Latest News & Articles

Secured™: The Official Cybersecurity Partner of Skull Games
Secured™ has announced its bronze-level corporate sponsorship and official cybersecurity partnership with Skull Games, a nonprofit organization dedicated to combating

Unveiling the Tools Behind Object Recognition: A Deep Dive into Deep Learning Equipment
Discover the cutting-edge tools and technologies powering object recognition systems. From sophisticated hardware to advanced software frameworks, learn how these

Looking Back on 10 Cybersecurity Trends of 2023
This list of trends highlights the dynamic and complex nature of cybersecurity we faced in 2023, underscoring the need for
Security Resources
CISA's Known Exploited Vulnerabilities Catalog

Minimize Cybersecurity Risk with the Known Exploited Vulnerabilities (KEV) Catalog
In November 2021 the Cybersecurity and Infrastructure Security Agency (CISA) started the Known Exploited Vulnerabilities (KEV) Catalog and Binding Operational Directive 22-01. The KEV catalog lists only vulnerabilities known to be actively exploited.

KEV Catalog: OpenSMTPD RCE Vulnerability (CVE-2020-7247)
CVE-2020-7247 is a remote code execution vulnerability in OpenSMTPD. OpenSMTPD is a free smtp protocol (mail server protocol) that runs
KEV Catalog: “Shellshock” GNU Bash Arbitrary Code Execution Vulnerability (CVE-2014-6271, CVE-2014-7169)
The “Shellshock” or “Bashdoor” vulnerability is a critical remote code execution vulnerability.
Active Directory Series

Active Directory Series: Introducing AD CS
This post introduces Active Directory Certificate Services (AD CS) and topics like: public key infrastructure (PKI), the Kerberos pre-authentication protocol PKINIT, Certificate Signing Requests (CSR), and templates. This overview provides a baseline for learning AD CS penetration testing.
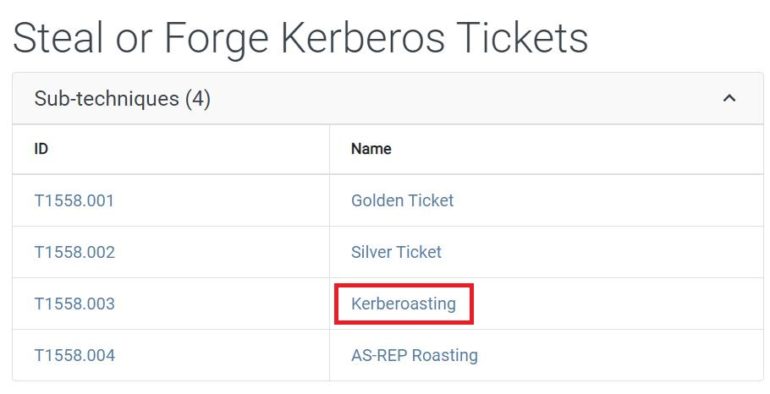
Active Directory Series: Kerberoasting
Kerberoasting is an Active Directory credential attack that attackers use to access other services in Active Directory environments. This post

Active Directory Series: Kerberos Authentication Overview
Active Directory uses the Kerberos protocol to authenticate clients and permit or deny access to different services like mail, databases
