Microsoft AD Domain Services Privilege Escalation (CVE-2021-42287 and CVE-2021-42278)
Date Added to KEV Catalog: April 11, 2022
CISA Due Date for Remediation: May 02, 2022
Table of Contents
Vulnerability
CVE-2021-42278 and CVE-2021-42287 are two critical Active Directory vulnerabilities discovered in November 2021. When used together they allow privilege escalation to Domain Admin.
CVE-2021-42278 “sAMAccountName”
CVE-2021-42278 allows for a user to impersonate a domain controller using computer account sAMAccountName spoofing. Active Directory user accounts can have two logon name attributes: sAMAccountName and userPrincipalName(UPN). UserPrincipalName is the newer attribute for user logon names and is more commonly used for logging onto Windows environments. UPNs need to be unique within an AD forest, while sAMAccountNames need to be unique in a domain. UPN combines the user account name, “@” symbol and DNS domain name, for example: someone@domain.com.
sAMAccountName is the older and original logon name for users. The sAMAccountName follows the format: DOMAIN\Username. Microsoft documentation states that computers accounts with the USER_WORKSTATION_TRUST_ACCOUNT flag must have their sAMAccountName end with a dollar sign ($):
Prior to CVE-2021-44278, no validation was made to confirm the trailing dollar sign ($) after a sAMAccountName attribute. This allowed users to impersonate Domain Controller accounts.
CVE-2021-42287 “noPAC”
CVE-2021-42287 is a security vulnerability of the Kerberos Privilege Attribute Certificate (PAC). For an overview on Kerberos check out Secured’s earlier post. In Kerberos, the KDC issues Service Tickets (ST) after receiving a Ticket Granting Ticket (TGT). With this vulnerability when the KDC verifies the received ST and cannot locate it, it will search again and add a dollar sign ($). Kerberos includes delegation extensions like S4U2Self and S4U2Proxy. Service for User to Self (S4U2Self) allows for a service to obtain a Service Ticket for itself on behalf of a user. This can be abused if an attacker leverages CVE-2021-4478 in the following steps:
1) an attacker can create a computer account without a dollar sign ($), rename it “DomainController” and get a TGT
2) an attacker can then rename the account with a trailing $, and request a ST with the original TGT
At this point the KDC will then not be able to locate this user. The KDC searches again and adds a $, and issues a ST as the DomainController$ through S4U2Self, leading to domain admin.
Systems Affected and Detection
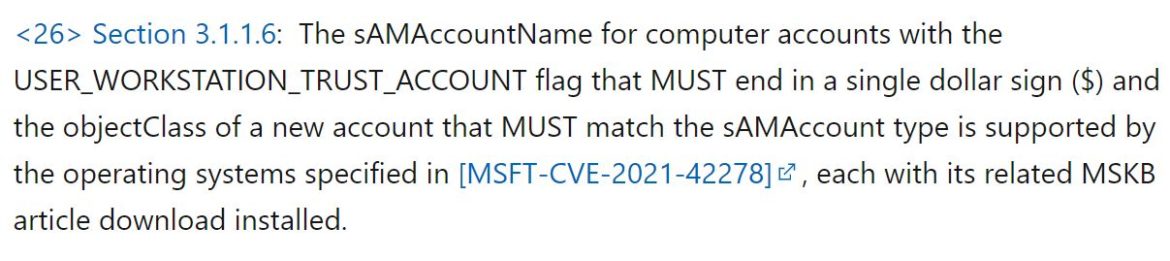
The following systems are affected (prior to the November 2021 update):
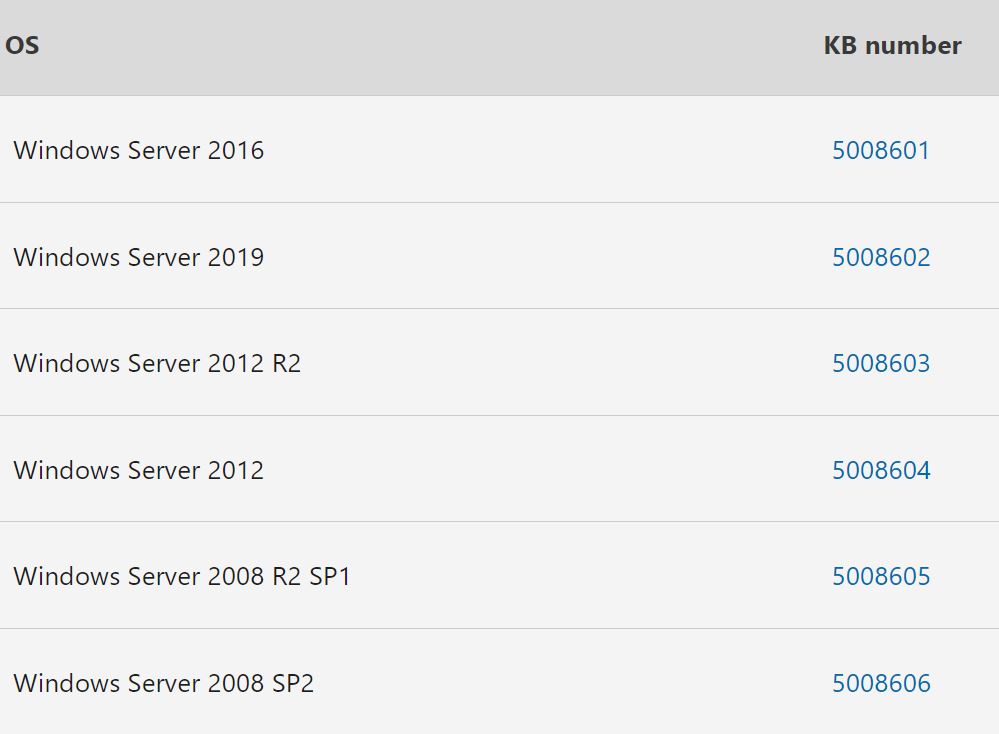
One remote detection option is a python script from GitHub, scanner.py:
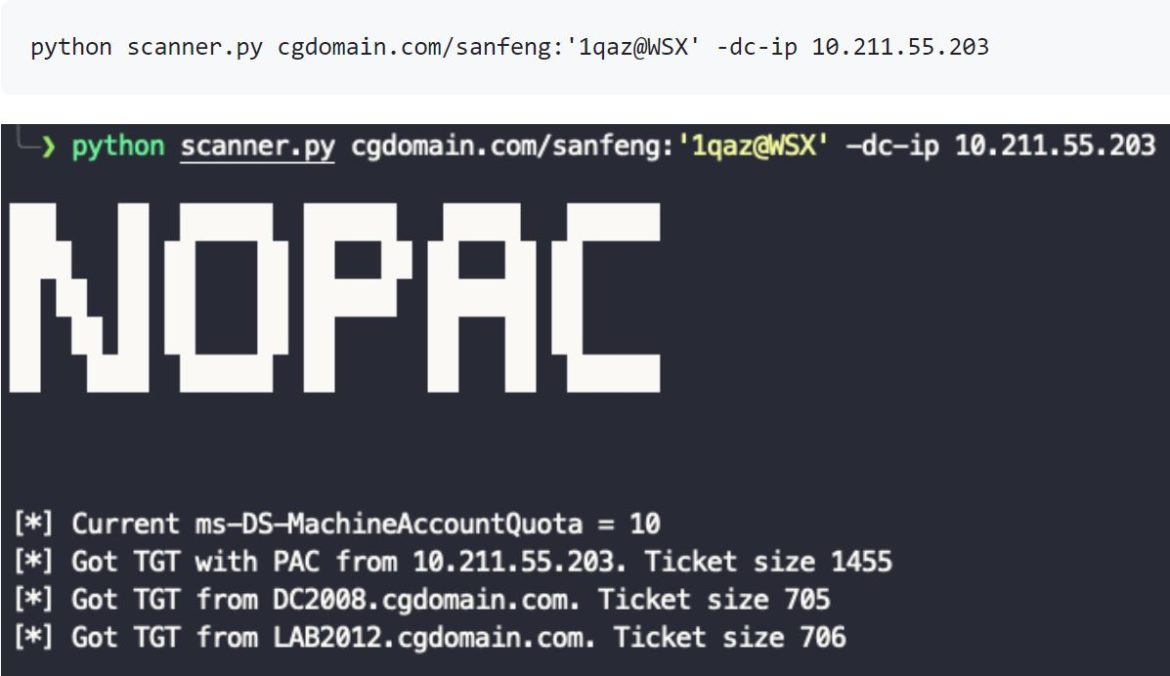
Crackmapexec also has a detection module called nopac:
cme smb IP –u <user> -p <password> -M nopac
The Remediation Section also shows that local detection can be done through PowerShell scripts by checking sAMAccountNames and sAMAccountTypes.
Exploitation
There are various exploit options for privilege escalation.
noPac.py and noPac.exe are two automated options.
This Orange Cyberdefense Active Directory Mind Map shows that Domain Admin can be achieved through Passing the Ticket and DC Sync:
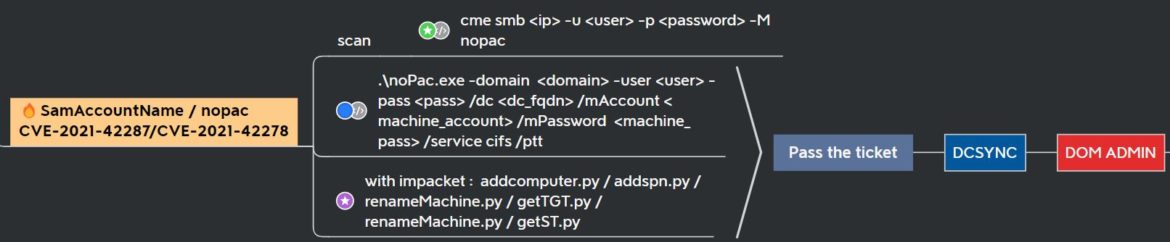
The Hacker Recipes has a very thorough list of the 7 steps for exploiting both Unix and Windows environments. Unix exploitation relies on Impacket scripts. Windows exploitation uses PowerShell scripts through PowerMad, along with Rubeus and Mimikatz.
The Hacker Recipes outlines these 7 steps:
# 0. create a computer account
# 1. clear its SPNs
# 2. rename the computer (computer -> DC)
# 3. obtain a TGT
# 4. reset the computer name
# 5. obtain a service ticket with S4U2self by presenting the previous TGT
# 6. DCSync
Remediation
Window’s update on November 9, 2021 addressed both CVE-2021-42278 and CVE-2021-42287. PowerShell scripts can also search for non-compliant accounts.
To find computer accounts that have a non-compliant sAMAccountName:
Get-ADComputer -LDAPFilter “(samAccountName=*)” |? SamAccountName -NotLike “*$” | select DNSHostName, Name, SamAccountName
To find computer accounts that have a non-compliant UserAccountControl sAMAccountType:
Get-ADComputer -LDAPFilter “UserAccountControl:1.2.840.113556.1.4.803:=512”