Latest News & Articles

Secured™ Receives 8(a) Certification from the Small Business Administration
Secured™ is proud to announce that we have received 8(a) certification from the U.S. Small Business Administration (SBA) and Veteran

Finance By Day, Fiction By Night: Brandon Thomson’s Journey at Secured™
At Secured™, employees are more than just cogs in the machine—they’re valued members of a family, each bringing their unique

Secured™ Announces the Appointment of Kristie Bender-Carey as CEO Finance
Secured™ proudly announces the appointment of Kristie Bender-Carey as CEO Finance, bringing her extensive experience in finance and strategic growth
Security Resources
CISA's Known Exploited Vulnerabilities Catalog

Minimize Cybersecurity Risk with the Known Exploited Vulnerabilities (KEV) Catalog
In November 2021 the Cybersecurity and Infrastructure Security Agency (CISA) started the Known Exploited Vulnerabilities (KEV) Catalog and Binding Operational Directive 22-01. The KEV catalog lists only vulnerabilities known to be actively exploited.

KEV Catalog: OpenSMTPD RCE Vulnerability (CVE-2020-7247)
CVE-2020-7247 is a remote code execution vulnerability in OpenSMTPD. OpenSMTPD is a free smtp protocol (mail server protocol) that runs
KEV Catalog: “Shellshock” GNU Bash Arbitrary Code Execution Vulnerability (CVE-2014-6271, CVE-2014-7169)
The “Shellshock” or “Bashdoor” vulnerability is a critical remote code execution vulnerability.
Active Directory Series

Active Directory Series: Introducing AD CS
This post introduces Active Directory Certificate Services (AD CS) and topics like: public key infrastructure (PKI), the Kerberos pre-authentication protocol PKINIT, Certificate Signing Requests (CSR), and templates. This overview provides a baseline for learning AD CS penetration testing.
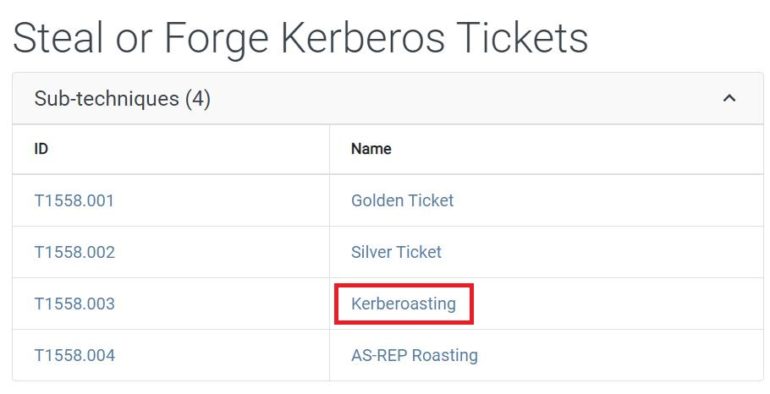
Active Directory Series: Kerberoasting
Kerberoasting is an Active Directory credential attack that attackers use to access other services in Active Directory environments. This post

Active Directory Series: Kerberos Authentication Overview
Active Directory uses the Kerberos protocol to authenticate clients and permit or deny access to different services like mail, databases
