Table of Contents
Background
Drone security is a challenging task that is matched by an ongoing news cycle of high-profile drone security issues. These headlines include major drone ID database leaks and controversy surrounding DJI. In the Ukraine war, DJI received criticism for its “drone detection platform” Aeroscope. DJI also claimed its DroneID was encrypted, but this was disproved and later shown to be used to locate drone operator locations.
Since 2020, the National Defense Authorization Act (NDAA)’s Section 848 prohibits the DOD from buying sUAS components from China. In December 2021 DJI was one of eight Chinese tech firms officially identified by the U.S. Treasury Department to be part of the Chinese Military-Industrial Complex. DJI has also been blacklisted for its alleged involvement in the surveillance of Uyghurs in China. This DJI controversy and NDAA’s Section 848 led to a clear necessity for proper drone security vetting: Blue UAS 2.0.
Blue UAS 2.0
Blue UAS 2.0 has emerged as a cyber-security framework for approving UAS for DOD procurement. Led by the Defense Innovation Unit (DIU), Blue UAS 2.0 aims to make commercially available drones NDAA-compliant. Blue UAS 2.0 vets UAS components following cybersecurity and supply chain requirements. DIU maintains a continually updated list of Blue UAS 2.0 cleared drones. As of June 2023, there are 17 drones:
Blue UAS 2.0 is not meant to exclude foreign drone manufacturers but instead aims to streamline approval for DOD procurements. For example, Parrot has two drones on the list and is headquartered in France. The current list can be found here.
Blue UAS 2.0 is also not the only way for approving DOD UAS procurements. DIU clearly states that DOD organizations can purchase non-Blue UAS products and components by completing their own compliance verification processes.
Blue UAS 5 Lines of Effort
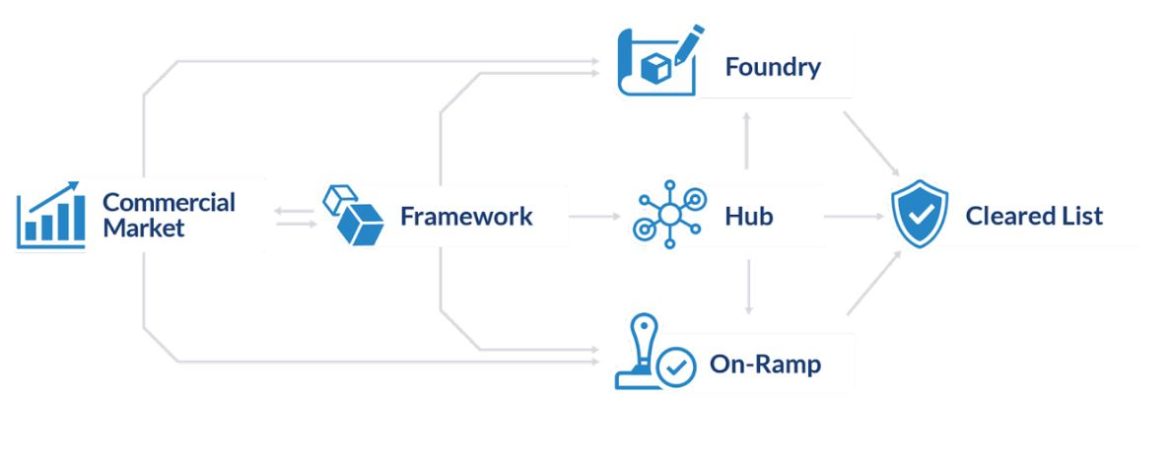
DIU uses 5 lines of effort to implement Blue UAS and verify UAS drones:
- Blue UAS Cleared List: a list of NDAA-compliant drones that are available for government purchase and operation.
- Blue UAS On-Ramp: an approval process for commercial UAS products.
- Blue UAS Hub: a website that provides Blue UAS resources and policy updates.
- Blue UAS Framework: DIU provides options on NDAA-compliant UAS components and software.
- Blue UAS Foundry: DIU provides prototyping which aims to implement NDAA-compliant UAS components and software to prototype with new or existing UAS.
Working from left to right the Blue UAS Framework aims to use these 5 lines of effort to streamline the approval of UAS drones for DOD procurement:
Drone Security Frameworks Going Forward
Drone security frameworks will likely continue to evolve. Blue UAS 2.0 is soon be replaced by Blue UAS 3.0 in the coming months. In February, the nonprofit Association for Uncrewed Vehicle Systems International (AUVSI) released Green UAS which vets commercial UAS that do not require DOD vetting. Last month, AUVSI also announced the Trusted Cyber Certification program which will provide security vetting for air, ground, and maritime systems. These new frameworks aim to address the broader uncrewed systems market and provide specific guidance that follows cybersecurity industry standards.
Drone Security Best Practices
Secured recommends adhering to cybersecurity and software supply chain best practices for UAS. Examples include:
- Properly evaluate and verify the software and firmware associated with your UAS systems.
- Ensure proper encryption for the UAS data link.
- If TLS is supported, use the highest standard that the UAS supports.
- If using Wi-Fi, use complicated SSIDs. Do not have the UAS broadcast the SSID or network name.
- Take extra caution when downloading UAS software, and limit access to enterprise networks.
- Use MFA for all UAS accounts.
These are just a few examples of CISA’s best practices for UAS. Secured recommends reviewing DIU’s website and CISA’s documentation for updates on vetting the security of UAS software and components: