Latest News & Articles

Secured™ Receives 8(a) Certification from the Small Business Administration
Secured™ is proud to announce that we have received 8(a) certification from the U.S. Small Business Administration (SBA) and Veteran

Finance By Day, Fiction By Night: Brandon Thomson’s Journey at Secured™
At Secured™, employees are more than just cogs in the machine—they’re valued members of a family, each bringing their unique

Secured™ Announces the Appointment of Kristie Bender-Carey as CEO Finance
Secured™ proudly announces the appointment of Kristie Bender-Carey as CEO Finance, bringing her extensive experience in finance and strategic growth
Security Resources
CISA's Known Exploited Vulnerabilities Catalog

Minimize Cybersecurity Risk with the Known Exploited Vulnerabilities (KEV) Catalog
In November 2021 the Cybersecurity and Infrastructure Security Agency (CISA) started the Known Exploited Vulnerabilities (KEV) Catalog and Binding Operational Directive 22-01. The KEV catalog lists only vulnerabilities known to be actively exploited.

KEV Catalog: “SMBGhost” Microsoft SMBv3 Remote Code Execution Vulnerability (CVE-2020-0796)
“SMBGhost” is a critical vulnerability that affected SMBv3 in Windows 10 Versions 1903 and 1909. The vulnerability is an integer

KEV Catalog: “HiveNightmare” aka ”SeriousSAM” Vulnerability CVE-2021-36934
CVE-201-36934 is called Microsoft Windows SAM Local Privilege Escalation Vulnerability and is also known by the nicknames “HiveNightmare” or “SeriousSAM”.
Active Directory Series

Active Directory Series: Introducing AD CS
This post introduces Active Directory Certificate Services (AD CS) and topics like: public key infrastructure (PKI), the Kerberos pre-authentication protocol PKINIT, Certificate Signing Requests (CSR), and templates. This overview provides a baseline for learning AD CS penetration testing.

KEV Catalog: “sAMAccountName” “noPac” Privilege Escalation (CVE-2021-42278 and CVE-2021-42287)
“sAMAcountName” and “noPac” are two critical Active Directory vulnerabilities that can lead to full Domain compromise. Learn how a dollar

Active Directory Series: DC Sync
DC Sync attacks are a serious threat to Active Directory environments. DC Sync attacks occurred in the SolarWinds compromise in

Secured™ Takes Aim To Support Veterans As “Top Gun” Sponsor of BCV’s Annual Helicopter Hog Hunt Weekend
We were proud to sponsor this year’s Big Country Veterans’ (BCV) Helicopter Hog Hunt Weekend, as well as honor a
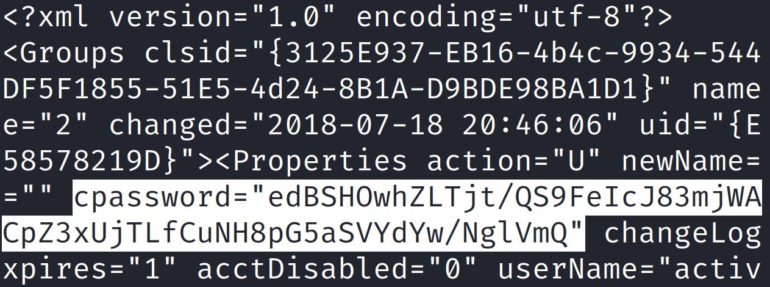
7 Locations for Unsecured Credentials
Attackers can use unsecured user credentials to access different services and pivot within a network. Malicious actors and penetration testers
Dallas County Data Incident from Computers Sold at Auction
Last month, Dallas County released a notice disclosing that Dallas County computers were sold at auction that did not have

Ferrari Cyber Incident: Cyber Extortion vs Ransomware
Last week, Ferrari announced it was contacted by a cyber threat actor for a ransom demand. Their corporate response to

CISA Announces Ransomware Vulnerability Warning Pilot
Last week, Monday March 13, CISA announced the creation of the Ransomware Vulnerability Warning Pilot (RVWP). This program was launched

Introducing and Setting Up the New Kali Linux 2023.1: Kali Purple
Today, Kali Linux’s 10-year anniversary, Kali Linux released their newest Kali Linux version: Kali Purple. Kali Linux is known for
