Cyber Attacks on the Oil and Gas Sector
The oil and gas industry has been at the forefront of a tumultuous news cycle this past year. Major headlines included increasing energy prices due to sanctions on Russian oil, the Nord Stream 1 and 2 pipeline bombings this past September, and the OPEC+ announcement last October that they will be reducing oil production by 2 million barrels per day. Coinciding with these geopolitical events was the constant threat of cyberattack on the oil and gas sector.
The last decade has seen a global rise in cybersecurity attacks on the oil and gas sector. Saudi Aramco, a Saudi Arabian public petroleum and natural gas company, was attacked in 2012, 2016, 2017, and 2021. In 2014, Norway revealed that 50 companies in the oil sector were targeted by a successful spearfishing campaign that led to data breaches. This past February, 17 oil ports in Belgium, Germany and the Netherlands were attacked by a large-scale ransomware attack that disrupted operations. The Colonial Access Pipeline attack in May 2021 is arguably the most famous cyber-attack on the oil and gas sector. This ransomware attack shut down 5,500 miles of pipeline that carry over 40% of fuel for the U.S. east coast. Cybersecurity attacks on the oil and gas sector also lead to longer business downtimes than for other industries. According to Trend Micro’s 2022 Oil & Gas Survey, “the oil and gas industry averaged 6 days for system outages due to cyberattacks, one day longer than the five days for other industries.” The next two sections look at what resources and best practices are available to mitigate these attacks.
Oil and Gas Sector Cyber Threat Resources
In May 2021 the Colonial Access Pipeline was hacked by the cybersecurity ransomware-as-service group DarkSide. On May 7th Colonial Access Pipeline paid a ransom of 75 bitcoin ($4.4 million) to the hackers. The attack shutdown the pipeline for six days and fuel shortages led to panic buying across multiple states. One month later the Department of Justice announced the recovery of 63.7 bitcoin ($2.3 million) from DarkSide. On May 9th President Biden issued an emergency declaration which was followed by the May 12th Executive Order on Improving the Nation’s Cybersecurity. Key goals from this executive order include: improving cybersecurity standards in the Federal Government, increasing threat information sharing between the government and private sector, and improving software supply chain security. This executive order aims to strengthen the cybersecurity posture of the oil and gas sector, critical to national security.
The U.S. pipeline infrastructure is designated as one of 55 National Critical Functions. In October 2018 the Cybersecurity & Infrastructure Security Agency (CISA) and the Transportation Security Administration (TSA) were both tasked with implementing the Pipeline Cybersecurity Initiative (PCI) which aims to assess “cybersecurity risks to the Nation’s pipeline infrastructure—with a focus on oil and natural gas (ONG) pipelines.” Oil and gas sector companies should leverage CISA’s Pipeline Cybersecurity Resources Library to ensure they are utilizing resources for vulnerability assessments, malware analysis, threat reporting, and other cybersecurity best practices. CISA also provides the Cyber Resource Hub which includes cybersecurity evaluation tools, including the Ransomware Readiness Assessment (RRA) which helps organizations better assess their ability to defend and recover from ransomware attacks.
As an example, in the infographic below CISA and TSA specifically address pipeline operators and focus on the exposure of integrating information technology (IT) and operational technology (OT) systems. CISA acknowledges the operational efficiency and safety benefits of integrating information communication technology (ICT), like remote access and internet-connect devices, but also emphasizes that this increases the attack surface that can be targeted by cyber threat actors. The infographic outlines how to protect this larger attack surface and addresses specific best practices, like the importance of network segmentation between IT and OT environments.

CISA and TSA provide tailored cybersecurity guidance for the oil and gas sector: Pipeline Cyber Risk Mitigation.
Oil and Gas Sector Cyber Threat Best Practices
Trend Micro’s 2022 Oil & Gas Survey asked over 900 companies: what type of attack has forced the shut down operations of ICS/OT systems? Compared to other industries, the oil and gas sector reported a higher percentage of attacks from:
- exploitation of remote access
- compromise of internet accessible device
- malware infection due to legitimate web browsing
- phishing
These results reflect the methods used in the Colonial Access Pipeline attack along with the cyber attacks in Norway, Saudi Arabia, and eastern Europe. The Colonial Access Pipeline was hacked due to password reuse with a VPN- exploitation of remote access. The 2012 Saudi Aramco attack became famous for the Shamoon malware that was used during the attack. The Norway, eastern European attacks, and the 2012 Saudi Aramco attacks all included phishing attacks. CISA and TSA guidance from the Pipeline Cybersecurity Initiative address these same threats and help the oil and gas sector mitigate the risk of attack from phishing and malware.
CISA’s National Cyber Awareness System provide Alerts, Analysis Reports, Current Activity, and Bulletins. Following the Colonial Access Pipeline attack, CISA released two alerts that applied directly to the oil and gas sector- alerts on ransomware and malware attacks. Ransomware attacks typically rely on a combination of phishing and malware. Five days after the Colonial Access Pipeline attack, CISA released the following alert: DarkSide Ransomware: Best Practices for Preventing Business Disruption from Ransomware Attacks. The alert mentions implementing network segmentation of OT and IT systems, and specifically addresses three main issues:
- how to prevent ransomware attacks
- how to minimize the damage if attacked by a ransomware attack
- what to do if impacted by a ransomware attack
While not all oil and gas sector cyber attacks are ransomware attacks, the best practices listed in the alert fundamentally address the specific issues that come from combining OT and IT systems. The DarkSide Ransomware alert includes a comprehensive list of mitigations, including five actions:
- Update software
- Require multi-factor authentication
- Limit access to resources over networks, especially by restricting RDP
- Implement regular data backup procedures
- Enable strong spam filters to prevent phishing emails from reaching end users. Implement a user training program and simulated attacks for spearphishing
One month after this ransomware alert was issued, CISA released its malware prevention alert. It listed 5 key immediate actions to prevent against malware: CISA’s August 2021 Key Malware Protection Actions

Malware is a key component of ransomware attacks, so the overlap in these same 5 cybersecurity practices is to be expected. These two alerts illustrate that by following ransomware and malware prevention guidance the oil and gas sector can address specific cybersecurity issues related to pipeline security. Both alerts also specifically address the importance of network segmentation:
- The CISA ransomware alert states: Implement and ensure robust network segmentation between IT and OT networks
- The CISA malware alert states: implement network segmentation to separate network segments based on role and functionality
In the infographic below CISA highlights that creating boundaries between information technology (IT) and operational technology (OT) systems through network segmentation reduces threats from phishing and malware attacks. The graphic highlights the level of effort needed for an attacker to breach an unsegmented versus segmented network, with yellow represented low effort and red representing high effort:
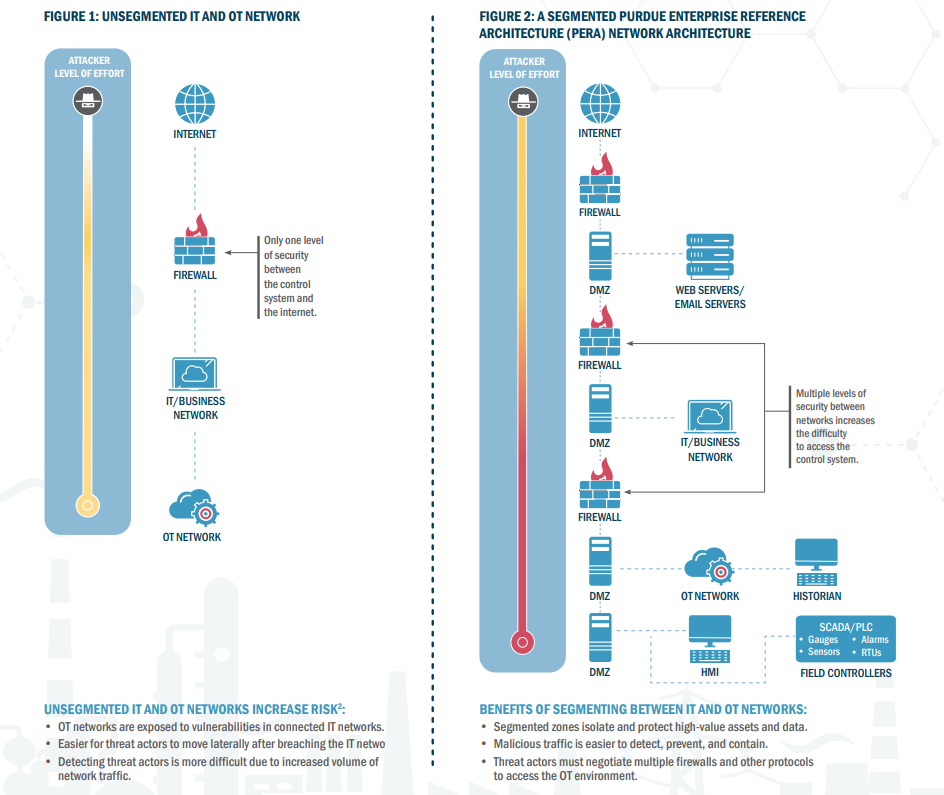
CISA’s Layering Network Security Through Segmentation Infographic
By segmenting IT and OT systems an attacker does not get direct access to all systems after initial access and must also breach multiple firewall and other protocols to get into the OT network.
These CISA alerts and guidance emphasize that the core best practices for pipeline security effectively address malware and ransomware attacks, and segmentation of IT and OT systems. As oil and gas companies continue to be a popular target of threat actors, following the best practices and resources from CISA and PCI can protect against these specific cyber threats. IT security professionals seeking to resolve the key issues mentioned in this primer and encouraged to use the below resources and referenced alerts to get more in-depth solutions and guidance.
References
Trend Micro’s 2022 Oil & Gas Survey
Executive Order on Improving the Nation’s Cybersecurity
CISA Alerts
Alert (AA22-216A) 2021 Top Malware Strains
CISA Infographics
Layering Network Security Through Segmentation
Pipeline Cyber Risk Mitigation.
CISA Resources
National Cyber Awareness System

