Apache CouchDB Remote Privilege Escalation (CVE-2022-24706)
Date Added to KEV Catalog: August 25, 2022
CISA Due Date for Remediation: September 15, 2022
Table of Contents
Vulnerability
The Apache CouchDB Remote Privilege Escalation vulnerability is due to an open distribution port that also uses a default Erlang cookie, “monster”.
Apache CouchDB is an open-source NoSQL database implemented in Erlang. CouchDB can be run in Standalone or Cluster modes of operation. Cluster mode allows for a cluster of CouchDB installations to be replicated with each other via network connections, typically with servers. CouchDB in cluster mode uses port 5894 as its primary port and uses the erlang port mapping daemon (epmd) on port 4369 to find other nodes so that servers can communicate with each other. Applications are automatically assigned random ports to communicate with other nodes, often in the TCP port ranges 9100-9200.
CouchDb’s documentation on cluster setup lists this warning:
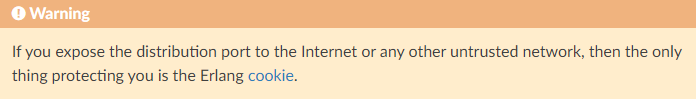
Alex Vandiver found this critical vulnerability in Apache CouchDB and Apache CouchDB outlines the privilege escalation vulnerability:
An attacker can access an improperly secured default installation without authenticating and gain admin privileges.
- CouchDB opens a random network port, bound to all available interfaces in anticipation of clustered operation and/or runtime introspection. A utility process called epmd advertises that random port to the network. epmd itself listens on a fixed port.
- CouchDB packaging previously chose a default cookie value for single-node as well as clustered installations. That cookie authenticates any communication between Erlang nodes.
Systems Affected and Detection
Apache CouchDB versions 3.2.1 and below are affected. Tenable Nessus’s plugin Apache CouchDB < 3.2.2 Remote Privilege Escalation can be used to detect this vulnerability.
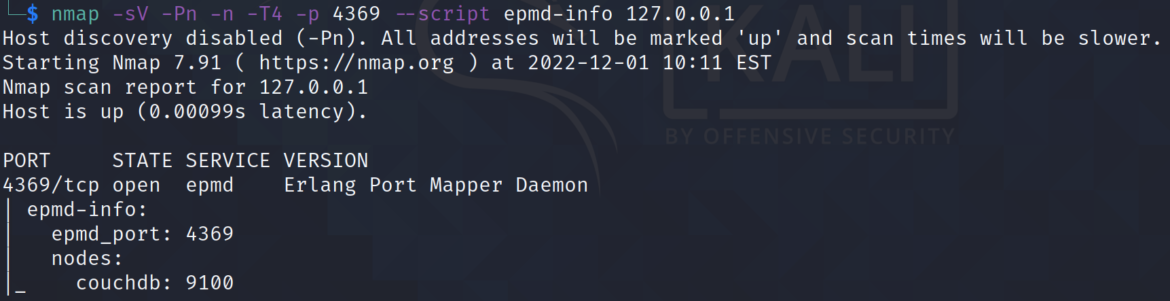
HackTricks shows that the Nmap script epmd-info can be used to check to see if the Erlang port mapper daemon (epmd) is accessible: nmap -sV -Pn -n -T4 -p 4369 –script epmd-info
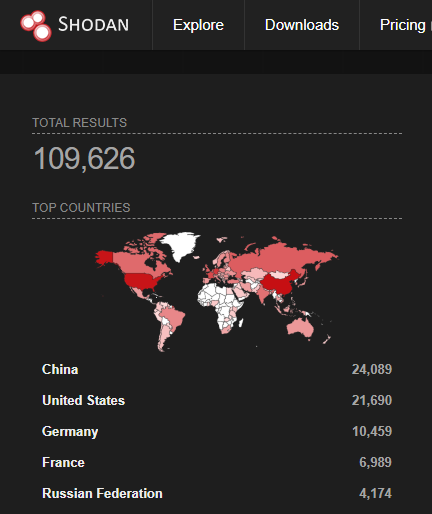
HackTricks also notes that Shodan.io can be used to see the scope of vulnerable CouchDB servers: port:4369 product:”Erlang Port Mapper Daemon”
Exploitation
After detecting the couchdb service on port 5984, nmap can be used to see if the Erlang port mapper daemon is open on port 4369.
nmap -sV -Pn -n -T4 -p 4369 –script epmd-info
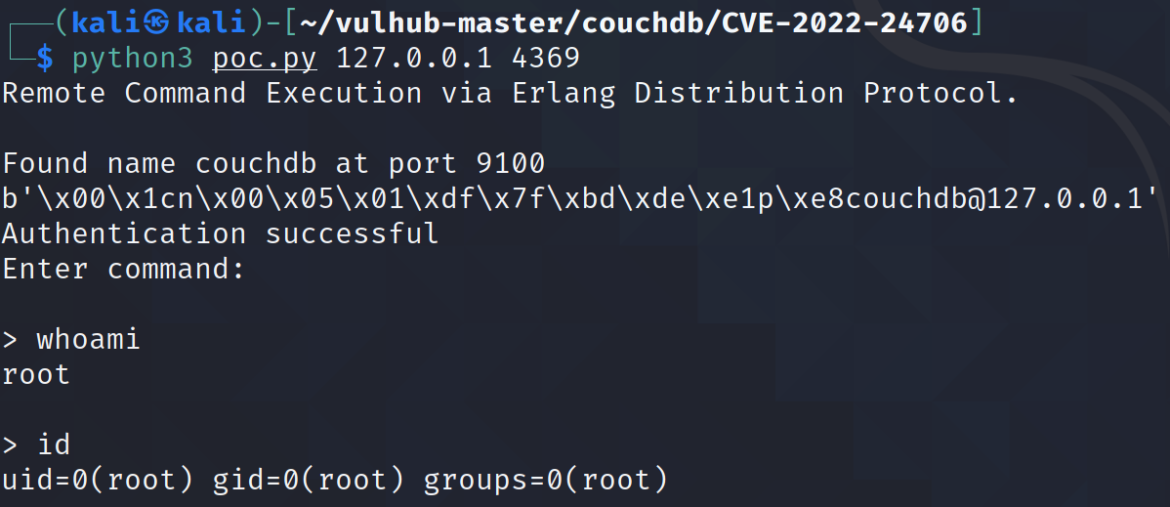
If the epmd port is open and the default cookie value of “monster” is set, attackers can use Konstantin Burov’s (Github @_sadshade) exploit on Github. (Always read through public exploits before running) Github’s Vulhub repository can also be used to set up a vulnerable environment and run the exploit:
The cookie is usually named “.erlang.cookie” and may be seen by running:
ps aux command with a grep search for –setcookie, couchdb, monster
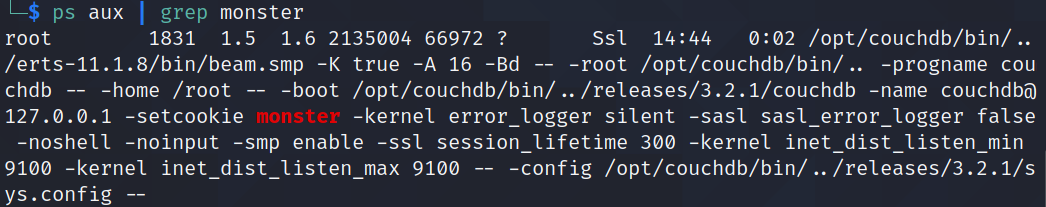
If an attacker knows the cookie, Metasploit also has an exploit module, erlang_cookie_rce, that targets the erlang port mapper daemon.
Remediation
Upgrading to CouchDB 3.2.2 or later fixes this vulnerability. Apache also recommends a firewall in front of all CouchDB installations, with only port 5984 exposed. Apache CouchDB explains that CouchDB 3.2.2 and onwards will not have default erlang cookie values of monster. Newer CouchDB versions also bind epmd and the CouchDB distribution port to 127.0.0.1 and/or ::1.
CouchDB also has instructions on proper CouchDB cluster set up here.
References:
- https://docs.couchdb.org/en/stable/cve/2022-24706.html
- https://nvd.nist.gov/vuln/detail/CVE-2022-24706
- https://github.com/sadshade/CVE-2022-24706-CouchDB-Exploit
- https://docs.couchdb.org/en/stable/setup/cluster.html
- https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/multi/misc/erlang_cookie_rce

