On February 6th law enforcement officials charged a neo-Nazi leader and his associate with plotting to attack Baltimore’s power grid. Brandon Russell and Sarah Clendaniel were arrested and charged with conspiring to damage an energy facility. They allegedly targeted Baltimore Gas and Electric, which provides energy to 1.2 million central Maryland customers. Russel is a founder of a neo-Nazi group called the Atomwaffen Division and a convicted felon. These arrests follow a rise in power grid attacks in Oregon, Washington, and North Carolina.
These high profile attacks reflect data released by the US Energy Department that shows that the “number of direct physical attacks, including acts of vandalism and other suspicious activity, that potentially threatened grid reliability rose 77% to 163 in 2022.” Implementing joint cybersecurity and physical security best practices can help protect the electrical power grid.
In November 2022 the Cybersecurity and Infrastructure Security Agency (CISA) published the 162-page report: “Resilient Power Best Practices for Critical Facilities and Sites”. The report provides guidance on various areas to protect critical infrastructure: backup generation sources, fuel, controls systems, renewable energy, energy storage, telecommunications, electromagnetic (EM) security, physical security and cybersecurity. The report notably combines physical security and cybersecurity and clearly outlines the importance of their integration for greater resilience of critical infrastructures. This post highlights guidance from CISA’s report.
Cybersecurity and Physical Security Convergence
Cybersecurity and physical security convergence aims to combine two typically separate fields and establish more formal collaboration. According to CISA, this convergence leads to organizations that “are more resilient and better prepared to identify, prevent, mitigate, and respond to threats. Convergence also encourages information sharing and developing unified security policies across security divisions.”
The need for cybersecurity and physical security convergence is due largely from an increase in hybrid attacks. CISA explains that “the adoption and integration of Internet of Things (IoT) and Industrial Internet of Things (IIoT) devices have led to an increasingly interconnected mesh of cyber-physical systems (CPS), which expands the attack surface and blurs the once clear functions of cybersecurity and physical security.” Most recently, on February 9th 38 security vulnerabilities for wireless Industrial IoT were reported.
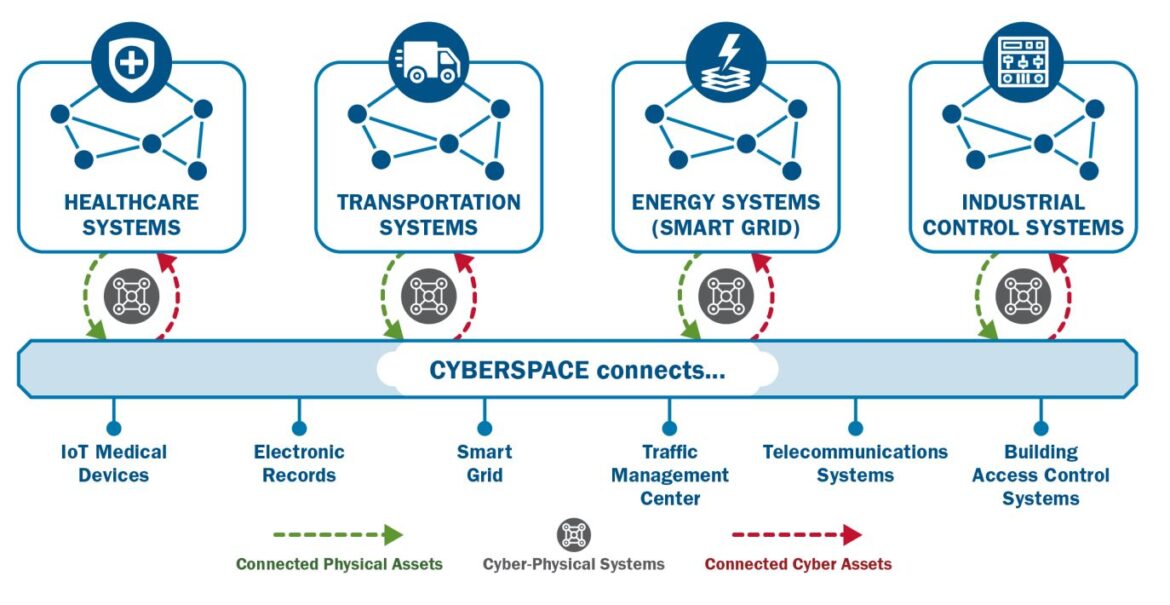
Common home IoT devices include TVs, speakers, security cameras, and thermostats. IoT devices have expanded into other sectors like healthcare (pacemakers, insulin pumps, ventilators, IV pumps), manufacturing (industrial sensors for tracking products, machinery and safety) and transportation (GPS and monitors for vehicle condition). The energy sector uses IoT technology to monitor power lines, power grids and control the flow of electricity. This widening cyber-physical attack surface comes with cybersecurity best practices that depends on established resilience levels (1-4) for critical instrasture facilities. Below are cybersecurity best practices that apply to all facilities.
- CISA 16 Cybersecurity Best Practices for Critical Facilities :
- Implement Zero Trust Security Model
- Minimize Account Privileges
- Identify Assets
- Provide Manual Override
- Monitor Network Traffic
- Log Cybersecurity Events
- Implement Strong Identity and Access Management
- Train Employees and Conduct Exercises
- Deploy End-to-End Encryption
- Patch and Upgrade Software
- Deploy Artificial Intelligence (AI)
- Backup Data
- Protect Against EM
- Create Incident Response and Continuity Plans
- Develop Unified Security Policies
- Conduct Assessments
Many of these best practices overlap with physical security. Training and conducting exercises would include physical security personnel. Implementing a Zero Trust Model requires support and collaboration with physical security teams. Incident response plans require physical security personnel, especially in the electrical grid sector where fuel resources may need to be protected. Develop unified security policies specifically addresses the importance of converging physical security and cybersecurity. CISA outlines this importance of this physical security and cybersecurity convergence in three statements.
CISA’s Unifying Cybersecurity and Physical Security Policy:
- Converge cybersecurity and physical security functions to create unified security policies.
- The unified policies should include many of the above mitigations such as identifying assets, training personnel, conducting exercises, creating an incident response plan, and developing response and continuity plans
- Identify the interactions between the physical and cyber assets including the interdependencies to adequately plan for, protect against, and respond to threats/incidents Source
There are numerous benefits to physical and cybersecurity convergence for the electrical grid. Through collaboration and communication CISOs and CSOs can develop better threat management strategies and recognize shared risks. The six physical security factors for protecting electrical power grids would also benefit from cybersecurity guidance.
CISA’s 6 Physical Security Areas
- Site Location
- Restricted Access Policies
- Physical Security and RF Barriers
- Monitoring Systems
- Protection Against Natural Elements
- Flooding Source
Protecting against vandalism, attacks on generators and backup power supplies should include cybersecurity specialists. Restricted access policies require cybersecurity measures to protect against failures from power outages, and outdated or poorly implemented security systems. Monitoring systems should also be protected from cybersecurity attacks.
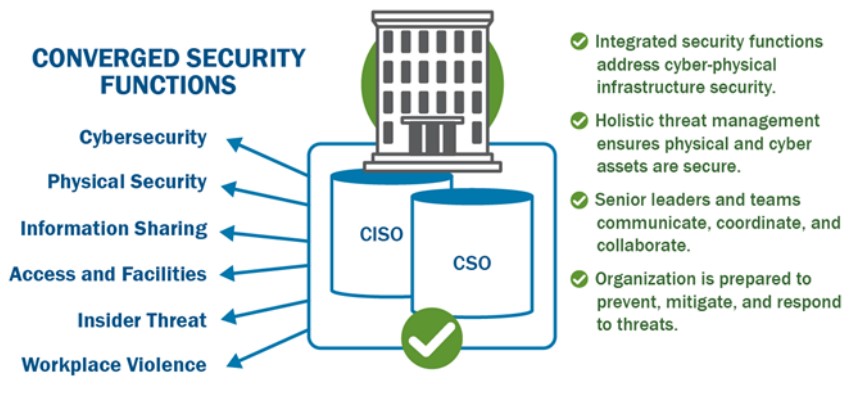
Recognizing shared threats allows for greater efficiency and prevents duplicate efforts by CISOs and CSOs that address the same threats. This convergence should increase the awareness of threats for both physical security and cybersecurity teams and create a shared strategic effort with a more unified incident response. For an overview on physical security and cybersecurity convergence access CISA’s report and guide.

