In order to understand Red Team, it is important to be aware of the different cybersecurity roles (teams) and functions in the cybersecurity industry. Traditionally, the three primary cybersecurity teams are Red, Blue and Purple:
- Red Team: Offensive Security
- Blue Team: Defensive Security
- Purple (team/function): the interaction between offensive and defensive teams.
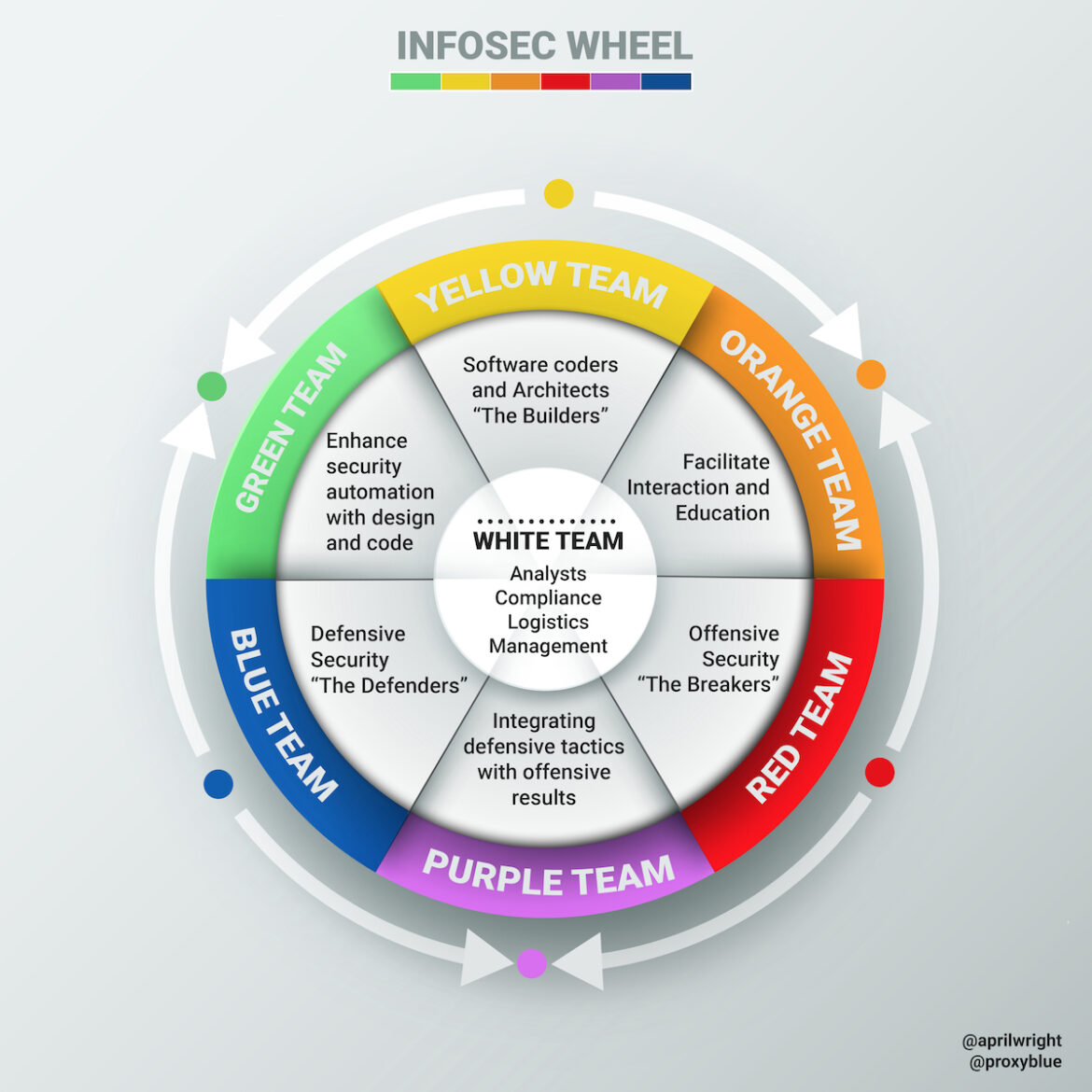
A newer framework includes Green, Yellow, and Orange Teams. This framework was introduced by April Wright in the Blackhat presentation, “Orange is the new Purple“. In this framework, the three main “roles” are the three primary colors: offensive (Red), defensive (Blue), and builders/developers (Yellow). The Green, Purple and Orange Teams facilitate between Red, Blue, and Yellow Teams. These teams are presented by @proxyblue as an Infosec Color Wheel. It distills these different teams and functions, and provides an easy-to-follow visual guide to the different cybersecurity roles.
Red Team: Test Blue Team Detection and Response
Red Team, Penetration Testing, and Vulnerability Assessments
Red Team vs Penetration Testing
Red Teams and penetration testers also have different objectives. Red Teams aim to test Blue Team’s detection and response to a real threat actor. This typically leads to a longer engagement time and a higher focus on stealth and evasion. Since the goal is to test the defensive posture of an organization, Red Teams often include social engineering or physical intrusion testing, which leads to a longer engagement time. Penetration testers aim to identify and exploit vulnerabilities with a specific goal in mind, like stealing customer data. Daniel Miessler further breaks down this comparison in this post.
The differences between Red Team and penetration testers are not strict and can change depending on the needs of the client and the rules of engagement.
Below is a table that summarizes many of these differences:
Red Team
Penetration Testing
Objective
Methods
Time Frame
Longer engagements, “campaigns”, cans be multiple weeks or months
Shorter engagements are typically under a month (~ 1 week)
Client objective (e.g. get administrative privileges, access customer data)
References:
- https://danielmiessler.com/study/red-blue-purple-teams/
- https://www.blackhat.com/docs/us-17/wednesday/us-17-Wright-Orange-Is-The-New-Purple.pdf
- https://hackernoon.com/introducing-the-infosec-colour-wheel-blending-developers-with-red-and-blue-security-teams-6437c1a07700
- https://danielmiessler.com/study/vulnerability-assessment-penetration-test/

