics sectors and against non-belligerent countries. For more information on how to protect your enterprise network check out CISA’s Shields Up campaign. Shield’s Up recommendations using free tools like OpenVAS for vulnerability scanning and checking if you have exposed services with Shodan. Finally, consider reviewing CISA’s cybersecurity advisory: Understanding and Mitigating Russian State-Sponsored Cyber Threats to U.S. Critical Infrastructure. The advisory lists common vulnerabilities exploited by Russian state-sponsored advanced persistent threat actors. Below is the list released in March 2022.