Microsoft AD Domain Services Privilege Escalation (CVE-2021-42287 and CVE-2021-42278)
Date Added to KEV Catalog: November 03, 2021
CISA Due Date for Remediation: November 17, 2021
Table of Contents
Vulnerability
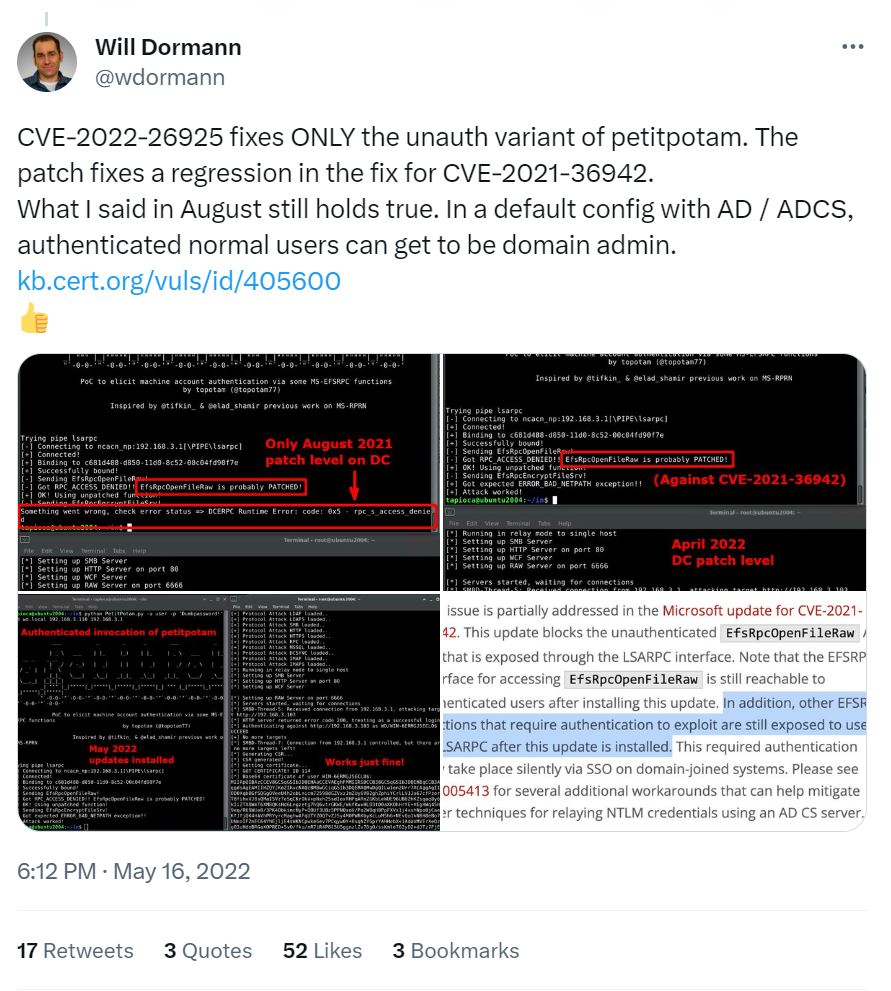
“PetitPotam” is an NTLM relay attack, and a vulnerability commonly checked for in Active Directory penetration testing. In August 2021 it was reported that the ransomware group LockFile used PetitPotam with ProxyShell to compromise Windows Domain Controllers. This vulnerability targets Windows Local Security Authority (LSA). An unauthenticated attacker can call the LSARPC and coerce the DC to use NTLM by using methods like Encrypting File System Remote (EFSRPC). Domain Controllers that host AD Certificate Services are commonly targeted for NTLM relay.
Will Dorman explains: “By relaying an NTLM authentication request from a domain controller to the Certificate Authority Web Enrollment or the Certificate Enrollment Web Service on an AD CS system, an attacker can obtain a certificate that can be used to obtain a Ticket Granting Ticket (TGT) from the domain controller. This attack, known as a “Golden Ticket” attack, can be used to fully compromise the entire Active Directory infrastructure.”
CVE-2021-36942 vs CVE-2022-26925
Currently, the most recent PetitPotam vulnerability is CVE-2022-26925 which allows an unauthenticated attacker to target DC with LSARPC.
Since there are both unauthenticated and authenticated vulnerabilities, penetration testers typically check for both. During an Active Directory penetration test, the unauthenticated vulnerability is checked for during initial enumeration and the authenticated vulnerability can be checked again after the tester gets valid domain credentials.
Systems Affected and Detection
These operating systems are vulnerable:
- Windows Server 2008 R2
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server 2019
- Windows Server 2004
- Windows Server 20H2
PetitPotam primarily (but not exclusively) affects Active Directory Certificate Services (AD CS) with
Certificate Authority Web Enrollment and Certificate Enrollment Web Service.
There are various detection options including Metasploit, CrackMapExec, and Nessus.
Before running the Metasploit PetitPotam scanner, an SMB server should be run in the background on Metasploit: auxiliary/server/capture/smb.
Then the scanner (auxiliary/scanner/dcerpc/petitpotam) options can be set and run:
RHOSTS- to match target
VERBOSE- true
LISTENER- to match the listening SMB Server
PIPE- the default is lsarpc. Other named pipes include: efsrpc, samr, lsass, netlogon
CrackMapExec includes a SMB module:
crackmapexec smb <ip> -u ” -p ” -M petitpotam
Tenable also detects for PetitPotam.
Exploitation
The most popular exploit tool is by topotam on GitHub, which has Windows executable (.exe) and python options. Similarly, Swisskyrepo on GitHub provides a good breakdown of how to exploit PetitPotam, simplified here:
- Setup Responder: responder -I eth0 –lm
- Run PetitPotam (with DC-IP, Responder-IP, and with or without credentials)
- Crack the NTLM hash
- DC Sync Using the Pass-the-Hash
Remediation
Microsoft’s KB5005413 “Mitigating NTLM Relay Attacks on Active Directory Certificate Services (AD CS)” outlines various mitigation options. They include:
- Enable Extended Protection for Authentication (EPA) for Certificate Authority Web Enrollment and Certificate Enrollment Web Service
- After enabling EPA, update the Web.config file created by CES
- Require SSL
- Enable SMB Signing
- Disable NTLM authentication. Examples include disabling NTLM for the Windows DC, AD CS Servers, and IIS running the Certificate Authority Web Enrollment and Certificate Enrollment Web Service.