Lessons from the City of Dallas Ransomware Attack
Table of Contents
Background
Two weeks ago, the city of Dallas was impacted by a ransomware attack by the suspected ransomware group Royal. This same group also targeted the Dallas Central Appraisal District website in November 2022. In March 2023 CISA released a cybersecurity advisory warning about Royal Ransomware. The alert notes that criminals have been using a new Royal ransomware variant to target U.S. and international organizations since around September 2022.
The May 2023 ransomware attack on Dallas affected various Dallas websites and services. The fallout from this includes:
- delayed 311 service requests
- closed courts with all cases rescheduled
- Dallas Water Utilities inability to process payments
- delayed application, registration, and payment operations for various city services
- Police, EMS, and fire departments reverted to manual radio communication and dispatch
- Police are reportedly unable to use their patrol car computers delaying checks on license plates and warrants.
Royal Ransomware Access
CISA’s alert provides specific guidance and background on Royal ransomware. These malicious actors typically gain access through 4 methods (as of November 2022):
- Phishing: 66.7% of Royal actors gain access through phishing emails
- Remote Desktop Protocol (RDP): 13.3% of Royal actors gain access through RDP
- Public-facing applications
- Brokers
Key ransomware mitigation strategy involves directly addressing Royal actors common methods of gaining initial access:
Royal Ransomware Process
After Royal actors gain access to a system they disable antivirus software, exfiltrate large amounts of data and use a custom file encryption program on target systems to lock out users. Royal actors will use this exfiltrated data to prove their access and also to threaten future data leaks. This combination of data extortion and ransomware is called double extortion. Double extortion involves both threatening to release data and block services through their ransomware encryption.
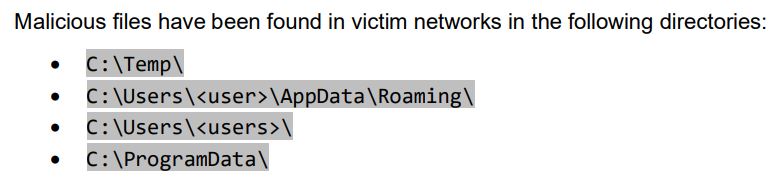
CISA also notes that Royal actors use these common directories to save files:
Royal Ransomware IOCs
CISA’s alert includes various Indicators of Compromise (IOC) by Royal actors.
For a detailed list, check out CISA’s Royal Ransomware alert. Files with the .royal file extension are an example IOC. The alert also includes a list of malicious IP addresses, malicious domains, SHA256 file hashes of commonly used tools by Royal actors and hash values of commonly used batch (.bat) scripts. The alert includes common MITRE attack framework techniques for Initial Access, Command and Control, Escalation, Defense Evasion and Impact.
CISA’s 15 Royal Ransomware Mitigation Guidelines
- Implement a data recovery plan.
- Require all accounts with password logins comply with NIST standards. Refer for the CISA Alert for 8 NIST example policies.
- Require multi-factor authentication.
- Keep all operating systems, software, and firmware up to date.
- Segment networks.
- Identify, detect, and investigate abnormal activity and potential traversal of the indicated ransomware with a networking monitoring tool.
- Install, regularly update, and enable real time detection for antivirus software on all hosts.
- Review domain controllers, servers, workstations, and active directories for new and/or unrecognized accounts.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Disable unused ports.
- Consider adding an email banner to emails received from outside your organization.
- Implement time-based access for accounts set at the admin level and higher.
- Disable command-line and scripting activities and permissions.
- Maintain offline backups of data, and regularly maintain backup and restoration.
- Ensure all backup data is encrypted, immutable (i.e., cannot be altered or deleted), and covers the entire organization’s data infrastructure.
Secured also provides various cybersecurity services, including vulnerability assessments and penetration testing, that can help proactively protect businesses from cyber attacks.


